CSRF Vulnerability on LinkedIn
In previous blog we have seen a critical vulnerability in LinkedIn password reset module allowing an attackers to compromise LinkedIn user’s account and how helpless a LinkedIn user in case of an actual compromise of his / her account in real world scenario.
Here is a new vulnerability Cross-Site Request Forgery, CSRF present on LinkedIn Recommendation Section, which allows attacker to delete any Recommendation of Any user.
Lets us understand the CSRF issue and simplicity of this attack.
1. Attacker / malicious LinkedIn user can check the recommendation given by LinkedIn User 1 to LinkedIn User 2.
2. Attacker logs into LinkedIn account, goes to the web page source and search for strings such as “Recommendation for USERNAME”.
Figure: Web page source shows the recommendation details with a unique Id ”515940281” for User 1’s recommendations to User 2.
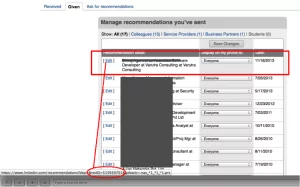
3. To craft a malicious CSRF link attacker goes to Manage Recommendation area and check for any recommendations he has posted for others. Clicks on it and copy the URL for any one recommendation.
The URL will be
https://www.linkedin.com/recommendations?dep=&recID=515830421&goback=%2Enas_*1_*1_*1%2Eprs
Figure: Analyzing and collecting URL for Displaying and Withdrawing a User’s recommendation.
4. Now same way the URL to withdraw any given recommendation by the attacker is
https://www.linkedin.com/recommendations?wdr=&recID=515830421&goback=%2Enas_*1_*1_*1%2Eprs
The only difference is to change the parameter from ‘dep’ to ‘wdr’.
Craft a URL for removing or withdrawing recommendation from User 1 to User 2 is
https://www.linkedin.com/recommendations?wdr=&recID=515940281
This is the shortest and simplest form of the vulnerable CSRF link.
5. Send this URL to User 1 in an email. More dangerously, the same CSRF link can be send using LinkedIn mail feature.
6. On clicking this link by User 1 the selected recommendation given by User 1 to User 2 will be withdrawn or deleted.
On reporting this issue LinkedIn was prompt to acknowledge the vulnerability and have mitigated it.
More can be read at http://packetstormsecurity.com/files/127259/
Written By,
Attack & PenTest Team,
Varutra Consulting