Security Advisory – Saipem Cyber Attack by Shamoon Malware

Saipem Cyber Attack by Shamoon Malware
1. Introduction
Saipem identified cyber-attack on Monday i.e. on 10th December 2018 that had primarily affected its servers in the Middle East. The cyber-attack hit servers based in the Middle East, India, and Aberdeen and in a limited way Italy through a variant of Shamoon malware. Shamoon malware is also known as Disttrack. The attack crippled between 300 and 400 servers and up to 100 personal computers out of a total of about 4,000 Saipem machines. The company does not know who was responsible for the attack.
2. Shamoon Malware
Shamoon is a disk-wiping malware it disables computers by overwriting master boot record making it impossible for devices to start up. Once overwritten the data is not recoverable. Shamoon is designed to destroy computer hard drives. It attempts to access default shared folders like Admin$ shares to spread among the network. It uses remote registry to disable UAC (User Access Control) and enable shares & to spread through the network. Shamoon relies on the remote registry system to disable User Account Control on the remote target, allowing the malware to install itself in the %WinDir%\ system32 directory and create a Scheduled Task without alerting the user.
Distribution Method: Via Trojan installation and password stealing.
3. Prevention and Remediation With SIEM
In order to prevent future infection and lateral movement of the malware across the enterprise, the following actions can be taken in addition to implementing the SIEM rules. Because these mitigations have implications across the enterprise network, it is important to assess the impact of making these changes and ensure appropriate policies and procedures to implement and support these changes are evaluated.
The Shamoon malware does not rely on exploiting application or operating system vulnerabilities to be successful. Instead, it uses hardcoded Windows Active Directory credentials and weak domain security configurations to infect and spread across the enterprise. Prevention of this type of attack requires hardening of the security policy on the network. Following are examples of security measures that should be implemented and how each prevents attacks such as Shamoon:
Note: If the malware is successful in wiping the affected systems, analysts can remediate this malware from a system or network only by restoring from backup.
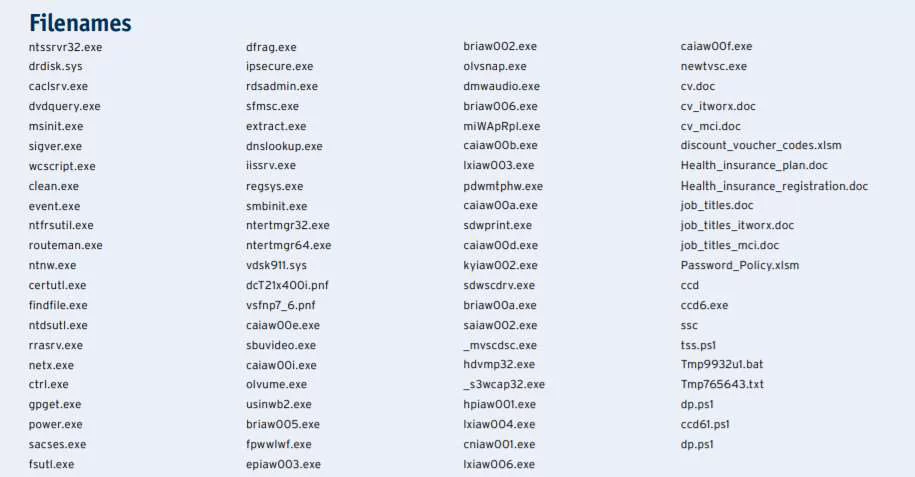
Below are the indicator of compromise:
4. Varutra Recommendation
1. Maintain the strong passwords policy.
2. Disable credential caching for all desktop devices.
3. Restricting account privileges.
4. Where possible, disable RDP on critical devices.
5. Ensure all network operating systems, web browsers, and other related network hardware and
software are updated with all current patches and fixes.
6. Restrict users permissions to install and run unwanted software applications.
7. Any unused applications or functions should be removed or disabled.
8. Consider the deployment of software restriction policy set to only allow the execution of
approved software (application whitelisting).
9. Consider the use of two-factor authentication methods for accessing privileged root level
accounts or systems.
10. Ensure the latest account credential protection is enabled on all Windows systems by verifying
that enterprise systems are kept updated with the latest Windows Update software.
11. Educate users to not to open and download suspicious files and to inform ITIM department if
they receive any spam or phishing email.
12. Keeping up to date antivirus signature set on the machines and enable the disabled antivirus
components.
5. Reference
- https://www.reuters.com/article/us-cyber-shamoon/saipem-says-shamoon-variant-crippledhundreds-of-computers-idUSKBN1OB2FA
- https://www.symantec.com/connect/blogs/shamoon-back-dead-and-destructive-ever
Author,
Umang Waghmare
SOC Team
Varutra Consulting Pvt. Ltd.