7 Top Trends in Cybersecurity for 2022

The world is getting accustomed to digitalization, and the organization’s digital footprint is trending in cybersecurity for 2022. In short, these trends focus on:
- How to remodel the security stack to adequately address new sophisticated cyber threats and risks.
- Reforming the organization’s security posture by pushing cybersecurity decision-making.
- Replan and develop the best practices for managing cyber threats better.
As the organization’s digital footprint expands, the security executives encounter a strong contingency, and centralized cybersecurity control becomes outmoded. In addition, the hybrid work module and integration into the cloud have opened the door to new risks. The emergence of sophisticated ransomware, digital supply chain attacks, and deeply ingrained vulnerabilities exposes the gaps in technology.
7 Top Trends in Cybersecurity For 2022
Here are the top 7 trends in cybersecurity for 2022 that will address new security risks and assist in evaluating, replanning, and preparing on how to respond to the latest sophisticated and evolving threats.
Trend No. 1: Expansion of Attack Surface
Around 60% of employees are currently working remotely. There are chances that approximately 18% of employees are likely to return to the office. This work shift has led to an increased usage of cloud services, association with supply chains, and the use of cyber-physical systems or intelligent systems has raised the possibility of exposing new attack surfaces.
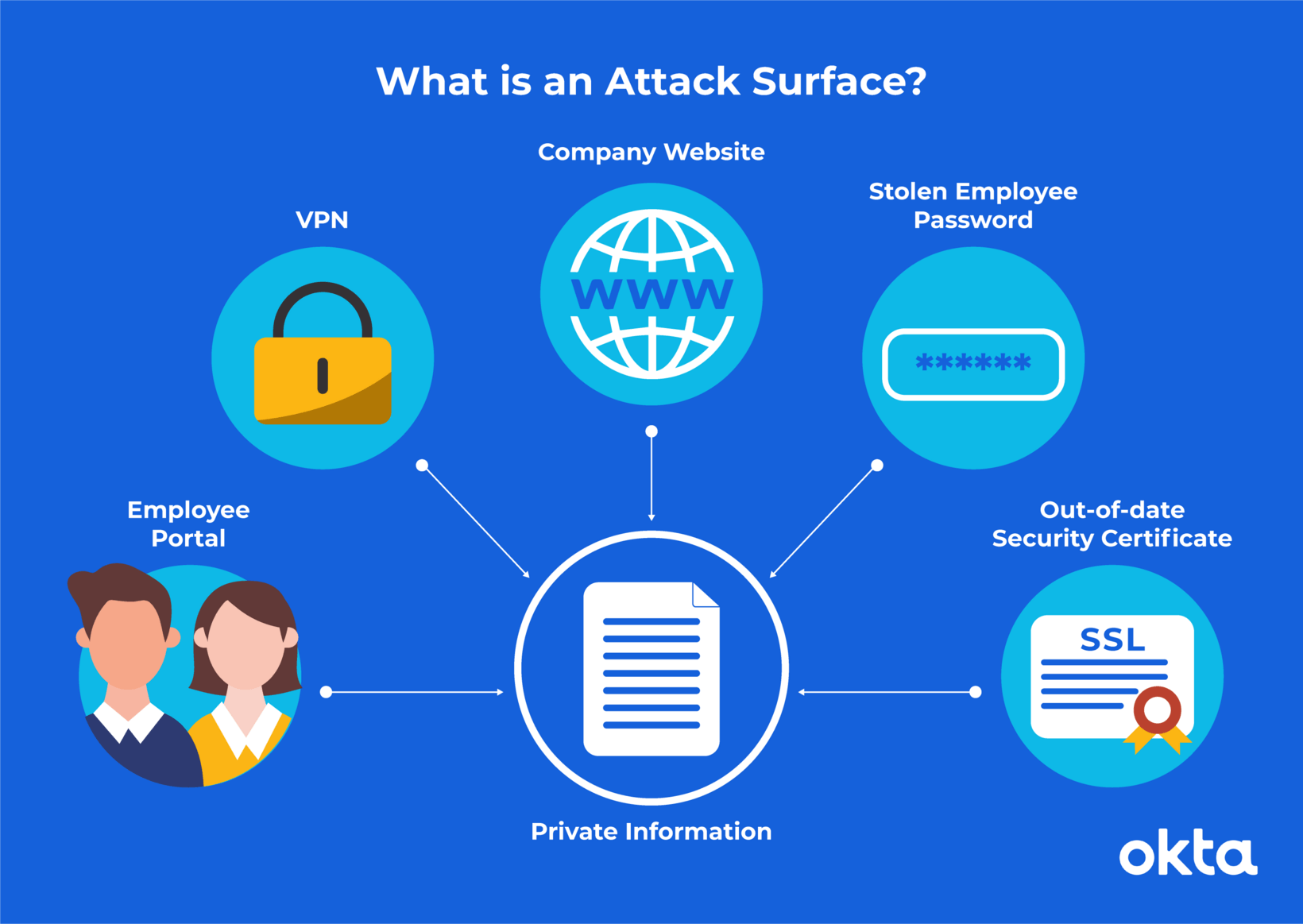
Source: Okta
Definition of the attack surface is the number of all attack vectors or possible points where an unauthorized user can access the system and extract data. It is said that the smaller the surface, the easier it is to protect the data. Therefore, organizations should regularly monitor the attack surface to identify threats and work on reducing their attack surface as it tends to get tricky because of digitalization. It often leaves the organization more vulnerable. It is recommended that the organization start thinking about a new and modern approach rather than just following the traditional method. It will help them with better security monitoring, identifying, and responding to cyber threats.
Trend No. 2: Defending Identity Systems
Identity systems come under sustained attack. By gaining access to the user’s credentials, attackers can access the system. It is the primary means to achieve the goals. For instance, in the SolarWinds breach, the hackers gained access by using the supplier’s privilege access to penetrate the target network.
According to a CrowdStrike Overwatch team report, eight out of ten breaches are identity-driven. These identity-driven attacks are pretty hard to detect. When an authentic user’s credential is compromised, it can be challenging to detect the hacker using the traditional security approach. Identity security is often seen as the last line of defense. It is suggested that the organizations work on the identity threat detection and response (ITDR) to protect and defend against the identity system.
Trend No. 3: Digital Supply Chain Threats and Risks
Gartner has predicted that by 2025, around 45% of the organizations will encounter supply chain attacks, a nearly three-fold increase from 2021. By attacking the digital supply chain, attackers get a high return as vulnerabilities spread through the supply chain, making it easier for the attacker to make more profits. Therefore, the digital supply chain threats require a new mitigation approach with a more calculated risk-based vendor who can analyze, manage and carry out best security practices. One of the best practices for the supply chain is to shift to resilience-based ideas by evaluating the critical infrastructure and developing a Plan B for any dire situation.
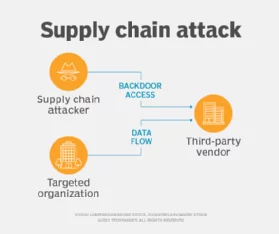
Source: TechTarget
Trend No. 4: Consolidating Vendors
Several security applications and products are forthcoming, and vendors are integrating multiple security functionalities into a single platform. In addition, they are introducing licensing and suitable pricing options to make the package look more attractive. Consolidating is a trend that decreases complications by cutting costs, improving efficiency, and providing better security. Though it reduces the negotiating power and seems challenging, it produces better results.
Trend No. 5: Cybersecurity Mesh
A cybersecurity mesh (CSM) is a modern approach to security infrastructure which enables the distributed enterprises to expand and coordinate with different security assets while they are off-premises or on-premises. It allows you to manage your systems like network security devices, perimeter firewalls, and security software in isolation. CSM helps secure the access points and assures that there are no pre-recorded cases of data leakage or known or unknown breaches. It has a lot of advantages, as it helps in real-time attack detection and creates a flexible security posture. Gartner has predicted that by 2024, there will be a reduction in the financial impact of distinctive security incidents by 90% for the organizations adopting cybersecurity mesh.
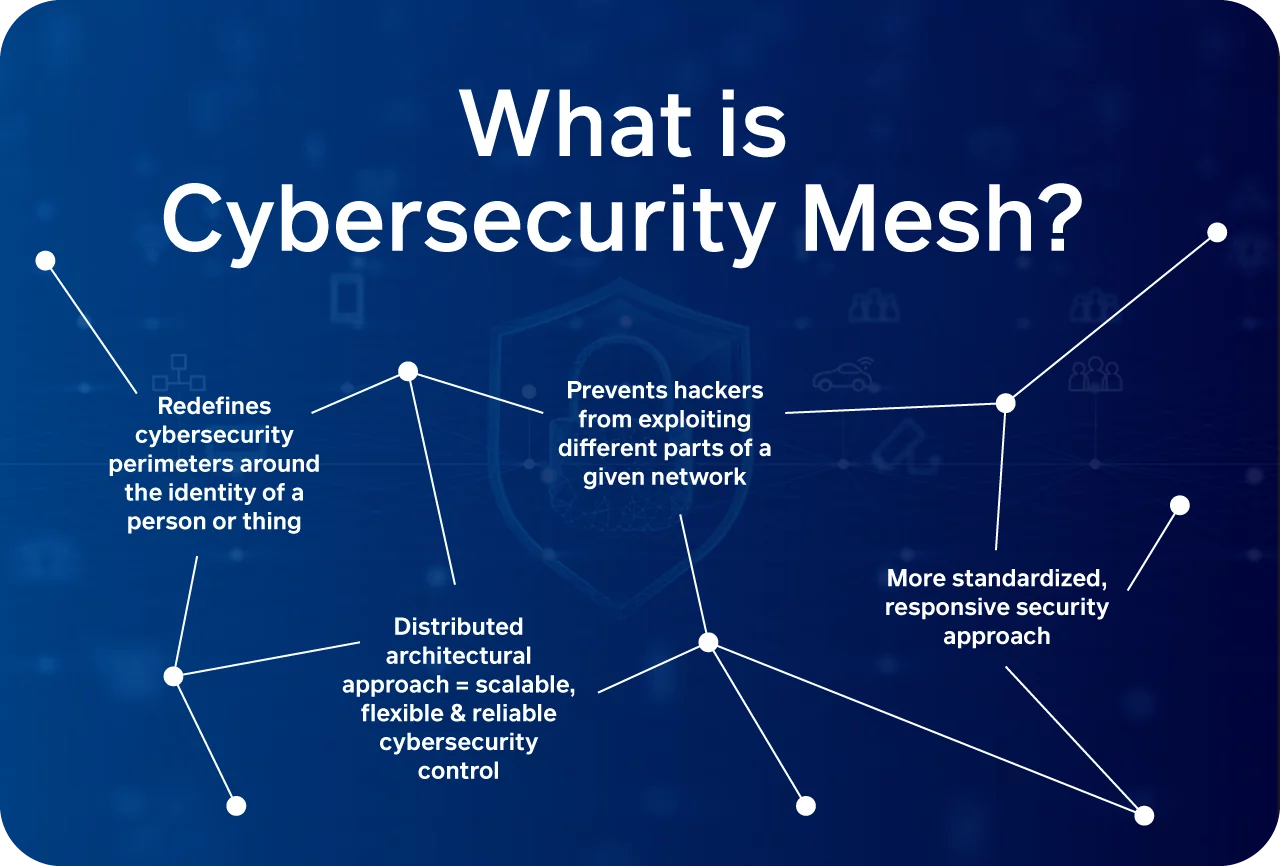
Source: Stefanini Group
Trend No. 6: Distributed Decisions
The leaders and executives in the organizations need to be fast-paced and quick to understand the cybersecurity functionalities and provide their support to the priorities regarding digital business. As the companies are now getting digitalized, the work is too much for a centralized CISO role. Several organizations are designing the CISO office to facilitate cyber judgment. However, the centralized function and CISO will continue to set policies while the leader who is placed in the parts of the organization will continue to decentralize security decisions.
Trend No. 7: Beyond Awareness
Human beings are bound to make an error, but sometimes these human errors can be fatal. It can even result in data breaches, proving the security awareness program can never be 100% effective. As a result, organizations are moving beyond the old compliance-based awareness programs and contributing toward comprehensive practices. These sophisticated development programs are designed to create more secure ways of working.
No organization is completely immune to attacks. However, they primarily focus on preventing and mitigating attacks. In other words, their main focus is to monitor and quickly identify the attacks and respond to them quickly. It means they should start thinking about what’s more to security other than the traditional practices and awareness of better secure means of working.
Conclusion
Cybersecurity attacks are evolving, and no one knows what the future holds for everyone. Organizations are busy fortifying their networks and systems against uncertainties and unknowns. These top trends in cybersecurity will help them gain insights on how to work and prepare themselves for the ambiguity of the future. In addition, it will help the organizations improvise their cybersecurity measures and protect their assets.
Reference
Gartner
Fortinet
CrowdStrike
TechRepublic
DXC Technology
FinancesOnline
Simplilearn
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




