“OAuth” Related Vulnerabilities
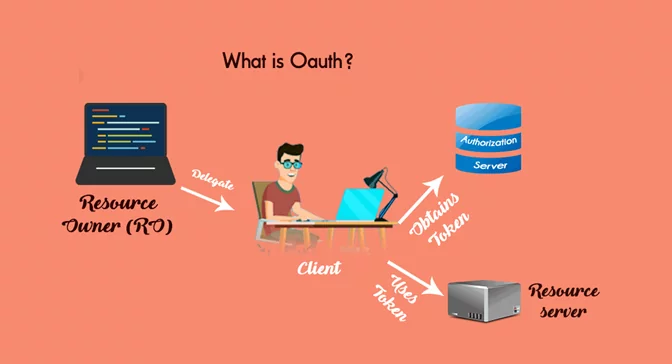
What is OAuth?
OAuth is a mechanism that is used by many companies like Amazon, Google, Microsoft, etc., which allows the user to view or share their account information with a third-party application. It is a commonly used open standard delegation which grants any user to access their information over other websites without the need to authenticate every single time.
Fig: What is OAuth?
Why is it used?
In essence, OAuth provides access directly to the main application to perform functions to fetch data or use it your account, from another application.
It is basically used to authenticate into the application directly through third-party sources without having a registered account in that application.
Entities used in OAuth 2.0.
Resource Owner: The resource owner is the user/entity granting access to their protected resource, such as their Google account contacts.
Resource Server: The server which handles the authenticated request, which the application forwards after it has obtained the access token from the resource owner.
Client Application: The component requesting authorization from the resource owner is the client application.
Authorization Server: Server which issues the access token to the client application when they successfully authenticate the resource owner.
Scope: Scope defines the level of accessing the client requests from the resource owner.
Redirect_Uri: The URL to which the user is redirected when the authorization is completed. Usually, this will the URL of the previously registered service.
State: While going back and forth the authorization server, the state is a parameter that persists the data between the user and the authorization server. Mostly it is recommended this value to be unique so that this value also provides a protection mechanism against CSRF.
Grant_type: The grant type is a parameter that specifies the grant type and the token is returned.
Now let us see the demo application from Port swigger lab exploiting this vulnerability.
• Capture the following request in the burp suite by clicking on login with social media.
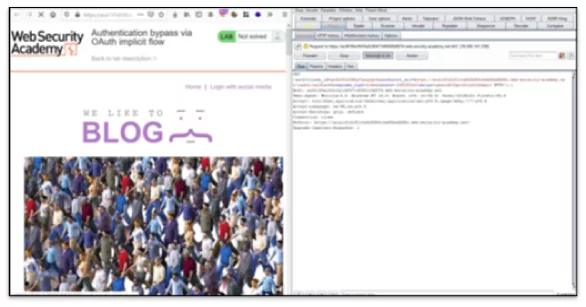
Fig:1.1 Intercepting the request.
• In the next request enter valid credentials as given and capture the request.
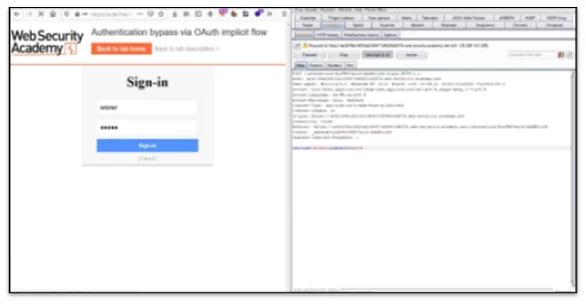
Fig 1.2 Enter the given credentials.
• Forward the request and you can see the email id parameter of the user.

Fig 1.3 Next request
• Change Email id to victim email and forward the request.
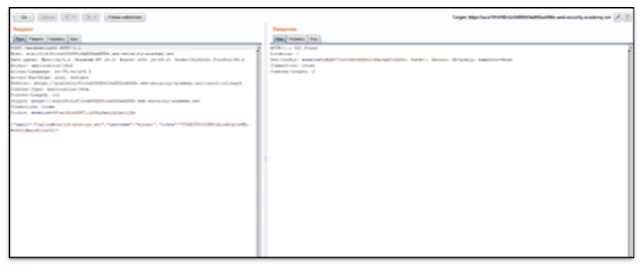
Fig 1.4 Email change
• The attacker can successfully login into the victim account and resulting in a complete account takeover.
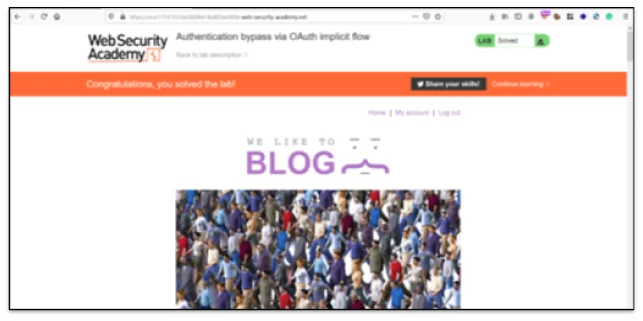
Fig 1.5 Authenticated Successfully
Mitigation:
1. The client applications require to the whitelist of valid redirect Uri’s.
2. Use strict byte-by-byte comparison for validating the URI in incoming requests.
3. Use pattern matching which will allow only the exact and complete matches.
4. This will prevent the attackers from accessing the pages on the domains which have been whitelisted.
5. Enforce the use of the state parameter. The value of this parameter should be bound to the user’s session, including some unguessable, session-bound data like has which contains the session cookie. This is will also provide an added protection against CSRF-like attacks, also making it a difficult task for an attacker to steal the authorization codes.
Thank you.
For more help please visit our website.
Author,
Saketh Reddy Malepu
Attack & Pentest Team
Varutra Consulting Pvt. Ltd.