VoIP Penetration Testing Part – III

In the previous tutorial VoIP Penetration Testing Part-II we have learnt on how to do scanning against VoIP Server. In this tutorial we will configure the softphone which we will be using for further attacks.
Softphone Configuration For VoIP Penetration Testing :
Lab Setup :
- VoIP Server -192.168.0.4
- Two Softphone on two systems running on VMware’s
Steps :
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
1. The main task is to configure Softphone. Download Zoiper Softphone from below link.
2. Open your browser and enter IP address of your server. In my case it is http://192.168.0.4
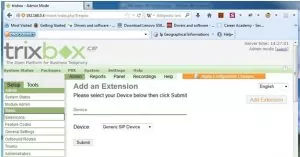
Click on PBX > PBX Settings > Extensions
3. Select Generic SIP Device and click on submit.
4. You need to enter following detail :
User Extension: ( 202,302,402 and so on)
Display Name: (Enter the name of your choice)
5. Secret: (Enter string of your choice)
6. Click on Add Extension.
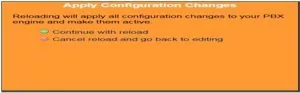
In my case I have added two extensions as shown below. After adding extension, do not forget to click on the Apply Configuration Changes button.
7. After clicking Apply Configuration Changes button, you will see following popup. Click on Continue with reload.
8. Now let us configure the Softphone.
9. Enter the password, which you have entered in the Secret field at the time of adding user on server. In username field enter the User extension that you have added in step 4 (E.g:100,200,) and in Domain field enter the IP address of Server. After submitting this information click on apply.
10. After Successful registration you will see following screen
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}
Note: Same way we have configured one more softphone for user ‘wagh’.
11. Now let us try to call from user wagh to user sachin to check whether the setup is working properly.
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}
It was observed that call from user wagh to sachin was successful.
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}
SIP User Extension Enumeration :
The next and last step in information gathering is enumeration. It involves probing the identified services for known weaknesses. Enumeration involves getting information such as user account names, misconfigured shared resources, and software versions. One of the most common enumerations is against SIP protocol.
Targeting SIP proxy or location server will provide user registration and presence.
Lab Setup :
1. Client where the softphone is installed – 192.168.0.5
2. Server IP – 192.168.0.7
Before starting the practical, let us understand the SIP Request method and Response code.
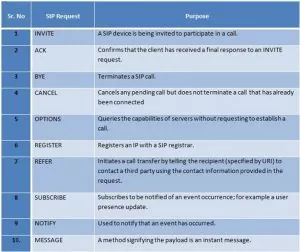
SIP Request Method:
Methods of enumeration:
- REGISTER – username enumeration
- INVITE – username enumeration
- OPTIONS – username enumeration
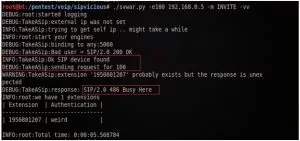
1. Username enumeration using REGISTER request method:
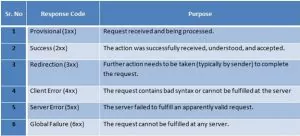
This involves gaining information about valid accounts registered on the VoIP network using error messages from SIP proxy or registration servers. Attacker sends SIP REGISTER requests to the proxy or registration server with the specified extension and checks for the response status code if and extension is valid. When the 401 Unauthorized or 407 Proxy Authentication Required or 200 OK is received, the SIP account username was valid. If 403 Forbidden is received, the SIP account username was invalid.
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}
Normal
0
false
false
false
EN-US
X-NONE
X-NONE
SIPVicious is a suite of command-line tools that works on Linux, Mac and Windows platforms.
The suite of tools includes
- Svmap
- Svwar
- Svcrack
- Svreport
- Svcrash
For extension scanning, the svwar.py tool is used, which supports REGISTER, INVITE and OPTIONS scans. It supports all three extension enumeration methods, the default method for enumeration is REGISTER.
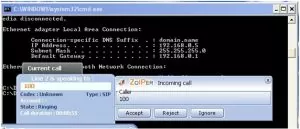
2. Username enumeration using INVITE request method:
Sending an SIP INVITE request, means initializing a call to target with valid user usually generates 100 Trying and 180 Ringing messages, which means the SIP username extension was valid. When 404 Not Found is received, it means the SIP username extension was invalid. INVITE requests can be sent directly to phones if their IP addresses are known.
You will see calling screen on 192.168.0.5 System when you send INVITE request.
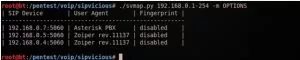
3. Username enumeration using OPTIONS request method:
The OPTIONS method is the most stealthy and effective methods.
The OPTIONS is used to advertise supported message capabilities and legitimate users.
Depending on if the received message was 200 OK or 404 Not Found, you can differentiate the valid and invalid SIP username extensions.
Svmap allows specifying the request method, which is being used for scanning.
The default method is OPTIONS.
In next and last tutorial we will learn on exploitation phase with various attacks.
Written By,
Attack & PenTest Team,
Varutra Consulting
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-priority:99;
mso-style-qformat:yes;
mso-style-parent:””;
mso-padding-alt:0in 5.4pt 0in 5.4pt;
mso-para-margin-top:0in;
mso-para-margin-right:0in;
mso-para-margin-bottom:10.0pt;
mso-para-margin-left:0in;
line-height:115%;
mso-pagination:widow-orphan;
font-size:11.0pt;
font-family:”Calibri”,”sans-serif”;
mso-ascii-font-family:Calibri;
mso-ascii-theme-font:minor-latin;
mso-hansi-font-family:Calibri;
mso-hansi-theme-font:minor-latin;
mso-bidi-font-family:”Times New Roman”;
mso-bidi-theme-font:minor-bidi;}