All About DoS And Its Preventive Measures
When a shop is over crowed and not possible to enter, waiting for some space can make fell bad impression on the shop and next time may possible the same customer can avoid that shop from his past experience and shop keeper can lose a customer. The same things happen in Denial of Services attack.
It’s one of the cyber-attacks in which attackers seek to make machine or network resources unavailable to its genuine users by super flooding request to machine to overload the systems. If the request is from the single IP is called Denial of Services, if the request from multiple IP and location called Distributed Denial of Services.
Between 11th February 2023 to 12th February 2023, Cloud flare, a web infrastructure and security firm, mitigated the largest volumetric Distributed Denial-of-Service (DDoS) attack to this date. Recently Germany’s airports, public administration bodies, and financial sector organizations have been hit by cyber attacks carried out by a Russian hacker group.
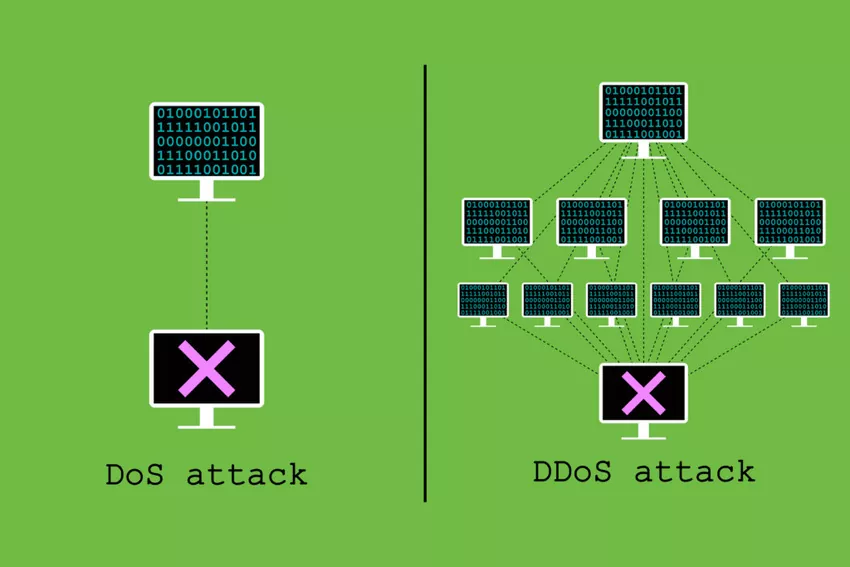
https://www.ipvanish.com/blog/dos-vs-ddos/
Types of DoS Attacks
There are 2 general forms of Dos attack, one which crash services and another that flood services.
Application DDoS Attack
It targets application-level vulnerability and weaknesses in the application that is used. This will cause application from delivering the necessary information to users. This attack is simple as clicking refresh in a web browser many times at once, which cause large number of HTTP request also called HTTP flooding. Cache-busting attack will fall under the same category.
Cache-busting Attack
Whenever a end users tries to access the internet via a web-enabled devices, Content delivery network(CDN) which already distributes content form original server to the world wide server to reduce the delivery time. Cache is a string of component that stored data so that future request can severed faster. Changing the string cause CDN to contact the original server for every page request, and these searching cause additional strain on the web server.
Application DoS Attack
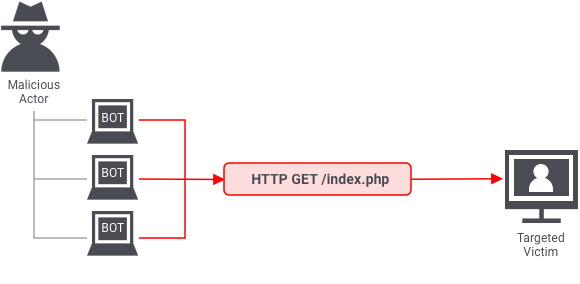
https://www.onelogin.com/learn/ddos-attack
Volume/Network Based Attacks
Combining all the available bandwidth from the server and sending several requests to the servers, thereby not allowing to access the target to general users such as UDP reflection attack.
UDP traffic doesn’t require connection between two devices before sending information(packets) and receiver doesn’t verify from where it’s coming before sending the response, because of this advantage volumetric DDoS is effective.
Attacker can craft UDP request packets by mentioning a targets IP as a source IP, where attacker send traffic to intermediate servers which create large number of traffic, because attacker mentioned target IP as source IP and the server respond with the target rather than attacker. Amplification ratio depends on the response sizes to request size. depends on the protocol attackers uses like NTP, SSDP. Example DNS can be 28 to 54 times if request payload is of 64 bytes, then DNS server generate 3400 bytes of unwanted traffic.
![]()
https://icon-library.com/icon/ddos-icon-10.html
Protocol Based Attackers
These attacks are meant to consume essential resources of the target servers like load balancer and firewall. SYN flood is the best example for this, attackers send large amount of SYN packets to the target, servers will allocate resources and send back SYN ACK to the request, now server will wait for the ACK packets where in this case attackers send SYN request without completing the connection until the server is out of resources and unable to accept other traffic. ICMP attack, Ping of death, slowloris, Buffer overflow and NTP application are some of the DoS attack which comes under protocol based attacks.
Protocol DoS Attack
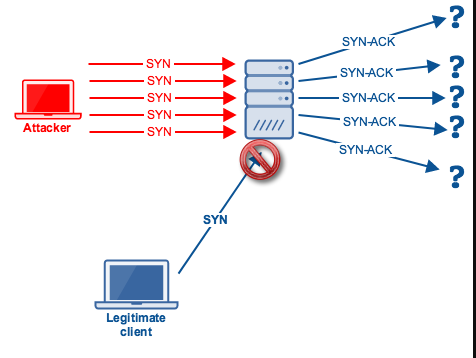
https://www.quora.com/What-does-the-TCP-SYN-flood-attack-do-to-cause-a-DDoS
Popular Forms of DoS Attacks
ICMP Attack
Internet Control Message protocol which is also know as ping flood attack, where attacker send maximum ping request from the different devices to make overwhelm a targeted devices and make it unavailable to access.
Ping of Death
Attacker send the simple ping request as fragmented IP packets that are oversized or deformed. Due to Violation in the Internet protocol maximum memory allocated to reassemble the IP header and body which caused crashes.
Slowloris
This type of attackers generally targets sever which handle incoming connection, but as a regular DDoS attack, the request are sent over a long period of time which result to incomplete open ports, due to this victim server tries to keep track of all the open connection which consumes the servers memory and CPU and makes overwhelmed of the server.
Buffer overflow
In this attack attacker send more traffic to a network address than the programmers have built the system to handle. which causes system overwhelmed and may crash also.
Pre-Measure of DDoS:
Knowing Internet Traffic Pattern
It plays an important play role, once you understand the normal traffic pattern, you’ll have a baseline. When there is any unusual traffic flow that occurs in the organization it helps to identify symptoms of a DDoS attack.
Safeguarding the Critical Asset
In the case of DDoS attack critical asset will be public asset and prioritize asset based on the need for availability. Patching and hardening and committing to good cyber hygiene which the lowers the risk of attack.
Scalability of Bandwidth
If bandwidth is scalable your organization will be able to absorb a larger amount of traffic. This will not stop DDoS attacks but can help to prevent traffic flow for genuine users. To avoid single point of failure we have to design the network with High-availability and/or load-balancer which helps the services to run in smooth without any interruption across multiple nodes.
Move to the Cloud
In cloud there will be more bandwidth than on-premises resources and cloud itself is known for its interruption services, which means cloud will already keep some of the countermeasure for such attacks and it will be less burden to the organization who are taking services from them.
DDoS Protection Services
Ensure that Internet services providers (ISP) have DDoS protection, ISP will route the malicious traffic away from the network, which helps during mitigation of any DDoS attack. ISP acts as a partial load-balancer in cases of DDoS attack. Cloudflare, Amazon Web Services, Radware are some of the services provider which can provide this type of services.
Cloudflare
It’s cloud-based DDoS protection system can deal with layer 7 attacks as well as layer 3 and layer 4 attacks.
Amazon Web Services
Using AWS Shield Standard with Amazon Cloud Front and Amazon Route 53 provides comprehensive availability protection against all known infrastructure (Layer 3 and 4) attacks
Organization DDoS Response Plan and Business Continuity Plan
Response plan will help your organization to guide the organization and all services providers. At a minimum, the plan should include the nature of attack, confirming, deploying, mitigation, monitoring and recovery for the DDoS attack. for business continuity find the alternatives for critical application mainly communication asset
Countermeasure During the Attack
Confirmation of a DDoS Attack
DDoS attacks always vary from lengths of time. Indicator of DoS incident could include network latency means slow network performance to access the Websites/files, High processor and memory utilization of bandwidth, abnormal high network traffic mean event per second will be high comparatively normal time. Also contact your Internet Services Provider to confirm if there is any outage at their end.
Understand the Nature of the Attack
Identify the range of IP addresses used to initiate the attack, looking at the attack against target services, correlate server CPU/memory utilization with network traffic logs and application availability. Conduct packet captures (PCAP) to verify that whether the firewall is blocking malicious traffic and allowing legitimate traffic to pass
Deploy Mitigation
Mitigation strategies always depend on what type of Dos attack and at what volume, but some of the standers are as follows.
1. Configuration changes to the current environment, like on public facing servers to allow the minimum amount of connections necessary to effectively conduct business.
2. All the services providers related to attack should know and understand their roles in response and recovery.
3. working with the ISP to get DoS attacks blocked.
4. sinkhole the traffic help to redirection of traffic to a particular server and the garbage packets do not reach the target.
5. Consider port and packet size filtering by the upstream network service provider.
6. Configure Strict TCP keep-alive and maximum connection on all perimeter devices.
Post Event Strategies
Continue to Monitor other Network Assets
To make sure that there should be no anomalous activity that could lead to secondary attack.
Updating DDoS Response Plan
Based on the experience of the previous attack update the DDoS response plan to improve response to future DDoS attacks such as improvements, lessons learned during communication, mitigation and recovery.
Updating the Network
Once the DDoS attack is reduced, change the configuration which was made during attack to normal as per business requirement and update the network to the latest version and patch the vulnerability.
Reporting
Report about the attack to the CERT_IN via Email (incident@nullcert-in.org.in) or Phone (1800-11-4949) and Fax (1800-11-6969). The details regarding methods and formats of reporting cyber security incidents are also published on the website of CERT-In www.cert-in.org.in and will be updated from time to time.
References:
– https://www.freecodecamp.org/news/protect-against-ddos-attacks/
– https://docs.aws.amazon.com/whitepapers/latest/aws-best-practices-ddos-resiliency/application-layer-attacks.html
– https://www.varutra.com/ctp/threatpost/postDetails/posttitle/MU1mRWFWUnZqT1p5WkJuZFlxQkRUZz09
– https://www.varutra.com/ctp/threatpost/postDetails/Cloudflare-Detects-and-Mitigates-Largest-Recorded-DDoS-Attack/dXd2cjRBZVBZSHczUVVpekJBL3NzZz09/
– https://cert-in.org.in/PDF/CERT-In_Directions_70B_28.04.2022.pdf
Author: Bharath Bistannanavar, from MSOC Team




