Android Malwares – An Overview
 Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of executable code, scripts, active content, and other software. ‘Malware’ is a general term used to refer to a variety of forms of hostile or intrusive software.
Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of executable code, scripts, active content, and other software. ‘Malware’ is a general term used to refer to a variety of forms of hostile or intrusive software.
Mobile malware is a malicious software designed specifically to target a mobile device system, such as a tablet or smartphone to damage or disrupt the device and allow a malicious user to remotely control the device or to steal personal information stored on the device.
Android malwares are continuously spreading across the globe. The rate at which android malwares are targeting the mobile phones is increasing day by day. Users install android malwares knowingly or unknowingly when they install applications from untrusted sources. It is very important that Android user’s needs to be careful while installing applications from internet.
97% of mobile malware is on Android by Forbes Report
In this article we will have overview of some well-known Android Malwares.
- AndroRat
- SandroRat
- ZitMO (Zeus-in-the-mobile)
- AcnetSteal
- Cawitt
- Gamex
- PremiumSMS
- KabStamper
- Mania
- SmsSpy
- UpdtKiller
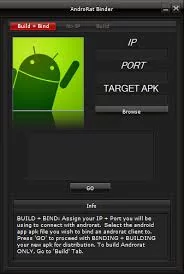
AndroRat: AndroRat is one of well-known open source proof of concept, which became an android remote access Trojan. AndroRat can bind with legitimate applications with the help of apk binder which is not freely available on internet which cost around $30-$40, available on underground hacking forums. AndroRat collects information from users mobile including contacts, call logs, messages, location, can take picture form camera, give call sends to the command and control center located at remote location.
SandroRat: SandroRat has functionalities like AndroRat including collecting contacts, call logs, messages, location, can take picture form camera, give call and sends information to the command and control center located at remote location.
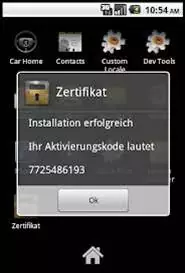
Recently samples of SandroRat received by McAfee Labs from customer in Poland with name Kaspersky_Mobile_Security.apk. Spammers use phishing techniques to spread this malware with threating emails pretending from antivirus companies.

Figure: SandroRat sample received via email
ZitMO: ZitMO is acronym of Zeus in the mobile. ZitMo is banking Trojan. ZitMo has capability to steal mobile transaction authorisation numbers (mTAN) sent by bank in text messages. ZitMo sends collected information remote server. A mobile version of Zeus also found on Blackberry smartphones.
AcnetSteal: Acnetsteal gathers data and information from infected device. It collects information like email addresses, telephone numbers. AcnetSteal uses triple DES encryption to send collected information to remote location.
Cawitt: Cawitt silently runs the background and collects information and later forwards to server located at remote location. Information collected by cawitt includes device ID, IMEI, phone number, bot ID, Modules. Cawitt can also premium rate SMS messages from the device when it receives command from server.
Gamex: Gamex hides its malicious components inside the package file. When gamex get root access by the user, it connects to command and control (C&C) server to download more applications and to forward device IMEI and IMSI numbers.
PremiumSMS: PremiumSMS android sends SMS to premium numbers and generates profit.It has a configuration file that contains data on the content of the SMS messages and the recipient numbers. Example of the sent messages:
Number: 1151 Content: 692046 169 BG QCb5T3w Number: 1161 Content: 692046 169 BG QCb5T3w
KabStamper: KabStamper malware has capability to corrupt images available on the infected devices. Basically it overwrites the images on the devices with predefined image. KabStamper is a malware that circulated in Japan during the AKB48 ‘election.’ AKB48 is a Japanese pop group that consists of 48 members. KabStamper is distributed via trojanized applications that deliver news and videos about the AKB48 group. It destroys images found in the sdcard/DCIM/camera folder that stores images taken with the device’s camera. Every five minutes malware checks this folder and modifies a found image by overwriting it with a predefined image.
Mania: Mania is SMS sending malware that sends out messages with content “tel” or “quiz” to number 84242. It pretends to perform to perform license checking to cover up its SMS-sending activities in the background. Mania is known for using the trojanization technique, where it is repackaged with another original application in order to dupe victims.
SmsSpy: SmsSpy logs incoming and outgoing SMS message to a certain file, and uploads the file to a FTP server. SmsSpy poses as an Android Security Suite application that records received SMS messages into a secsuite.db. This malware targets banking consumers in Spain where it is spammed via a message indicating that an extra Security Protection program that protects the device is available for download.
UpdtKiller: UpdtKiller connects to command and control(C&C) server, where it forwards users data to and receives further commands. This malware is also capable of killing antivirus processes in order to avoid being detected.
So how an android user can prevent himself / herself from such malwares and download authentic applications securely?
Android users should use Google play store to install application, all the application submitted to Google play store evaluated by Google Bouncer. Google Bouncer analyses the application to detect the malicious behavior in its cloud infrastructure.
Preventions of Android Malwares :
- Do not download android applications from untrusted sources.
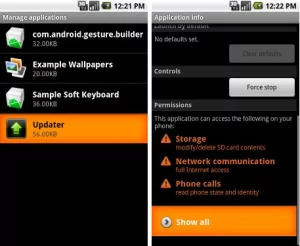
- Check the permissions of application before installing.
- Always keep your operating system secure by downloading and applying any security patches released by your smartphone vendors (to check OS level vulnerabilities on your mobile download MVD application).
Conclusion: :
Android is one of the popular mobile operating system and it holds around 80% of mobile market share; the reason Android is favorite target for attackers and so the increasing threat from android malwares. User needs to be alerted while downloading any applications from Internet and keep their phone OS up-to-date with security patches.
References:
http://www.forbes.com/sites/gordonkelly/2014/03/24/report-97-of-mobile-malware-is-on-android-this-is-the-easy-way-you-stay-safe/
http://home.mcafee.com/virusinfo/virusprofile.aspx?key=2344277
http://www.f-secure.com/
Author: Snehal Raut
Security Consultant,