Blockchain Security – Part 1

Blockchain is both a strength and a concern. Know basics of blockchain and blockchain security security practices to make it as secure as possible.
 Blockchain History
Blockchain History
The core ideas behind blockchain technology emerged in the late 1980s and early 1990s. In 1989, Leslie Lamport developed the Paxos protocol, and in 1990 submitted the paper The PartTime Parliament to ACM Transactions on Computer Systems; the paper was finally published in a 1998 issue.
In 1991, a signed chain of information was used as an electronic ledger for digitally signing documents in a way that could easily show none of the signed documents in the collection had been changed. These concepts were combined and applied to electronic cash in 2008 and described in the paper, in Bitcoin Peer to Peer Electronic Cash System, which was published pseudonymously by Satoshi Nakamoto, and then later in 2009 with the establishment of the Bitcoin cryptocurrency blockchain network. Nakamoto’s paper contained the blueprint that most modern cryptocurrency schemes follow (although with variations and modifications). Bitcoin was just the first of many blockchain applications.
The use of a blockchain enabled Bitcoin to be implemented in a distributed fashion such that no single user controlled the electronic cash and no single point of failure existed; this promoted its use. Its primary benefit was to enable direct transactions between users without the need for a trusted third party. It also enabled the issuance of new cryptocurrency in a defined manner to those users who manage to publish new blocks and maintain copies of the ledger; such users are called miners in Bitcoin. The automated payment of the miners enabled distributed administration of the system without the need to organize. By using a blockchain and consensus-based maintenance, a self-policing mechanism was created that ensured that only valid transactions and blocks were added to the blockchain.
In Bitcoin, the blockchain enabled users to be pseudonymous. This means that users are anonymous, but their account identifiers are not; additionally, all transactions are publicly visible. This has effectively enabled Bitcoin to offer pseudo-anonymity because accounts can be created without any identification or authorization process (such processes are typically required by Know-Your-Customer (KYC) laws).
What is Blockchain?
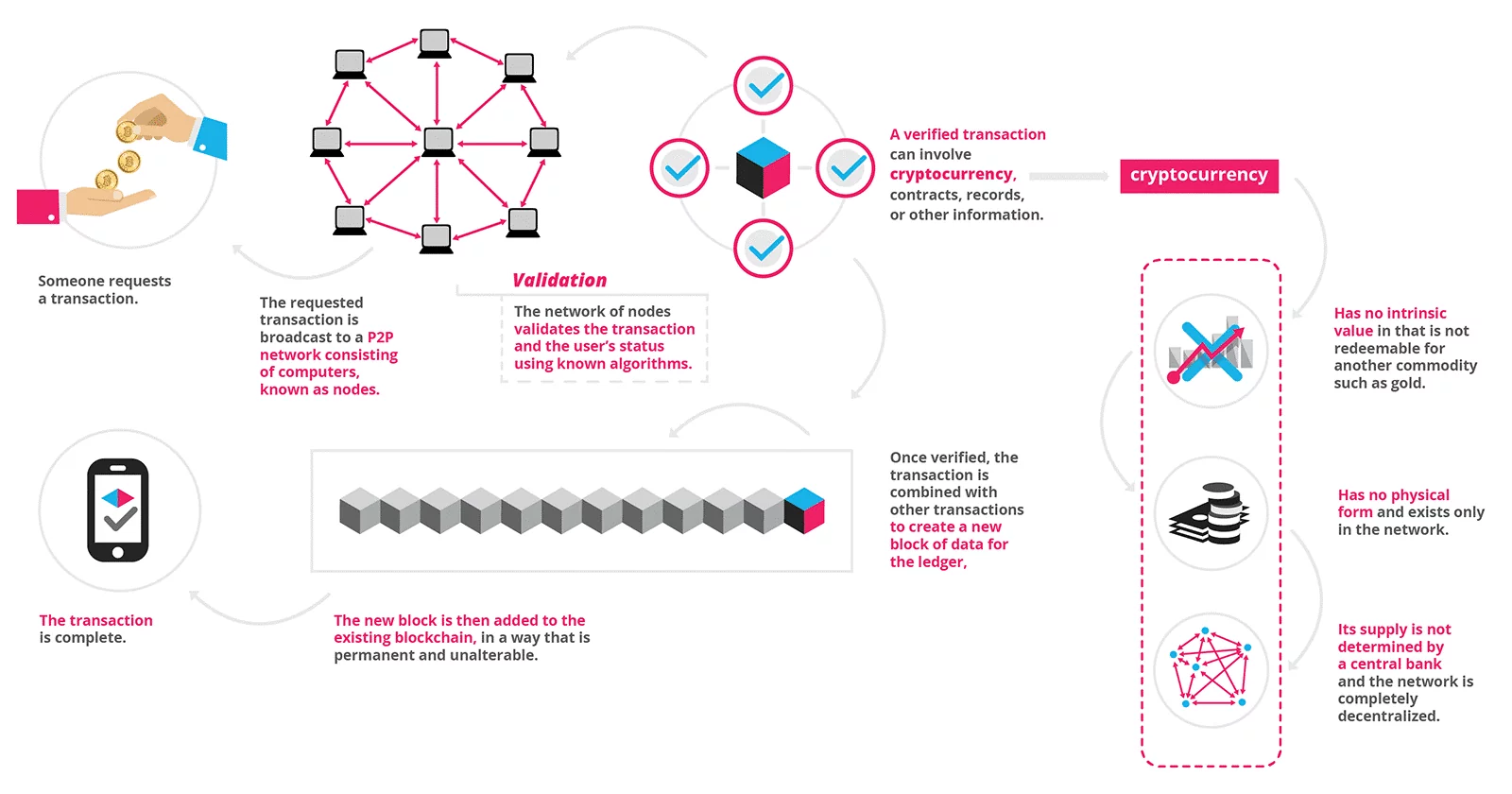
Blockchains are tamper evident and tamper resistant digital ledgers implemented in a distributed fashion (i.e., without a central repository) and usually without a central authority (i.e., a bank, company, or government). At their basic level, they enable a community of users to record transactions in a shared ledger within that community, such that under normal operation of the
blockchain network no transaction can be changed once published. In 2008, the blockchain idea was combined with several other technologies and computing concepts to create modern
cryptocurrencies: electronic cash protected through cryptographic mechanisms instead of a central repository or authority. The first such blockchain based cryptocurrency was Bitcoin.
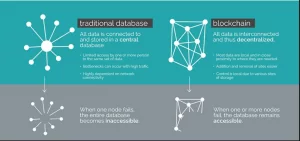
Blockchain is decentralized in nature. If the server in a traditional database fails, users can no longer work with the database. Yet with a Blockchain when one node fails, the remaining nodes stay intact. Consequently, users can keep working with the database.
Blockchain is an unchangeable, highly available, decentralized database. When participants write information in to it, encryption protects it from unauthorized access. As a result, this information becomes tamper-proof.
Blockchain writes transactions in chronologically, forms blocks, and then closes them with a checksum. Each block contains the checksum of the previous block and the system creates and distributes many copies of them. Therefore, no central unit controls the chain.
PoC: Phishing page of Blockchain
Blockchain Categorization
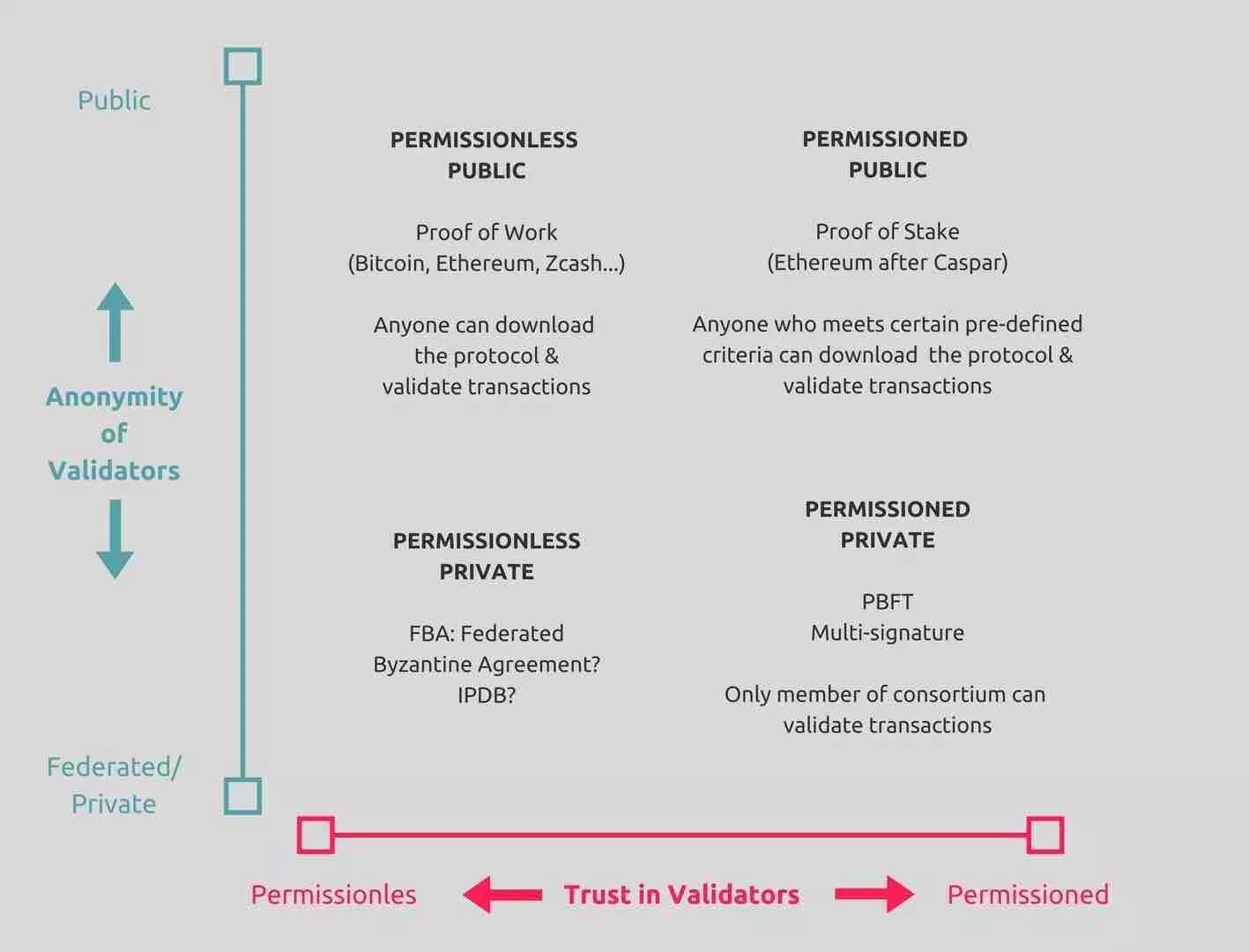
Blockchain networks can be categorized based on their permission model, which determines who can maintain them (e.g., publish blocks). If anyone can publish a new block, it is Public Blockchain. If only particular users can publish blocks, it is Private Blockchain. In simple terms, a Private Blockchain network is like a corporate intranet that is controlled, while a Public Blockchain net work is like the public internet, where anyone can participate. Private Blockchain networks are often deployed for a group of organizations and individuals, typically referred to as a consortium.
Public Blockchain
This type of blockchain is completely open and anyone can join and participate in the network. It can receive and send transactions from anybody in the world, and can also be audited by anyone who is in the system. Each node (a computer connected to the network) has as much transmission and power as any other, making public blockchains not only decentralized, but fully distributed, as well. In order for a transaction to be considered valid, it must be authorized by each of its constituent nodes through the consensus process. Once this authorization takes place, the record is added to the chain. Public blockchains typically have incentives to encourage people to join the network as well as to authenticate transactions.
One of the biggest disadvantages of a public blockchain is its complete openness. This type of transparency implies little to no privacy for transactions and supports a weak concept of security. Another drawback is the substantial amount of computing power that is necessary for the maintenance of the ledger. With so many nodes and transactions as part of the network, this type of scale requires extensive effort to achieve consensus.
Private Blockchain
In order to gain access to a private blockchain network, one must be invited and then validated by either the network starter or by specific rules that were put into place by the network starter. Once the invitation is accepted, the new entity can contribute to the maintenance of the blockchain in the customary manner. Due to the fact that the blockchain is on a closed network, it offers the benefits of the technology but not necessarily the distributed characteristics of the public blockchain. The extent to which the entity can view or validate transactions is up to the network starter to determine.
A typical way for enterprises to use private blockchains is intrabusiness, ensuring that only company members have access. This is a useful business solution if there is no reason anyone outside of the company should be part of the chain as data can be restricted to certain individuals on a need-to-know basis.
PoC: Blockchain Categorization
Can Blockchain be Hacked?
Recent hacks have proven that blockchain is not impregnable.
Nicehash hack, Dec 2017 – Cryptocurrency amounting to $78 million Bitcoin is said to be stolen from cryptocurrency mining marketplace NiceHash, emptying its entire bitcoin wallet. https://www.coindesk.com/nicehash-ceo-confirms-bitcoin-theft-worth-78-million
CoinDash ICO hack, July 2017 – CoinDash, a blockchain start-up, aimed at raising capital for cryptocurrency social trading by selling their digital tokens in exchange for Ethereum. On 17th July, the day of ICO sale, on 3 minutes after the start of the sale, CoinDash website was compromised. The address for sending investments was changed with a fake address and investments were funded to the attacker’s account. Around $7.4 million Ethereum was stolen during this hack. https://www.coindesk.com/7-million-ico-hack-results-coindash-refund-offer
Krypton (KR) & Shift (SHF), Aug 2016 – Attackers targeted Ethereum-based Blockchains as the cryptocurrencies, Krypton (KR) and Shift, both Ethereum type coins using the version of 51% attack. The attackers could exploit the Blockchain with a two-step attack. Overpowering the network with 51% attack to ensure rollback on transactions and spending the coins twice; and employing DDoS nodes to enhance network power. The attack led to the loss of 21,465 KR, $3000 at the time.
Steemit, July 2016 – The Blockchain-based blogging platform, was hacked. Vulnerability on the Web browser front end and not on the cryptocurrency itself led to this attack. Around 250 user accounts were compromised, resulting in the loss $85,000 worth of Steem Dollars and cryptocurrency Steem. https://www.ccn.com/steemit-secures-hacked-accounts-advises-new-password/
The DAO, May 2016 – Blockchain based venture capital, The DAO – an Ethereum Project, hacked for $60 million. https://en.bitcoinwiki.org/wiki/The_DAO
Blockchain Attacks
The demand for the security of bitcoins based on blockchain has increased since hacking cases were reported. Mt. Gox, a bitcoin exchange based in Tokyo, Japan, reported losses of USD 8.75 million due to hacking in June 2011 and bitcoin wallet service InstaWallet reported losses of USD 4.6 million due to hacking in April 2013.
In November of the same year, anonymous marketplace Sheep Marketplace was forced to shut down after somebody stole USD 100 million worth of bitcoins. Mt. Gox, which had already suffered losses due to hacking, again reported losses of USD 470 million due to hacking in February 2014 and subsequently filed for bankruptcy. The problems continued, with the Hong Kong-based bitcoin exchange Bitfinex reporting losses of USD 65 million due to hacking in August 2016. These problems have raised awareness of the need for security.
With recent study by Varutra Consulting, below attacks were identified recently:
Phishing Attack
Phishing scams are the most familiar blockchain attacks due to their prevalence and success rate. Consider the Iota cryptocurrency. Victims lost $4 million in a phishing scam that lasted several months. The attacker registered iotaseed.io, providing a working seed generator for an Iota wallet. The service worked as advertised and enabled victims to successfully create and use their wallets as expected, providing a false sense of security and trust. The attacker then waited, patiently taking advantage of the building trust. For six months, the attacker collected logs, which included secret seeds, and then began the attack. In January, using the information previously stolen, the attacker transferred all funds from the victims’ wallets. 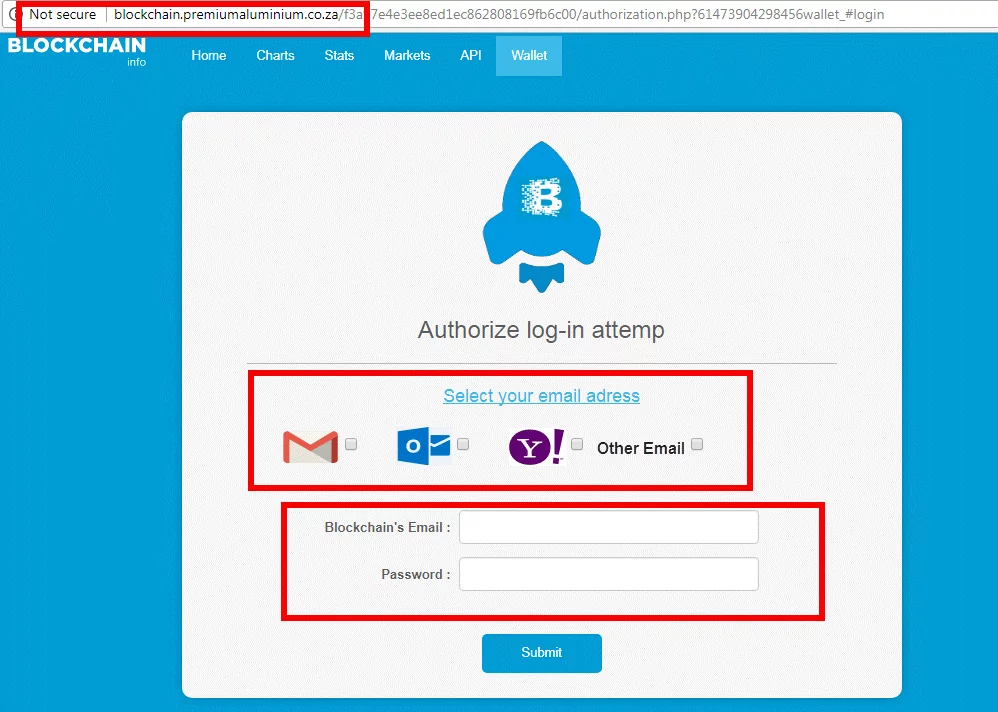
PoC: Phishing page of Blockchain
Authentication Attack
An important part of blockchain security is security related to the personal key used in encryption. An attacker carries out various attempts to access a user’s personal key stored in the user’s computer or smartphone in order to hack the bitcoin. The attacker will install malware on the computer or smartphone to leak the user’s personal key and use it to hack the bitcoin. It has been proposed a hardware token for the approval of a transaction to protect the personal key.
It was suggested strengthened authentication measures for the storage unit containing the bitcoin. A two-factor authentication is considered to be the leading method for strengthening authentication. For bitcoin, the two-party signature protocol by ECDSA can be used for authentication.
Security Incidents
The Distributed Denial of Service (DDoS) attack floods the targeted server with superfluous requests to overload the system and prevent the provision of normal service to other users. Thus, it can prevent the users of blockchain from receiving the service. DDoS attacks include the bandwidth-consuming attack that exceeds the bandwidth of all systems using the same network and the PPS (Packet Per Second)-consuming attack that causes internal system failure or the denial of service to other servers in the same network.
The http-flooding attack transfers a large amount of http packets to a targeted server to cause the denial of service. Since the bitcoin service must be continuously provided to the users, countermeasures to DDoS attacks are needed.
Majority Attack
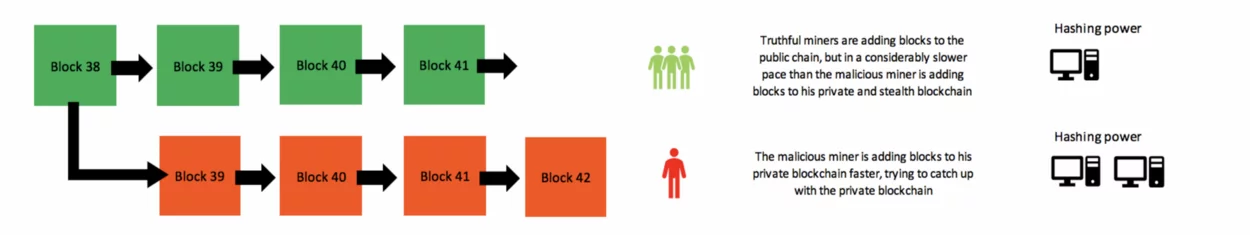
A majority attack (usually labeled 51% attack or >50% attack) is an attack on the network. This attack has a chance to work even if the merchant waits for some confirmations, but requires extremely high relative hash-rate.The attacker submits to the merchant/network a transaction which pays the merchant, while privately mining a blockchain fork in which a double-spending transaction is included instead. After waiting for n confirmations, the merchant sends the product.
If the attacker happened to find more than n blocks at this point, he releases his fork and regains his coins; otherwise, he can try to continue extending his fork with the hope of being able to catch up with the network. If he never manages to do this, the attack fails, the payment to the merchant will go through, and the work done mining will also go to waste, as any new bitcoins would be overwritten by the longest chain.
PoC: Majority Attack (51% attack)
Finney Attack
A Finney attack works as follows: Suppose the attacker is generating blocks occasionally. in each block generates and includes a transfer from address A to address B, both of which attacker can controls. To cheat victim, attacker will generates a block, which doesn’t broadcast it. Instead, opens the store web page and makes a payment to victim’s address C with his address A.victim may wait a few seconds for double-spends, not hear anything, and then transfer the goods. attacker broadcasts his block now, and his transaction will take precedence over victim’s.
PoC: Finney Attack
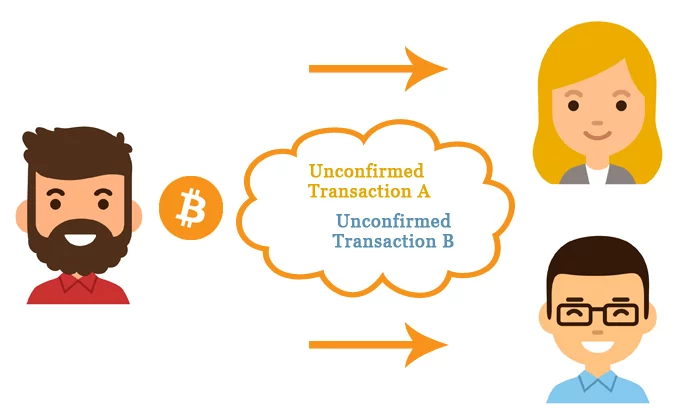
Race attack
Traders and merchants who accept a payment immediately on seeing “0/unconfirmed” are exposed to the transaction being reversed. An attempt at fraud could work that the fraudster sends a transaction paying the merchant directly to the merchant, and sends a conflicting transaction spending the coin to himself to the rest of the network. It is likely that the second conflicting transaction will be mined into a block and accepted by bitcoin nodes as genuine.
Merchants can take precautions (e.g., disable incoming connections, only connect to well-connected nodes) to lessen the risk of a race attack but the risk cannot be eliminated. Therefore, the cost/benefit of the risk needs to be considered when accepting payment on 0/unconfirmed when there is no recourse against the attacker.
Conclusion
Blockchain is still an emerging technology and evolving with each passing day. Most security vulnerabilities are patched up quickly, and in extreme cases, they can result in a new version of that blockchain known as a hard fork. This is what Ethereum did to recover $55 million worth of Ether when it was stolen from the DAO (Decentralized Autonomous Organization) smart contract.All things considered, blockchain is a much better solution to storing and exchanging digital value than anything that has come before it. Does that mean it’s perfect? No, but then nothing is. What’s important is we keep developing and improving the blockchain ecosystem to make it as secure as possible.
Author,
Tanmay Nashte
Attack & PenTest Team
Varutra Consulting