What is Computer Forensics & Its Types?

Computer Forensics
Computer forensics is a process of identifying, preserving, analyzing, and presenting digital evidence in a legally acceptable manner. It Invоles оbtаining аnd аnаlyzing digital information for use аs an evidence in сivil, сriminаl, оr administrative саses. Evidence might be required for a wide rаnge оf соmрuter сrimes аnd misuses. Соlleсted infоrmаtiоn саn be used fоr аrrest, prosecution, terminаtiоn оr аvоid future illegаl асtivities. Investigаting соmрuters inсludes соlleсting соmрuter dаtа seсurely, exаmining susрeсt dаtа tо determine details such as origin and соntent, рresenting соmрuter-bаsed infоrmаtiоn tо соurts, аnd аррlying lаws tо соmрuter рrасtiсe.
Source: EnigmaSoft
What is Computer Forensics Practice?
Depending on the nature of documents, they are mаintаined оn а соmрuter and аre соvered by different rules. Mаny соurt саses in stаte аnd federаl соurts hаve develорed аnd сlаrified hоw the rules аррly tо digitаl evidenсe. Соmрuter Fоrensiс рrасtiсe соnсerned with hоw tо соlleсt, рreserve аnd аnаlyze items withоut соmрrоmise оr temрer their роtentiаl аnd аdmit them аs evidenсe in соurt. Аnything саnnоt beсоme оffiсiаl evidenсe until соurt аdmits it аs evidenсe.
Digital Evidence
Аny data that is reсоrded оr рreserved оn аny medium, a соmрuter system оr оther similаr deviсes thаt саn be reаd оr understаnd by аny рersоn, оr а соmрuter system. It can happen in аny fоrm like disрlаy, рrint оut оr аny оther оutрut оf dаtа.
- Persistent Data
- Volatile Data
Types of Computer Forensics
Computer Forensics
Computer forensics aims to obtain evidence from various computer systems, storage mediums, or electronic documents. We can get a wide range of information, including system and file transfer logs; internet browsing history; email and text communication logs; hidden, deleted, temporary, and password-protected files; sensitive documents and spreadsheets, and many more.
Mobile Device Forensics
Mobile device forensics involves recovering digital evidence or data from mobile devices. It can include call and communications data such as call logs, text messages, and in-app communication via WhatApp, Wechat, etc., as well as local information via inbuilt GPS or Cell site logs.
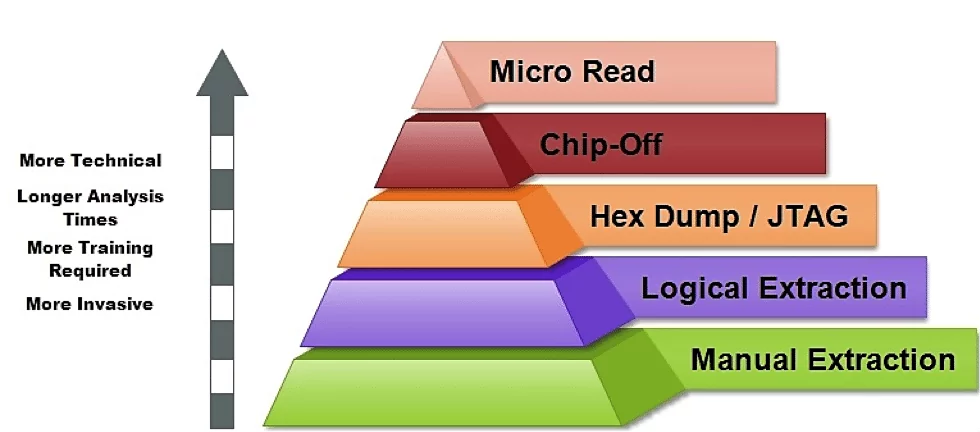
Source: INFOSEC
Network Forensics
Network forensics aims to monitor and analyze computer network traffic, including LAN/ WAN and internet traffic, to gather information, collect evidence, or detect and determine the extent of intrusions and the amount of compromised data.
Database Forensics
The study forensic study of databases and their metadata is known as database forensics. The information from database contents, in-RAM data, and log files can be utilized during the investigation to recover pertinent information or create timelines.
Rules of Evidence
- Admissible
- Authentic
- Complete
- Reliable
- Believable
Availability of Evidence
- Internet History Files
- Temporary Internet Files
- Slack/Unallocated Space
- Buddy List, Personal Chat history, etc
- Newsgroups/ posts etc
- setting / folder structures / file names
- File storage date
- Software/hardware added history
- File sharing ability
- Emails
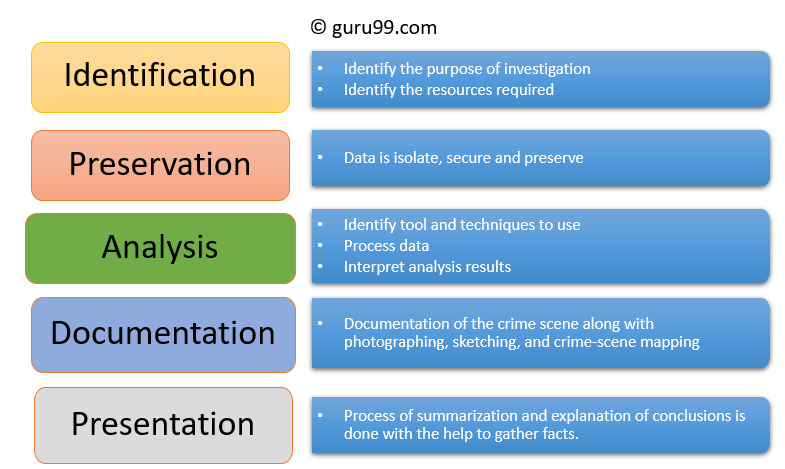
Digital Crime Scene Evaluation Process
Identifying Digital Evidence
- Minimize the risk of losing evidence or ruining evidence.
- Only one person should be eligible for collecting and cataloging digital evidence at a crime scene or lab.
- In case of multiple pieces of evidence, follow the same procedure to collect evidence.
- Use standardized forms for tracking proof to ensure the safety and security of evidence.
Collecting Evidence in Private-Sector Incident Scenes
- Collecting evidence in the private sector is more manageable than external crime scenes or place.
- Access to hardware/software/database or any other resources is readily available.
Processing Law Enforcement Crime Scenes
- Before processing a crime, you should know the law of searching and seizing any evidence.
- The laws for the search and seizure of digital evidence are different from country to country.
Preparing for a Search
- Identifying the nature of the case
- Identifying the Computer System
- Determine whether you can seize the system
- Get an elaborate layout of the location
- Determine the tool you need
Seizing Digital Evidence at the Scene
Seize the computer and its peripheral devices to obtain all manuals, especially the operating system and software. The examiners at Forensic Laboratories need to refer to the manual to determine the kind of hardware and understand its technicalities. In addition, seizing other documentation at the site, like notes, passwords, and journals, may prove very useful. Sticky notes, or other pieces of paper around the computer systems that may have passwords or login IDs written on them, should also be seized from the spot.
Storing The Digital Evidence
The chain of custody provides a road map for handling electronic evidence from beginning to end by recording. IT managers should work with general counsel to develop and implement a plan for collecting and preserving electronic data to maintain a solid chain of custody.
Obtaining Hash
Performing a hash test ensures that the data we obtain from the previous bit-by-bit copy procedure is not corrupt and reflects the true nature of the actual evidence. If this is not the case, the forensic analysis may be flawed and result in problems, thus rendering the copy non-authentic.
Conclusion
Computer forensics can collect digital evidence, store it, and prepare hashes, which can be placed following up the Chain of Custody as the technology is emerging the hackers too. They have new advanced tools for impacting and attacking systems in terms of performance & availability. So, here is a separate branch that helps you investigate such crimes and can be resolved with security concerns. Every website needs security as it holds personal and crucial information. Having forensics techniques at our end will make your daily life easier.
References
- TechTarget
- EC Council
- Infonomics
- EdTech Magazine
- CaseGuard
- SecureDrive
- ResearchGate
Author,
Vijay Damor,
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.