VoIP Penetration Testing Part-II

In the previous tutorial VoIP Penetration Testing Part-I we have learnt on how to do Information Gathering/ Footprinting using Google dorks and identify the target IP address of the TFTP server. Now let’s start with the scanning phase.
Note: I have used dynamic IP address, so in my case VoIP Server IP is 192.168.1.108. In your case it may be different.
In scanning phase we will use following techniques,
1. Footprinting:
TOOL:
- SMAP :
SMAP is a simple scanner for SIP, enabled devices. SMAP sends off various SIP requests awaiting responses from SIP enabled DSL router, proxies and user agents.
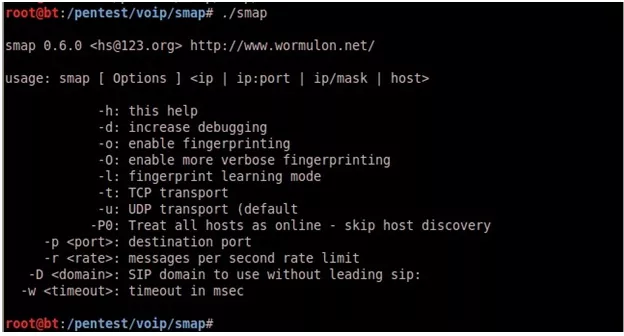
SMAP Usage:
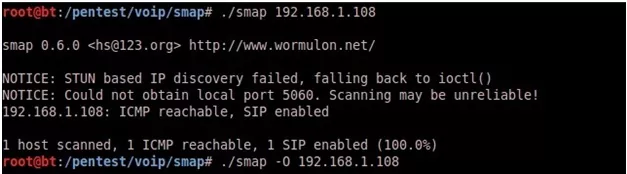
Scanning single host using SMAP:
Now identifying SIP enabled host.
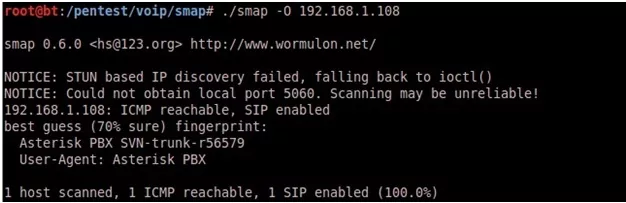
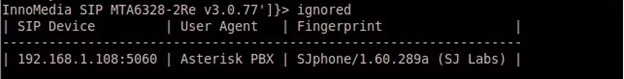
Use SMAP to fingerprint the server/client type and version:
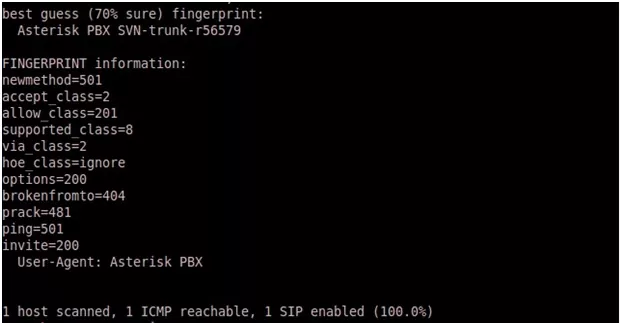
Another useful feature of SMAP is -l argument to go in learning mode to provide more useful information.
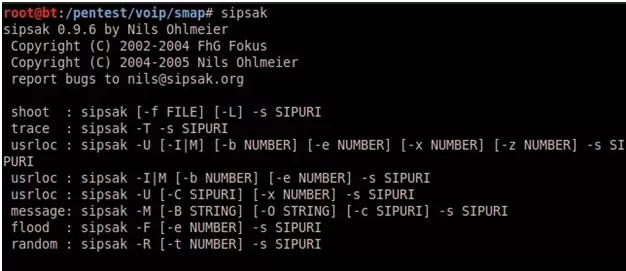
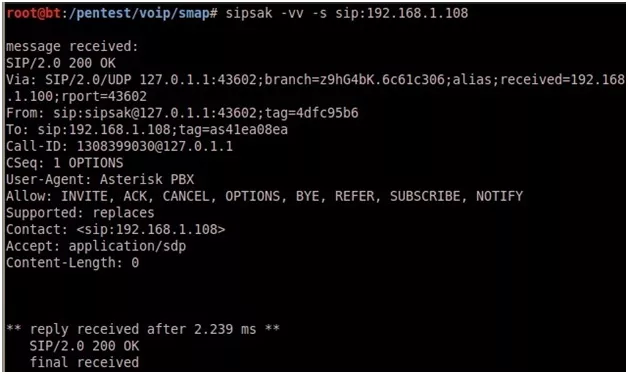
- SIPSAK :
SIPSAK is a small command line tool for developers and administrators of SIP applications.
SIPSAK Usage:
It can be used for some simple tests on SIP applications and devices.
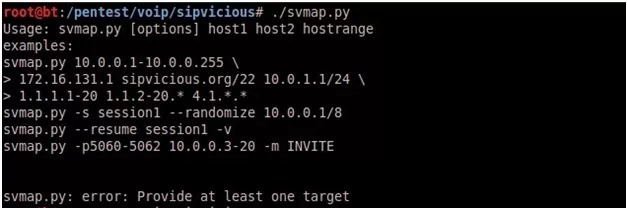
- SVMAP:
is a free and Open Source scanner to identify SIP devices and PBX servers on a target network. It can also be helpful for systems administrators when used as a network inventory tool. SVMAP was designed to be faster by specifically targeting SIP over UDP.
SVMAP Usage:
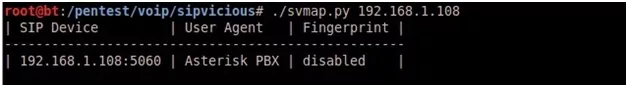
Scanning single IP using svmap:
You can also specify a name instead of an IP address:
./svmap sipvicious.org
Performing fingerprint (- -fp) scanning using svmap:
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
2. ICMP Ping Sweeps:
In ICMP Ping Sweeps, pinging includes sending ICMP type 8 packets (ICMP ECHO REQUEST) to an IP address. If the router or firewall does not block ICMP the host will reply with an ICMP type 0 packet (ICMP ECHO REPLY).
TOOL:
- fping
- Nmap
- SuperScan
- Nessus
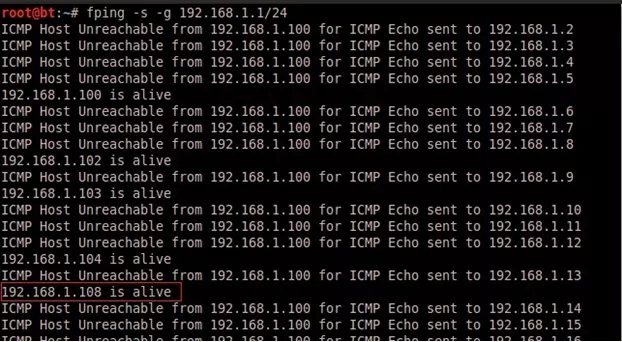
- fping:
fping is used with the command-line option –g to specify the range of hosts to scan, along with the -s option.
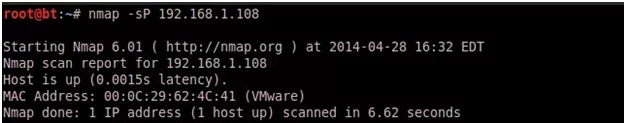
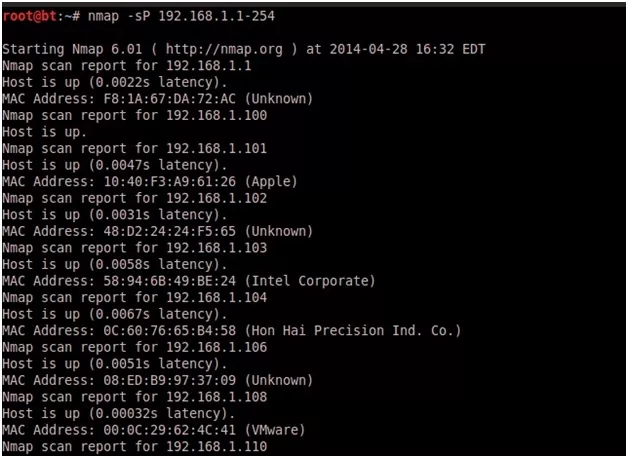
- NMAP Ping Scan (-sP):
This scan type lists the hosts within the specified range that responded to a ping. It allows you to detect, which computers are online rather than which ports are open. Four methods exist within Nmap for ping sweeping. The first method sends an ICMP ECHO REQUEST (ping request) packet to the destination system. If an ICMP ECHO REPLY is received, the system is up, and ICMP packets are not blocked. If there is no response to the ICMP ping, Nmap will try a “TCP Ping”, to determine whether ICMP is blocked, or if the host is really not online.
A TCP Ping sends either a SYN or an ACK packet to any port (80 is the default) on the remote system. If RST , or a SYN/ACK , is returned, then the remote system is online. If the remote system does not respond, either it is offline, or the chosen port is filtered, and thus not responding to anything. When you run Nmap ping scan as root, the default is to use the ICMP and ACK methods.
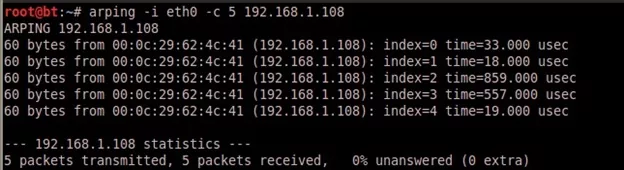
3. ARP Pings:
Arping is a command line tool for ARP pinging IP and MAC addresses. Let us find out the reachability of an IP address on the local ethernet with arping.
arping –i eth0 –c 5 192.168.1.108
Where,
–i eth0 : Specify network interface.
–c 5 : Stop after sending 5 ARP REQUEST packets.
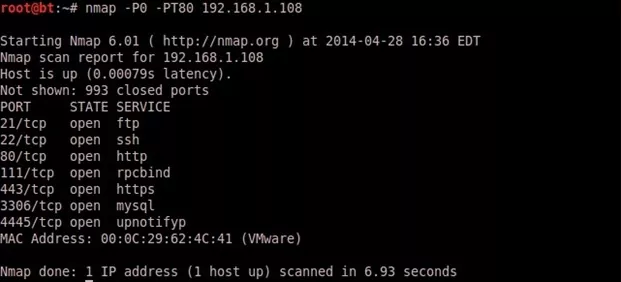
4. TCP Ping Scan:
A TCP ping scan involves sending a TCP SYN-flagged or ACK-flagged packet to a commonly used TCP port on the target host. ACK packets are more useful, because they can be used to bypass stateless firewalls that monitor only for incoming SYNs. By default, Nmap uses a SYN packet on port 80 to probe, but it can be customized from the command line to use an ACK packet on a different port using the -PT option
TOOL:
- NMAP:
5. Hping3:
Hping3 is one of the tools for security auditing and testing of firewalls and networks.
A subset of stuff you can do using hping:
- Firewall testing
- Advanced port scanning
- Network testing, using different protocols, TOS, fragmentation
- Manual path MTU discovery
- Advanced trace route, under all the supported protocols
- Remote OS fingerprinting
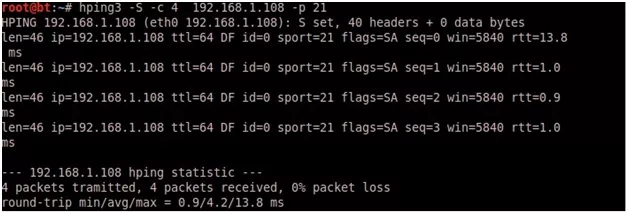
- TCP SYN SCAN:
hping3 -S -c 4 192.168.1.108 -p 21
NOTE: I had to use -c 4 flag in order to send the SYN packet four times, otherwise hping will continue sending probes.
- TCP ACK SCAN:
TCP ACK Scan can be performed by setting up ACK flag in probe packets;
hping3 -A 192.168.1.108 -p 80 -c 1
- XMAS SCAN:
XMAS Scan can be performed by setting FINISH,PUSH,URGENT flag in probe packets;
hping3 -F -P -U 192.168.1.108 -p 80 -c 1
- UDP SCAN:
hping can be configured to operate in UDP mode by specifying -2 in the command line.
hping3 -2 192.168.1.108 -p 161 -c 1
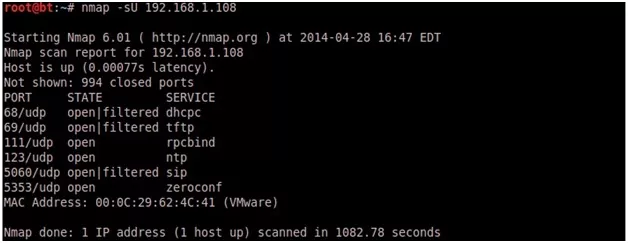
6. SNMP Sweeps:
Simple Network Management Protocol (SNMP) scanning is another effective method of determining active network equipment.SNMP v3 is based on stronger encryption such as AES and 3DES.
nmap –sU 192.168.1.108
7. Port Scanning:
TOOL:
- NMAP:
Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service up time. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
TCP SYN SCAN:
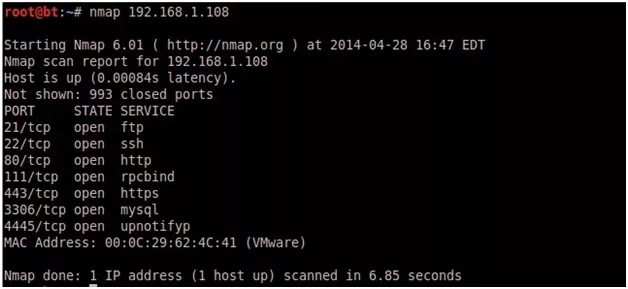
nmap 192.168.1.108
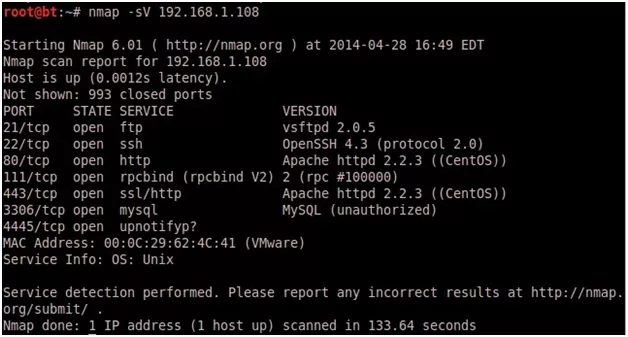
Version Detection:
nmap -sV 192.168.1.108
8. Host/Device OS Identification:
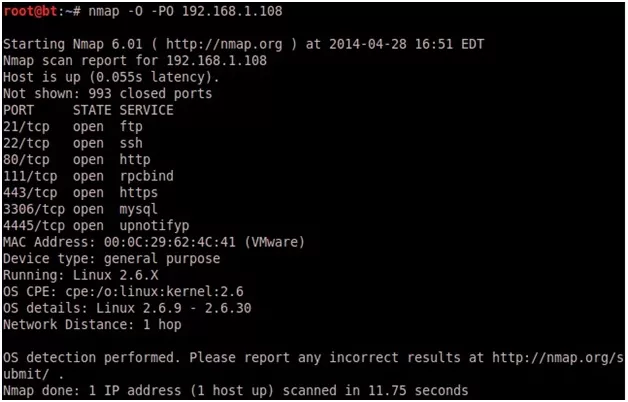
Nmap has a built-in OS detection option i.e. -O
Nmap –O –PO 192.168.1.108
9. Banner Grabbing:
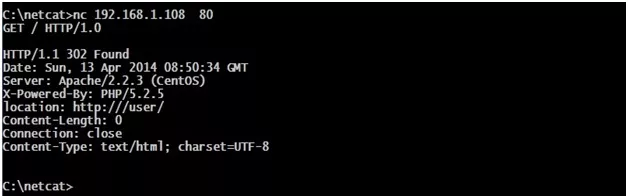
Banner grabbing, is a method of connecting to a port on a remote target to determine further information about the associated services running on that specific port(s).
TOOL:
- Netcat:
Netcat is a featured networking utility, which reads and writes data across network connections, using the TCP/IP protocol.
Written By,
Attack & PenTest Team,
Varutra Consulting
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}