WEB CACHE DECEPTION

Introduction:
A security researcher, Mr. Omer Gil initially proposed Web cache deception attack in 2017. This attack takes advantage of the caching functionality in the webserver to extract sensitive user data.
What is Caching?
Caching is a method used to reduce the load and time to respond to a web server. This attack mainly focuses on the configuration of caching features. If these configurations are misused, then it may lead to caching of contents that were not supposed to be cached.
We will get into the details of the attack point by point.
Request processing and CDN:
Initially, whatever request is made to the server, the connection of this request goes through a CDN (Content delivery networks). They are nothing but a geographically distributed network of proxy servers and data centers. It is implemented to gain high availability and performance by distributing the service semantically relative to the end-users. The edge servers are scattered across the world. These stored cache local copies of web content provide faster access to users, thus reducing the load on the web servers.
Edge servers are powerful computers put at the “edge” of a network where data computation needs to happen. They are physically close to the systems or applications that are creating the data being stored on, or being used by the server.
The general and most basic rule of caching is that the cached items should not contain any private or user-specific data. Ideally, static content like images, CSS files, pdf files, etc. should be cached considered as the cached content i.e., the content which is not user-specific. All those requests which are dynamic and request the user-specific data are routed to the main servers. This basic rule of caching the non-user-specific data is implemented for security reasons. As web servers, these cache servers don’t have any mechanisms for identifying any authenticated users, and these checks are provided to avoid access to unauthorized data.
The Working of Web Cache Deception:
As stated above, any request made by a user to the server over the internet may go through proxies or may be processed by several caching techniques, that include the number of CDN’s and centralized server-side caches, before it finally reaches the origin of the webserver.
In a typical Web cache deception attack, the attacker first searches a page that contains highly sensitive data such as a setting page. Then, the request is prompted to have a web caching service, such as a load balancer, reverse proxy, CDN, or other similar services, to interpret the request differently than the main web server.
Here the attacker will try to cache content that would not have been cached in any normal circumstances. Some of the web applications, especially with a non-existent object, a request will try to process it with a similar object reference if any exist. Then, the attacker will add a dynamic URL with a non-existent page or file which most probably will end in a cacheable file such as jpg, CSS, and more.
For Example:
- Assume a URL example.com/account.php refers to content containing sensitive data that should not be cached. Here, to get the request cached, an attacker will try to add an object which might look like something which is not a user-specific object, such as /account.php/nonexistent.jpg
- Now the attacker will trick the user into making a request to example.com/account.php/nonexistent.jpg, which will cause the server to respond with www.example.com/account.php because of the presence of the victim’s cookies in the request, the request contains sensitive information personal to the victim.
- The proxy considers example.com/account.php/nonexistent.jpg as a request for a non-existent, cacheable ‘nonexistent.jpg’ file, causing the content of ‘/account.php’ to be cached and accessible by others.
- The target user starts the first request, which is a key aspect of this attack. The attacker would then access the cached contents of the legitimate URL, holding the previously private data by following the same URL and caching server.
The figure below shows the summarized process explained till now.
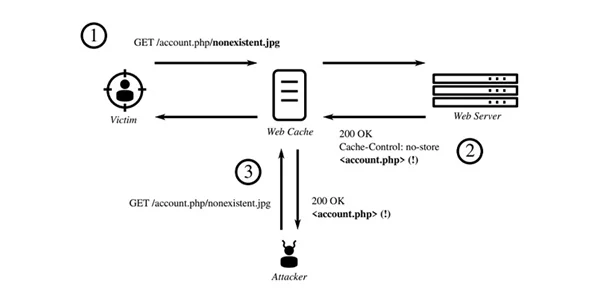
Figure: Web cache deception using path confusion
Impact of Web Cache Deception Attack :
Web cache deception can cause various attacks, such as
- Theft of sensitive information
- Insecurely stored Credit Card details
- Addresses
- Site-Specific information like,
- Search history
- Shopping cart content
- Carrying out actions on behalf of the user
- Using CSRF Tokens for a Cross-Site-Request-Forgery attack
- Account takeovers or Account theft
- Stealing access tokens or plaintext passwords
- Enabling exploitation of otherwise un-exploitable vulnerabilities, such as self-XSS.
Recommendations to Mitigate Web Cache Deception Attack :
Web cache deception mainly arises when the cache is configured poorly. The configurations of the web cache are specific to application requirements. Thus, the recommendations are also mostly application-specific. But the following are some of the generic recommendations which might mitigate to some extent but fully.
- Scripts and applications that do not assume parameters in the URI following their location should redirect to a URL they could handle, or return a 404 or 302 response.
- Assure that caching services properly follow the origin’s caching expectations, especially if the expectation is “no-store”.
- Disable any functionality that could lead to a file extension conflict between the proxy server and the origin server.
Thank you.
Author
Pralekya Hirmalwar
Attack&Pentest Team
Varutra Consulting Pvt. Ltd.




