How Hackers Use Social Engineering to Spread Dridex Malware
What is Dridex Malware?
Dridex is a highly sophisticated form of malware that has been active since 2014, with the primary goal of stealing banking credentials from its victims. This malware is classified as a Trojan, which hides malicious code within seemingly harmless data. It is typically spread through phishing campaigns that target Windows users with malicious emails, prompting victims to open attached Word or Excel files. Once opened, the malware infects the victims computer and enables cybercriminals to steal personal information, primarily banking credentials.
Evil Corp, a Russia-based group, is thought to have made several updates to the Dridex Banking Trojan in the last decade.The Dridex malware can evade antivirus detection controls, making it hard to detect. Since the malware constantly changes and uses new and unknown signatures, signature-based threat detection software may not be effective against it. User behavior analytics software, which relies less on signature-based threat detection, could be a better alternative to other tools.
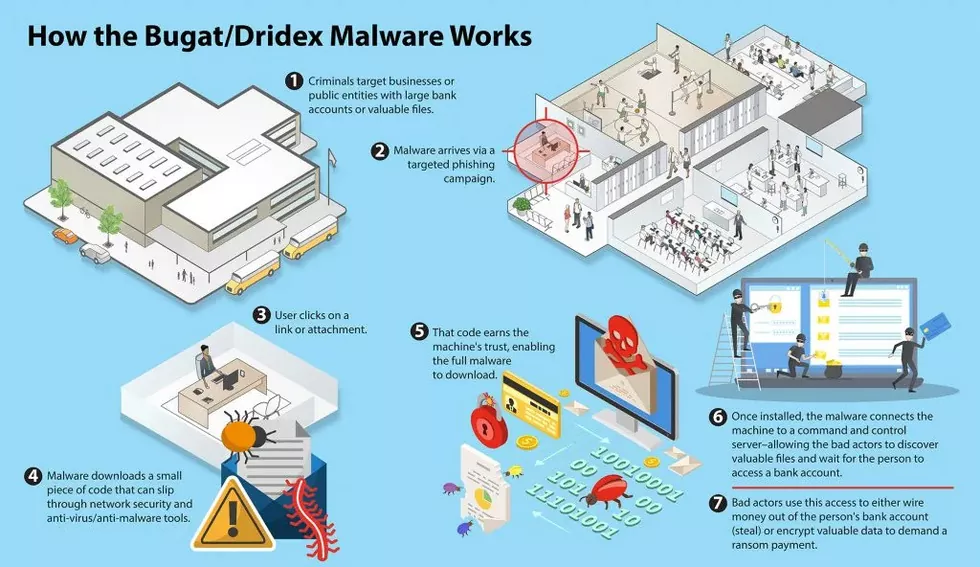
How does Dridex Malware work ?
Dridex malware is a sophisticated banking trojan that is designed to steal sensitive information from victims, including login credentials, financial information, and personal data. It is typically delivered via phishing emails, which are designed to trick users into opening an attachment or clicking on a link that downloads the malware onto their device. Once installed, the malware will remain dormant until the user visits a banking website or enters their credentials, at which point it will activate and begin recording keystrokes and other sensitive data.
https://www.spambrella.com/what-is-dridex-malware/
The malware is modular in nature, meaning that it can download additional modules or updates to enhance its functionality. Some of the additional modules that have been observed in Dridex attacks include a network scanner that can map out the victim’s network, a screenshot grabber that can capture images of the victim’s screen, and a data stealer that can exfiltrate data to the attacker’s command and control servers.
One of the unique features of Dridex malware is its use of a decentralized peer-to-peer (P2P) network for communication between the infected devices and the command and control servers. This makes it more difficult for security researchers to track and disrupt the malware, as there is no single point of failure in the communication network.
Dridex malware is constantly evolving, and new variants are being developed and deployed by cybercriminals on a regular basis. As such, it is critical that organizations implement robust security controls, such as email filtering, endpoint protection, and user awareness training, to prevent Dridex malware infections and mitigate the impact of any successful attacks.
How to detect Dridex malware ?
Detecting Dridex malware can be challenging, as it is designed to evade traditional signature-based antivirus and intrusion detection systems. However, there are several strategies that organizations can employ to identify and mitigate Dridex infections:
a.Email filtering
Dridex malware is typically delivered via phishing emails, which can be identified and blocked by email filtering solutions. These solutions can analyze the content, attachments, and sender information of incoming emails and block suspicious messages before they reach the user’s inbox.
b.Endpoint protection
Endpoint security solutions can detect and prevent Dridex malware infections by monitoring system activity, detecting suspicious behavior, and blocking known malicious files and processes. Some endpoint protection solutions also include advanced features such as memory scanning and behavioral analysis to detect and prevent zero-day attacks.
c.User awareness training
Educating users on how to identify and avoid phishing emails can be an effective way to prevent Dridex infections. Users should be trained to recognize suspicious emails and to avoid clicking on links or downloading attachments from untrusted sources.
d.Network monitoring
Network monitoring solutions can detect and alert on unusual network activity that may indicate a Dridex infection. These solutions can detect communications between infected devices and command and control servers, as well as lateral movement within the network.
e.User behavior analytics
User behavior analytics solutions can detect anomalous behavior on endpoints and identify potential insider threats. These solutions can analyze user activity and alert on deviations from normal behavior, such as excessive data access or unusual login patterns.
f.Insider threat hunting
Insider threat hunting involves proactively searching for signs of malicious activity within the organization. This can include reviewing access logs, analyzing network traffic, and conducting forensic investigations on suspicious devices or user accounts.
By implementing these strategies, organizations can increase their chances of detecting and mitigating Dridex malware infections. It is important to remember that no single solution is foolproof, and a multi-layered defense strategy is necessary to effectively protect against advanced threats like Dridex malware.
Does dridex malware can spread by macOS ?
Dridex malware is primarily designed to target Windows operating systems and is not known to affect macOS. This is because Dridex malware is typically distributed as a Microsoft Word or Excel document that contains malicious macros, which are scripts that automate tasks within the document. These macros are written in Visual Basic for Applications (VBA) code, which is specific to Microsoft Office and does not run on macOS.
While it is technically possible for Dridex malware to be modified or re-engineered to target macOS systems, there have been no known cases of this occurring in the wild. Additionally, macOS systems have built-in security features, such as Gatekeeper and XProtect, that can detect and block known malware and prevent unauthorized software from running.
However, it is still important for macOS users to remain vigilant and practice good security hygiene, such as avoiding suspicious emails, regularly updating software, and using reputable antivirus and endpoint protection solutions. While the risk of Dridex malware on macOS is low, there are other types of malware and cyber threats that can target these systems, and it is important to take steps to protect against these threats.
How to remove Dridex malware ?
Removing Dridex malware can be a challenging task, as the malware is designed to evade detection and removal. However, there are several strategies that can be used to remove Dridex malware from infected systems:
a.Antivirus and anti-malware software
The first step in removing Dridex malware is to run a full system scan using a reputable antivirus or anti-malware software. These solutions can detect and remove known instances of Dridex malware, as well as other types of malware and viruses that may be present on the system.
b.Malware removal tools
There are several specialized tools available that are designed specifically to detect and remove Dridex malware. These tools can be downloaded from reputable security vendors and should be used in conjunction with antivirus and anti-malware software for maximum effectiveness.
c.Manual removal
In some cases, Dridex malware may be resistant to automated removal methods and may require manual removal. This involves identifying and removing all associated files and registry entries, which can be a time-consuming and complex process. It is recommended to seek the assistance of a professional IT or security specialist for this task.
d.System restore
If the infected system has a recent system restore point available, it may be possible to restore the system to a state before the infection occurred. This can be done using the built-in System Restore feature in Windows or through a backup solution.
It is important to note that removing Dridex malware does not necessarily guarantee that all traces of the malware have been eliminated. In some cases, the malware may have left behind backdoors or other malicious components that could allow attackers to regain access to the system. As such, it is recommended to perform a thorough security audit and implement additional security measures, such as network monitoring and access control, to prevent further attacks.
What is Social Engineering?
Social engineering is a malicious activity that uses psychological manipulation to trick individuals into making security mistakes or giving away sensitive information. These attacks leverage human error, rather than exploiting vulnerabilities in software or operating systems. The perpetrator may initiate social engineering attacks through a gradual process that involves several steps. The first step is gathering the necessary background information to proceed with the attack. After that, they move to gain the victim’s trust and use stimuli to encourage subsequent actions that violate security practices. Social engineering attacks can occur in one or more stages and are often difficult to detect.
The weakest link in the security chain is the human element that readily accepts a person or scenario without suspicion. Criminals frequently resort to social engineering tactics because it is often easier to exploit an individual’s natural tendency to trust rather than discovering methods to hack their software. The type of information criminals seek can vary, but when targeting individuals, they typically aim to deceive them into disclosing their passwords or banking information or providing access to their computer. In some cases, the criminals secretly install malicious software that allows them to access the victim’s passwords, banking information, and control over their computer.
Social engineering techniques have evolved with the advancement of ICT technologies. Scammers employ social engineering techniques such as Tailgating, pretexting, quid pro quo, and baiting to achieve objectives outside the IT realm or gain further access to an IT system. These techniques involve using IT technologies to support psychological manipulation techniques or directly manipulating individuals using psychological tactics.
Pretexting involves using a false justification for a specific course of action to gain the victim’s trust and trick them into providing sensitive information or performing a desired action. An example of pretexting is an attacker claiming to work for IT support and requesting the target’s password for maintenance.
How Do Hackers Use Social Engineering to Spread Dridex Malware?
In the world of cybersecurity, email is often the primary vehicle for hackers to deliver malware, phishing scams, and other types of cyber attacks. Hence, it is essential to be careful when receiving emails from unfamiliar sources. You should never click on any links or download attachments unless you are confident that the email is legitimate. Hackers may try to disguise their emails as coming from a reputable source, such as a bank or a well-known company, to trick you into divulging personal information or downloading malware. By being vigilant and scrutinizing any suspicious emails, you can prevent yourself from falling victim to cyber attacks and safeguard your personal data.
a.Phishing Emails
Phishing emails are a common way for cybercriminals to spread Dridex malware through social engineering tactics. These emails are designed to trick you into believing that they are from a legitimate source, such as your bank or a well-known company. The attackers often use persuasive language to entice you to click on a link or download an attachment. However, by doing so, you could be downloading Dridex malware onto your computer, which could result in significant harm, including data breaches, financial loss, and identity theft. Therefore, it is essential to be cautious when opening emails and to verify the authenticity of the sender before taking any action to protect yourself from falling victim to such phishing attacks.
b.Impersonation
One of the ways cybercriminals spread Dridex malware is through social engineering tactics like impersonation. The attackers may impersonate a trusted source, like a friend or colleague, and send an email with a link or attachment that they claim is important. They may even create fake accounts or spoof emails to make them appear legitimate. Once you click on the link or download the attachment, Dridex malware can infect your computer.
Therefore, it is essential to verify the identity of the sender before clicking on any links or downloading any attachments. By being vigilant and careful, you can protect yourself from these types of attacks and avoid falling victim to Dridex malware.
How Can You Protect Yourself from Dridex Malware?
There are several things you can do to protect yourself from Dridex malware
a.Be Careful with Emails
In today’s interconnected world, email has become an essential tool for communication, but it is also a prime target for cybercriminals. They often use social engineering tactics to trick unsuspecting users into clicking on malicious links or downloading infected attachments. These emails may appear to be from legitimate sources, but they are, in fact, part of a sophisticated phishing campaign to spread malware like Dridex. Therefore, it is crucial to scrutinize any suspicious emails and avoid clicking on links or downloading attachments unless you are confident about their legitimacy. By following this simple best practice, you can significantly reduce the risk of becoming a victim of cybercrime.
b.Use Antivirus Software
Antivirus software is an essential tool for protecting your computer from various types of malware, including Dridex. It can detect and remove malicious software, preventing it from causing harm to your computer and stealing your sensitive information. Antivirus software works by scanning your system for known viruses, suspicious activities, and potential vulnerabilities. It can also provide real-time protection by blocking incoming threats before they can infect your system. Some antivirus software even offers additional features, such as firewall protection and safe browsing, to enhance your overall online security. It’s crucial to keep your antivirus software up-to-date to ensure that it can effectively protect your computer from new threats.
c.Keep Your Software Up to Date
Keep your software up to date to ensure optimal security. This can help prevent hackers from exploiting vulnerabilities in your software to spread viruses like Dridex malware. Installing software updates as soon as they become available is crucial as most updates include security fixes. Many operating systems and software applications offer automatic updates, which can be set to run in the background without any intervention required from the user. Make sure to enable automatic updates or check for updates regularly to stay protected.
d.Be Wary of Impersonators
Impersonation is a common tactic used by scammers and hackers to spread malware or steal sensitive information. Be cautious when you receive messages from someone you don’t know or from an account that seems unusual. To ensure safety, it is advisable to confirm the sender’s identity before downloading attachments or clicking on links. Hackers can easily spoof email addresses and websites to make them look legitimate, so be careful when entering personal or financial information online.
Conclusion
In addition to being careful with emails and messages from unknown sources, it’s also important to be vigilant about your online activity. To minimize risks, it is recommended to refrain from visiting suspicious websites or downloading software from untrusted sources. Keep your passwords secure and consider using two-factor authentication for added security. Regularly back up your important files and data, so that if your computer does become infected with Dridex malware or another virus, you have a backup of your important information. By taking these precautions, you can help reduce your risk of falling victim to cyber attacks and keep your sensitive information safe.
Research, References & Resources :
https://www.spambrella.com/what-is-dridex-malware/
https://www.techtarget.com/searchsecurity/definition/Dridex-malware
https://any.run/malware-trends/dridex
https://cybersecurity.att.com/blogs/security-essentials/dridex-malware-the-banking-trojan
https://www.tutorialspoint.com/dridex-malware-mode-of-operation-how-to-detect
https://www.blackberry.com/us/en/solutions/endpoint-security/ransomware-protection/dridex
https://www.thesecuritybuddy.com/malware-prevention/what-is-dridex-malware/
https://www.cmu.edu/iso/aware/dont-take-the-bait/social-engineering.html
https://www.cygularity.com/post/2020/06/02/exploiting-the-weakest-link-humans-social-engineering
https://www.studocu.com/row/document/universite-mohammed-v-de-rabat/informatique/cyber-security-2/43580711
https://www.helprange.com/post/files-security-protection/protecting-your-files-from-phishing-attacks
https://itcoverage.com/system-software-update-why-you-shouldnt-skip-them/




