Open Redirect
What is Open Redirect?
An open redirect is a security flaw in an application or a web page that causes URLs to fail to authenticate properly. The open redirect is a failure in this phase that allows attackers to direct users to malicious websites of third parties.
When and Where Happens?
Open redirection happens when, via a user-controlled input, a web page is redirected to another URL in another domain. This happens when the program takes user-controlled data to the target of redirection in an unsafe way.
Common dorks for open redirect
Some dorks
/{payload}
?next=
?url=
?target=
?rurl=
?dest=
?destination=
?redir=
redirect_uri=
?redirect_url=
?redirect=
/redirect/
Finding possible parameters using web archive for open redirection.
Using the below link user can identify maximum parameters that could be tested for open redirection.
Automation is possible for checking for open redirect.
Use the following one Liner to test for open redirect.
gau testphp.vulnweb.com | tee -a archive 1>/dev/null && gf redirect archive | cut -f 3- -d ‘:’ | qsreplace “https://evil.com” | httpx -silent -status-code -location
Below are the GitHub links to the tools.
- https://github.com/lc/gau
- https://github.com/tomnomnom/gf
- https://github.com/tomnomnom/qsreplace
- https://github.com/projectdiscovery/httpx
- https://github.com/ffuf/ffuf
SSRF via open redirection.
This is vulnerable Lab made by Portswigger to test open redirection via ssrf.
- Access the lab and capture the request in Burp suite.
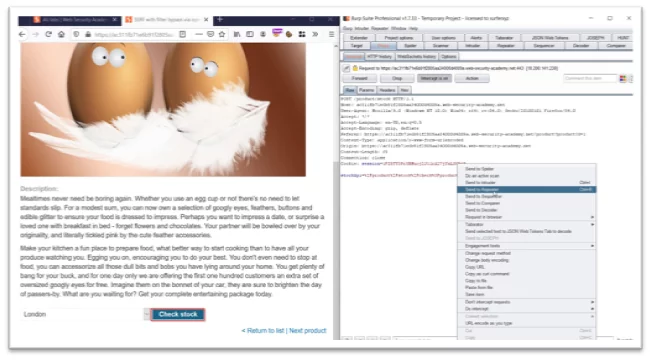
Fig 1.1 Check stock api Request
- Capture check stock request and send the request to repeater.
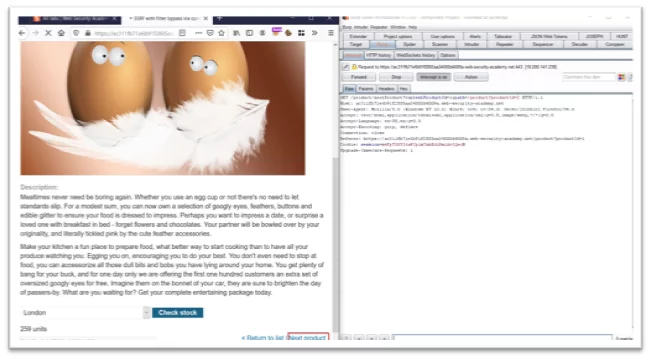
Fig-1.2 Next product intercept request
- Click on next product and send it to the repeater.
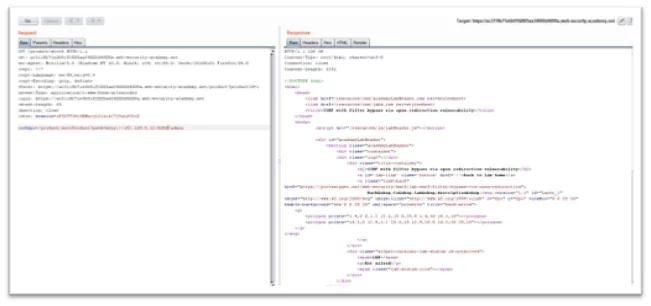
Fig-1.3 Tampering stock apiurl
- Change the stock api endpoint to /product/nextproduct?path=http://192.168.0.12:8080/admin
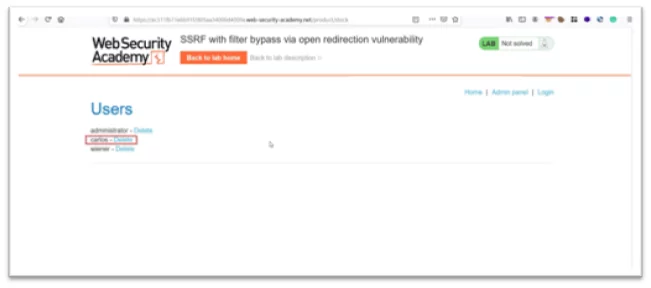
Fig -1.4 Rendering the request in Burp
- Render the request in the browser. In order to solve the lab, delete Carlos user.
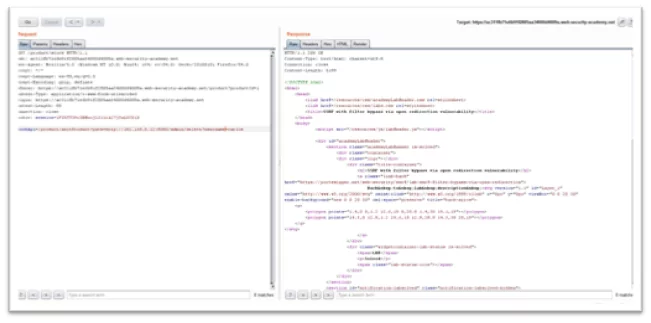
Fig-1.5 Adding delete username endpoint in order to delete carlos user
- Add the endpoint to stock api as delete/username=carlos
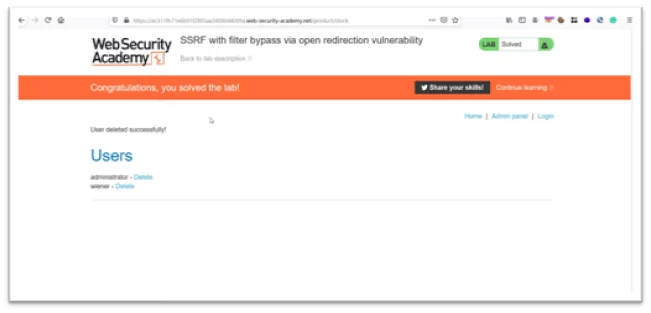
Fig-1.6 Lab Solved Successfully
How Can You Prevent Open Redirection Vulnerabilities?
Not allowing the user to control where your page redirects them to will be the simplest and most efficient way to avoid insecure open Redirects. If you want to redirect the user based on URLs, you can always use an ID that is internally resolved to the respective URL instead of using untrusted input. You can use a redirection page that needs redirection if you want the user to be able to issue redirects.
Author,
Saketh Reddy Malepu
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.




