The Importance of Zero Trust Network Access (ZTNA) in Healthcare

There has been a significant increase in data breaches worldwide in all industries, and the healthcare industry is no exception. Critical Insight’s 2021 healthcare data breach report stated that breaches have increased by 84% after the pandemic. In addition, it resulted in an all-time high number of healthcare data breaches reported by the Human Services Office for Civil Rights (OCR). In addition, ransomware attacks have increased in the healthcare industry. According to the Sophos State of Ransomware in Healthcare 2022 report, 94% of ransomware attacks on the healthcare sector over a year. Also, 66% of healthcare organizations were hit by ransomware in 2021.
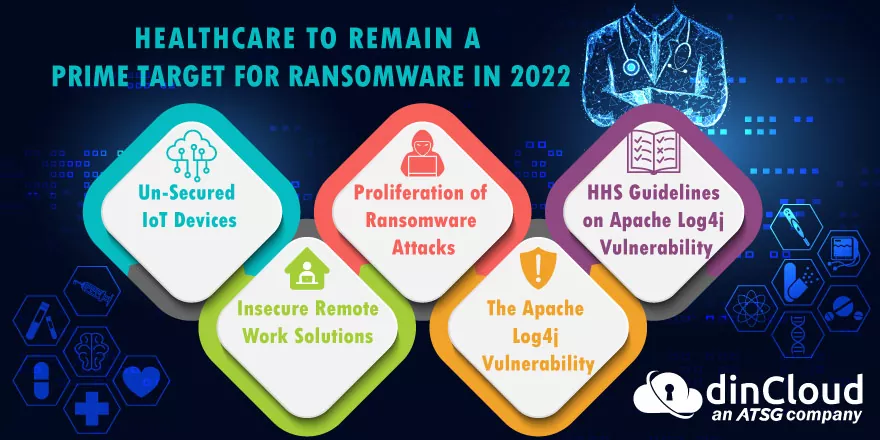
Also, 61% of such attacks primarily result in data encryption. It makes the information inaccessible until the ransom is paid or the data is restored to their systems. Such attacks can cause severe damage to the patient and their safety. Today healthcare is also about securing the patient’s sensitive information rather than providing adequate medical attention to the patients. They not only have to comply with several industry regulations regulating the use of PHI (protected health information), which includes HIPAA (Health Insurance Portability and Accountability Act), but also access and authentication complexities.
Data Breaches in Healthcare Industry
Industries are moving to cloud-based services and augmenting remote health monitoring, IoMT devices, telehealth, portable medical devices, and more in their IT infrastructure. However, it also increases the surface attack area and makes the healthcare sector one of the most vulnerable sectors and a target of ransomware attacks. Recently, a lawsuit stated the first-ever allegations of patient death due to a ransomware attack.
In any healthcare organization’s network, many valuable PHI, medical equipment, and refrigerators containing several life-saving vaccines are stored. And when a network gets hacked, it can cause a lot of damage to the entire healthcare institution. Most healthcare institutions use traditional perimeter-based security for their infrastructure, but because of its unrestricted access and inherent trust, it becomes vulnerable to numerous cyber-attacks. Also, the permitter boundaries are getting blurred, and all thanks to the remote care options, perimeter-centric security is becoming immensely vulnerable.
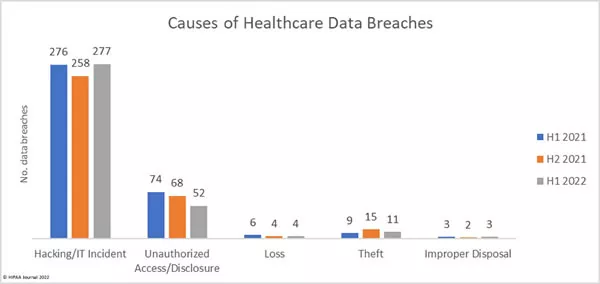
Source: HIPAA Journal
For such a situation, healthcare institutions should look for security means to protect the entire network completely. Zero Trust Network Access (ZTNA) provides seamless protection to the whole network infrastructure by verifying user authentication, device and policy accessibility, and then giving access limited to a specific system or applications only and not the complete network. In addition, ZTNA helps in preventing compromised devices from getting connected to other applications and devices. It contains the network’s lateral movement and cyberattacks like ransomware from getting onto the network.
What is ZTNA (Zero Trust Network Access) & How Does It Work?
ZTNA or Zero Trust Network Access is a security solution that provides security to applications outside the organization’s premises through its limited access control policy. It is very different from VPNs (Virtual Private Networks) as they grant users access to the entire network. In contrast, ZTNA only provides limited network access after verifying the authentication of the users.
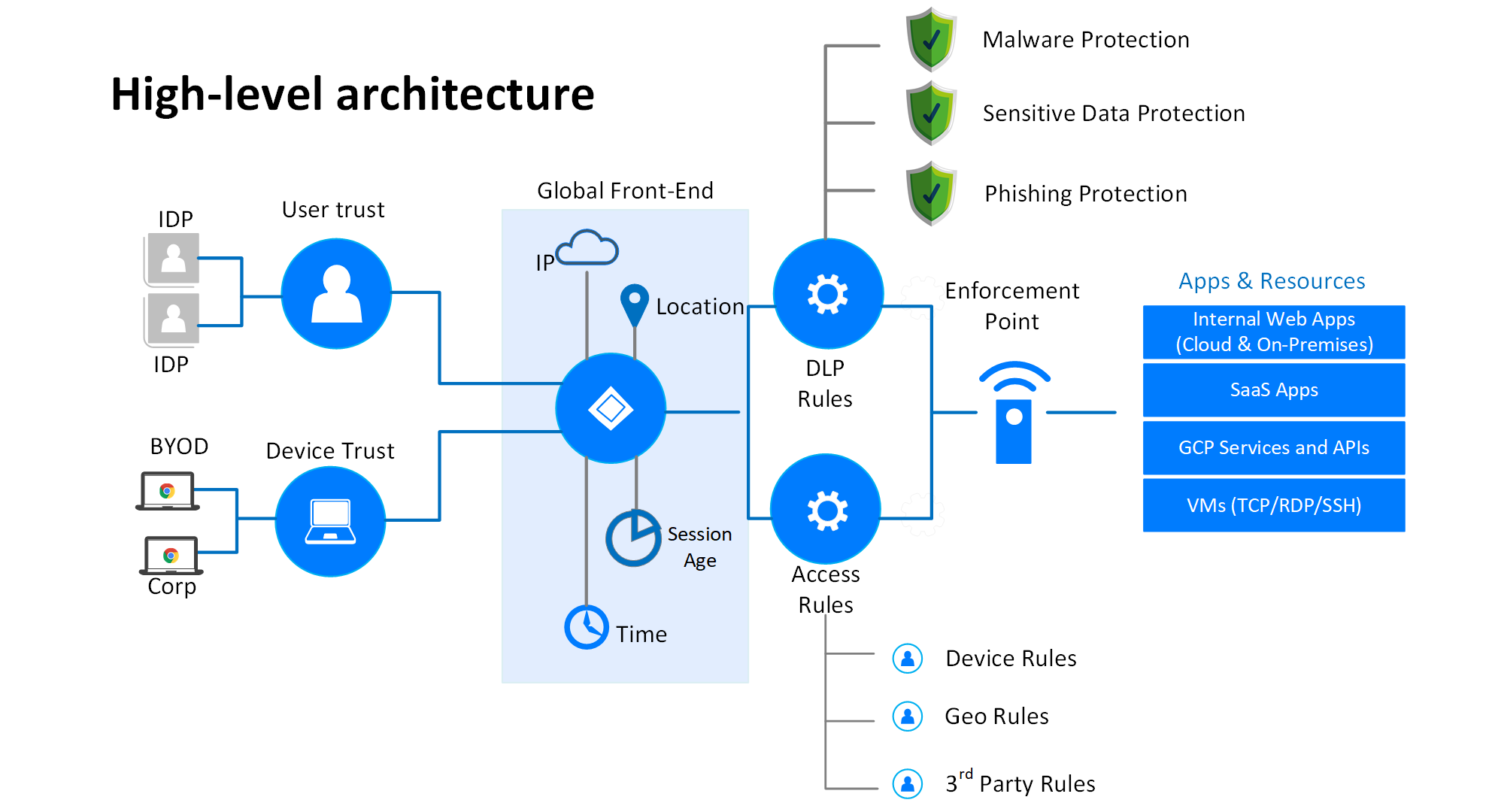
Source: Netify
ZTNA only provides access to specific applications or resources after validating the user’s authentication. After validation, the user to the ZTNA service then grants user access using a well-protected encrypted tunnel. It offers an additional protection layer preventing the applications from getting exposed to IP addresses that would be otherwise visible. It means ZTNA acts like SDPs (software-defined parameters), following the idea of dark cloud by preventing the users from having visibility of any other applications whose access permission they do not have. It is also helpful in a scenario where attackers have gained access to any application, and they will not be able to scan or locate other applications in the network.
Benefits of Integrating ZTNA in Healthcare Organizations
ZTNA is the fastest and most secure way to connect users, applications, and devices to the healthcare network. Most applications are now available in cloud environments, or multiple applications reside on various clouds and on-premises. ZTNA offers only limited access to users depending upon their requirements. This way, the other critical information or applications are not exposed, and the chances of getting attacked reduce. This model defines nothing or no one can be trusted until they are proven trustworthy. The trust is built through the authentication and the validation of the user device posture via location, IP address, context, etc. It results in a more secure and flexible environment with better monitoring. The primary attributes of ZTNA that apply to healthcare organizations are:
- Provides an extra layer of security preventing network-level threats.
- Access is only allowed after proper verification and authentication.
- It is an entirely cloud-based operation that works across every geological area, enabling autoscaling.
- The applications and services associated with the healthcare organization are constantly monitored.
- Outstanding user experience while eliminating privacy concerns and backhauling.
ZTNA seamlessly integrates with the healthcare network providing security while constantly sharing any data, automatically isolating any compromised device or application, and preventing any threats from data stealing.
Reference:
Sophos
VMware
Citrix
NordLayer
HealthITSecurity
Author,
Sanjana Yadav,
Marketing Department
Varutra Consulting Pvt. Ltd.




