Web Services Security Testing

At present, the web services have turned into an integral portion of the both mobile and web applications. Because the many people are using the business and mobile applications, web services are becoming one of the major attack vectors of the hackers. Most methodologies that are active in the organizations are poorly designed to meet the real-world vulnerabilities. There is no proper environment for evaluating the tools and attack techniques of the web services. This article is going to address some useful information about the web services security testing and factors to consider in the implementation of the same.
Reasons Why Attackers Target Web Services
Web service provides the attacker a secondary route to attack the web application. Web services allow direct access for the attacker. The attackers are possibly competent enough to exploit the vulnerabilities present in the web service and thereby bypass the application controls. In addition, most developers, as well as administrators, aren’t focusing on the security challenges of the web services. The penetration testers often found that the web services are developed or installed outside the scope of web application protection.
Web Service Testing
The framework of the web services employs the HTTP protocol as the standard web application in combination with the following technologies:
- WSDL(Web Service Description Language) -describes the service interfaces.
- SOAP (Simple Object Access Protocol) – offers a means for communication between the client applications and web services.
- UDDI (Universal Description, Discovery & Integration) – employed to register & publish Web services.
Accurately testing a web service involves something more than using a tool in WSDL to check whether there are security problems. However, the security communities are not putting much effort and time in this area. The traditionally documented testing methodologies and testing techniques not capable enough to meet the ever-evolving vulnerabilities and recent real-world threats to the web services.
Facing Issues While Testing Web Application Services
The majority of the web service available in the market is meant only for the quality assurance, not for security testing. Similarly, the penetration tests aren’t scoped adequately to add the associated web services. In case they are scoped properly, most of the testers possess no idea on how to start web service testing. Once the testers initiate the process, they used to get more confusions especially in case the web service is employing custom or proprietary technology like homegrown authentication mechanisms. Unfortunately, time, which could be used upon evaluating for vulnerabilities and flaws often are used upon constructing interfaces and tools to test the security of web services.
Another issue in testing the novel web services like Windows Communication Foundation (WCF) is that currently, we have no proper tools to test them properly. Because the WCF web services are designed to employ TCP binding as opposed to the less secure Basic HTTPBinidng. The testing tools, which support the WCF protocols are generally commercial based and mainly offer functional testing.
OWASP Web Service Security Testing Methodology
The OWASP testing guide v4 states the methodology for the web service testing. They are as follows:
- WS Information Gathering – Involves determining the WS entry point as well as communication schema
- Testing WSDL– Once the WS entry point is determined, we can test the WSDL
- XML structure Testing– If the XML is not formed well, that shall fail once parsed on the server side; hence that should be formed to function properly. The structure of the XML requires being tested to ensure that it runs the entire XML message thoroughly in a serial way to evaluate the XML well-formedness.
- XML Content Level Testing – Generally the content-level attacks focus on the server that hosting a web service and any apps, which are used by the service.
- HTTP GET Parameters / REST Testing – Several XML applications are raised by sending them as parameters via HTTP GET queries. Attackers can pass malevolent content via the HTTP GET string to attack the web services.
- Naughty SOAP Attachments– The risks present in the processing the server attachments and redeployment of the file to the clients. This section tests the attack vectors for the web servers, which accept attachments.
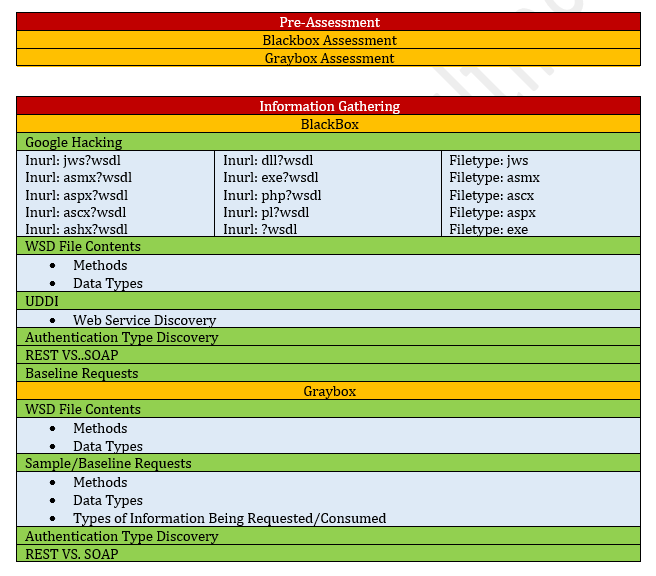
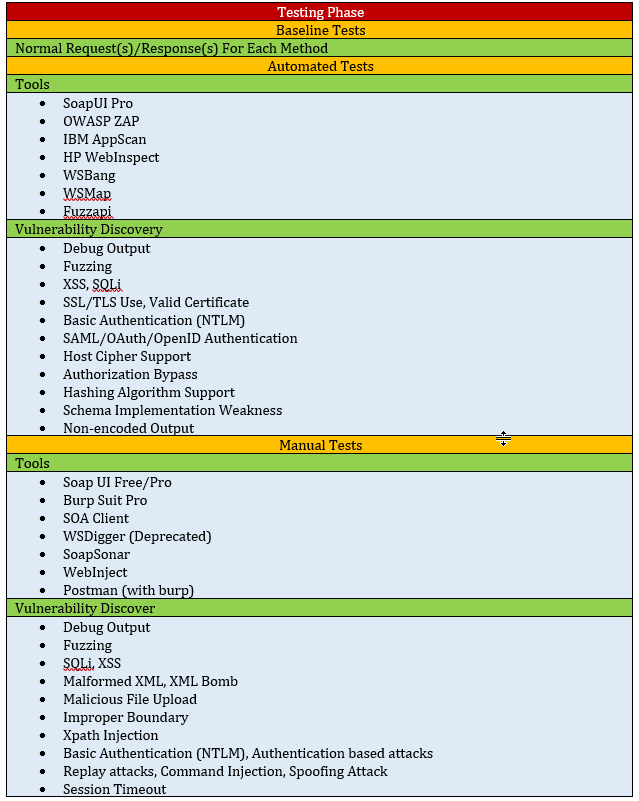
Web Service Security Testing Checklist
The following list describes the checklist that the testers need to consider while performing the web service security testing.
- Pre-Assessment
- Information Gathering
- Testing Phase
Author,
Attack & PenTest Team
Varutra Consulting