Json web token (JWT) Attack – Most Common Scenarios

What is a JSON web token (JWT)?
A JSON web token (JWT) token is an open standard which defines the compact and secure way of transmitting data or information as a JSON object between two parties. It is considered secure as it is digitally signed. Since the information transmitted is signed digitally (using a secret key or private/public key pair), it can be trusted and verified at the receiver end.
A JWT token still makes a claim with respect to the parties who have signed it. It can also be encrypted to provide secrecy. Signed tokens help parties verify the integrity of claims contained in them but the encrypted tokens do not reveal those claims to other parties. Upon signing a token using public/private keys, the signature also certifies that the party having the private key is the one who signed it.
When is JSON web token (JWT) used?
It is mostly used in two scenarios
1. Authorization
JWTs are most commonly used for authorization. Every subsequent request, after a user logs-in, will contain a JWT token with it, which allows the user to access services, routes, resources, etc., that are allowed with the token. JWTs are widely used in the Single Sign-On feature due to minimum overhead and its ability to be used across various domains.
2. Information Exchange
JSON Web Tokens (JWTs) are a good way to transmit information between parties securely. Since it is possible to sign JWTs using public/private key pairs, you can be confident that the senders are who they claim they are. You can also verify that content is not modified via the signature because it is calculated using the header and the payload.
Fig -1.1 JWT Decoder
Structure of JSON web token (JWT)
The JWT token comprises three parts which are separated by ( . )
- Header: It consists of two parts; the token type used (JWT), and the signing algorithm used like RSA, HMAC, or SHA256.
- Payload: Payload is the part of a JWT that contains claims. Claims define statements about the user (entity). There are 3 types of payload claims; Registered, Private, and Public claims.
- Signature: The signature is typically used to verify the integrity of the data, so that it remains original or untampered.
It is created by the server using:
Algorithm {header + payload} — secret key
What Is the Use of KID Parameter in JSON web token (JWT) ?
The key ID (KID) header parameter indicates the key that was utilized to secure the JWS and enables originators to clearly show recipients that a change of key has taken place. There is no specified structure of the KID value; however, its value must be a case-sensitive string.
How to recognize a JWT token?
JWT token usually starts with base64 char “ey” and it is separated by two dots(.)
Algorithms
1.Symmetric
In the Symmetric mechanism, only one key is required to create and verify the JASON web token. The most common algorithm for this mechanism is HS256.
2.Asymmetric
In the Asymmetric mechanism, two different keys are required; a Private key for signing the signature and a Public key for verification. For this mechanism, the most common algorithm is RS256.
Various signature methods can be utilized to verify the integrity of a JWT such as
- RSA based
- Elliptic curves
- HMAC
- None
Now Let’s see different methods for exploiting the Json web tokens.
1.None-Algorithm
When the value of “alg” header cannot be verified by an application, you can change the value to “none”, thereby eliminating the requirement of a valid signature for verification.
Cracking a sample Json web token (JWT) using base64 decode.
Fig -1.2 Base64 Decode
Encode it now again by modifying the algorithm to None from HS256and pass it on.
- Change Algorithm from RS256 to HS256
The RS256 algorithm requires a private key for modifying the data and a public key for verifying the signature authenticity. However, when the signing algorithm is changed from RS256 to HS256, the application is made to use a single key for performing both the tasks (authentication and verification). The HMAC algorithm uses a single key for doing both the tasks.
Hence, this method changes the workflow from Asymmetric encryption to Symmetric encryption and allows using the same public key for signing new tokens.
But where is public key found?
In reality, you may get the public key from a mobile application or a JavaScript script.
Using the JWT_tool in python for exploitation
In this scenario, the following command is used, as shown in the below figure:
python3 JWT_tool.py <JWT> -S hs256 -k public.pem
Fig-1.3 JWT TOOL PAYLOAD FOR CHANGE RS256 TO HS256 ALGORITHM ATTACK
Here, first we have to download the public key from the possible sources and then sign the token with the HS256 algorithm using that key. We can create new tokens this way and can inject payload in any claim that already exists.
- Signature Not Being Checked
If the app shows no error while fuzzing the data in the Payload and Header sections, it indicates that the signature is not being checked after it is signed by the Authorization server. This allows us to inject the payload in the assertion, and the token will be valid at all times.
In this scenario, the following command is us
python3 JWT_tool.py <JWT> -I -pc name -pv admin
Fig-1.4 JWT TOOL PAYLOAD FOR SIGNATURE NOT UNCHECKED
Since the signature part is not checked, the name field can be modified in the payload section and we can get higher privileges.
For more information visit our website.
Author,
Saketh Reddy Malepu
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.


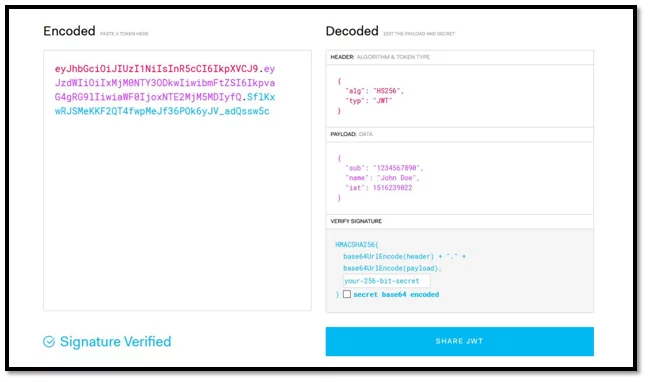 Fig -1.1 JWT Decoder
Fig -1.1 JWT Decoder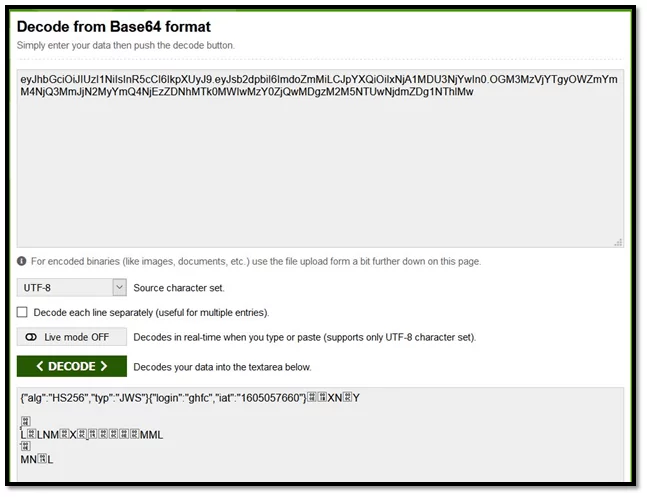 Fig -1.2 Base64 Decode
Fig -1.2 Base64 Decode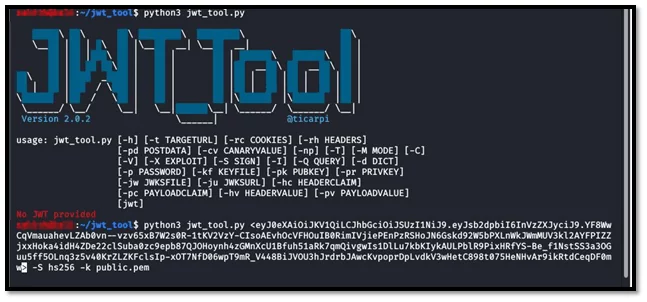 Fig-1.3 JWT TOOL PAYLOAD FOR CHANGE RS256 TO HS256 ALGORITHM ATTACK
Fig-1.3 JWT TOOL PAYLOAD FOR CHANGE RS256 TO HS256 ALGORITHM ATTACK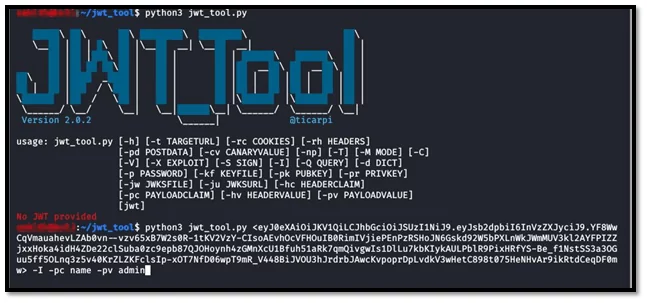 Fig-1.4 JWT TOOL PAYLOAD FOR SIGNATURE NOT UNCHECKED
Fig-1.4 JWT TOOL PAYLOAD FOR SIGNATURE NOT UNCHECKED 

