Code Obfuscation

Abstract
In this paper, we came up with a basic understanding of Code Obfuscation – A Code Protection Technology which need anti-reverse engineering transformations to change programs in such a way that tools and approaches for program analysis become ineffective.
What is Code Obfuscation?
The word Obfuscation accurately means ‘making something less obvious and harder to get it.
Code obfuscation is a group of program alteration that makes program code and/or its execution challenging to analyze by deterring both manual and automated inspection. Obfuscating source code makes it very difficult for hackers to understand. It is also used to prevent the reverse-engineering of software.
Obfuscation is NOT similar as encryption. Encryption is used where we transform data in order to keep it secret from others. Whereas, the purpose of obfuscation is to make it difficult for humans to understand the data. Encrypted code always needs to be decrypted before execution, while de-obfuscation does not require for an obfuscation code during its execution.
Why use a Code Obfuscator?
- Once you develop an application (Any Application), your aim is to make it tougher for attackers to review the code and analyze the application.
- It is very important to hide business logic and code to form it tougher for attackers to achieve access and begin debugging and tampering together with your application. (They usually repackage an application with malicious code.)
- Code obfuscation will drastically decrease file size, and download time can also be reduced considerably. (Consider JavaScript as an example.)
- Folks are creating careers out of reverse engineering—Therefore, you wish to form it as tough as possible to discourage them.
- Industries, which are developing applications, might not wish that users could easily get their source code.
How does Code Obfuscation Work?
Code obfuscation comes up with completely different techniques, each building on top of the other, thus rendering the code is unintelligible.
Some typical samples of obfuscation and application security techniques include:
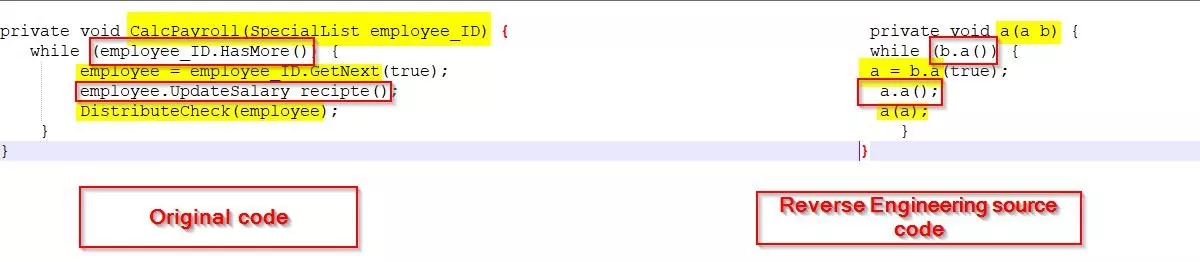
Rename Obfuscation: By altering the name of methods and variables makes the decompiled source tougher for people to understand but it doesn’t alter program execution. The new names will utilize totally different schemes like “a”, “b”, “c”, or numbers, unprintable characters or invisible characters and names will be full as long they need a totally different scope. Name obfuscation may be a basic rework that’s utilized by most .NET, iOS, Java and mechanical man obfuscators.
Fig: 1(Rename obfuscation)
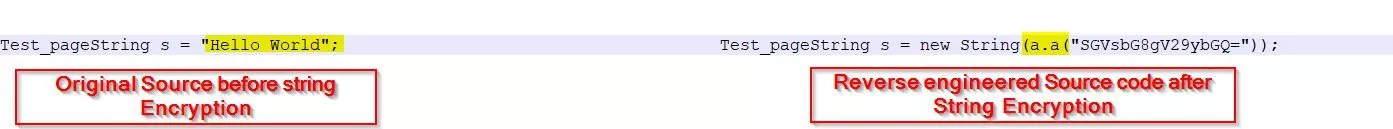
String Encryption: All strings are clearly determinable and decipherable in managed executable form. Even once methods and variables are renamed, strings can be used to locate a critical code section in the reference of a binary string. This includes messages (especially error messages) that are shown to the user. To run an efficient barrier against this sort of attack, string cryptography hides strings within the executable format and just restores their original value once required. Decrypting strings at runtime sometimes incurs a small runtime performance penalty.
Fig: 2(String obfuscation)
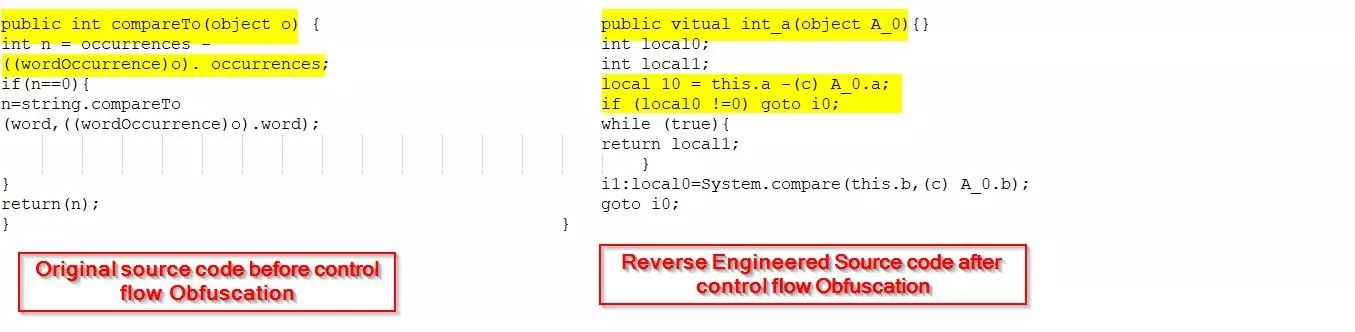
Control Flow Obfuscation: Control flow obfuscation creates conditional, branching, and repetitive theories that turn out valid possible logic. However, it yields dissimilar results once decompiled. It makes decompiled code incredibly tough for a hacker to understand. These techniques might have an effect on the runtime performance of a format.
Instruction Pattern Transformation: It converts common guidelines created by the compiler to alternate and less obvious concepts. These are impeccably legal machine language commands that will not map cleanly to high-level languages like Java or C#. One example is temporary variable caching that controls the stack-based nature of the Java and .NET runtimes.
Dummy Code Insertion: Inserting code into the practice that doesn’t have an effect on the logic of the program. However, it decompiles or makes reverse designed code which is tougher for further research.
Example Dummy variables:
Student Favourite Game: Ludo, PUBG & Indoor game.
Fig: 4(dummy code insertion)
Dead Code and Metadata Removal: By eliminating debug information, non- essential metadata and unused code from applications generate less important and smaller assembly size on disk, which improves the load time during execution.
Binary Linking/Merging: These changes combine multiple input executables/libraries into one or additional output binaries. Linking can build your application smaller, mostly once used with renaming and pruning. It can make simple scenarios and may reduce information accessible to hackers.
Opaque Predicate Insertion: Obfuscates by adding conditional branches that continuously judge to acknowledge results that can’t simply be determined via static analysis. This can be some way of introducing doubtless incorrect code which will never really be dead. However, it confuses attackers to attempt or understand the decompiled output.
Anti-Tamper: An obfuscator will inject application protection into your code to verify your application has not been tampered by any approach. If meddling is detected, it will halt the request, limit the functionality, invoke random crashes or perform the other custom action. It would additionally send a message to a service to supply details regarding the meddling detected.
Anti-Debug: When a hacker is making an attempt to pirate or counterfeit your app, steal your information or alter the behavior of an essential piece of infrastructure set, they will nearly begin with reverse engineering and stepping through your application with a debugger. An obfuscator will layer in application protection by injecting code to find if your production application is executed among a computer program. If a computer program is employed, it will corrupt sensitive information (protecting it from theft), invoke random crashes (to disguise that the crash was the results of a right check) or perform the other custom actions. It also sends a message to a service to deliver a signal.
Drawbacks of using an obfuscator
- In some cases, antivirus computer code like AVG Antiviruses can provide you with a warning once you visit a web site that has been obfuscated (as one in all the needs of obfuscation is to cover malicious code). However, with the case, wherever obfuscation has been doled out of security reasons. It’s going to deter users from victimization or visiting a website.
- Several techniques might negatively have an effect on the performance of algorithms.
You will be able to use the following tools for a particular language:
.Net: Dotfuscator, ILprotector
JavaScript: JavaScript obfuscator, Jscrambler
Android: ProGuard
Conclusion
Although obfuscation will build reading and reverse-engineering a program hard-hitting and long, it’s necessary to retain in mind. Code obfuscation will be a decent job of obscuring source code. There is no obfuscator that guarantees more security. Therefore, in cases where security is very important, you’ll have to use other trials, including various encryption schemes.
Author,
Attack & PenTest Team
Varutra Consulting