Introduction to Secure Software Development Life Cycle

The most effective way to reduce application security risk is to implement a formal development process that includes security best practices to avoid application vulnerabilities.
Secure Development process and Security Testing are powerful tools to monitor and search for application flaws and they should be used together to increase the security level of business critical applications/software’s.
What Is Application Security?
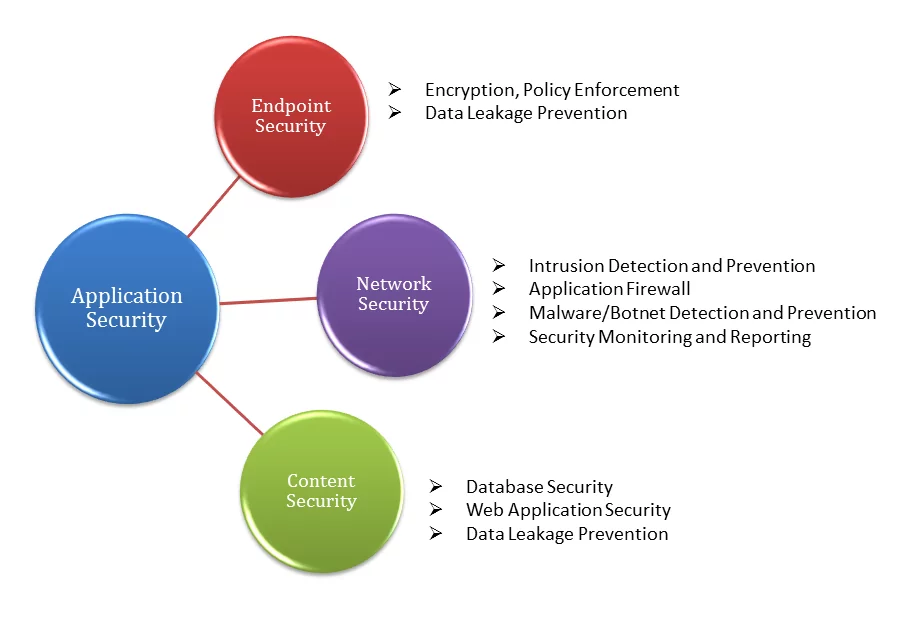
Application security helps to eliminate potential attacks to business websites and applications when running internally or publicly on the Internet. This process reduces unexpected risks, financial loss and builds customer trust as well as increases brand value as a result.
Application security is a process that begins from the application development lifecycle to ensure the highest security possible of the development process (coding), the system, hardware the application runs on and the network it uses to connect, authenticate and authorize users.
Fig: Application Security
What is Secure Software Development Life Cycle (SSDLC)?
SDLC stands for Software Development Life Cycle. SDLC is the process consisting of a series of planned activities to develop the software products. The life cycle defines a methodology for improving the quality of software and the overall development process.
What is SSDLC (Secure Software Development Life Cycle)?
The S-SDLC stands for Secure Software Development Lifecycle (SSDLC) is a software development process that helps developers builds more secure software and reducing development cost while address security compliance requirements.
The only way to fully protect applications is to build security into the applications themselves. According to formal S-SDLC methodology, organizations define an end-to-end process of secure software coding and testing practices.
The entire software development lifecycle when embedded with security features is known as “Secure Software Development Lifecycle“.
What is the Need of SSDLC?
As an old saying goes – “Need is the mother of invention” – This is applicable for S-SDLC as well. There are multiple reasons why programs like these have gained popularity.
Hackers or attacker can break into an organizations network through various routes and one such route is the application host. If applications are hosted by organization are vulnerable, it can lead to serious consequences.
This is where S-SDLC comes into the picture. While employing a team of ethical hackers helps, having processes like S-SDLC can help organizations in addressing the above discussed issues in a much more cost-efficient manner as identifying security issues earlier in the development life cycle.
The Heartbleed Bug is a perfect example of what could go wrong if a software provider does not embed security from the beginning of a product’s development.
All developers test their software. They test the individual functions, methods, and modules they write to ensure it works as advertised. System integrators test the entire system to ensure the same.
What exactly does The Secure SDLC?
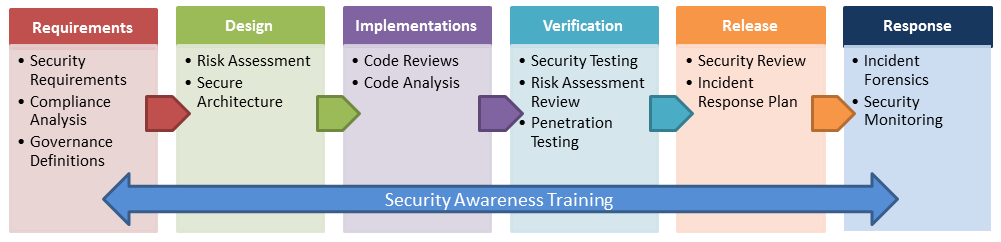
Most SDLC models generally follow these steps in order: Gather Requirements, Design, Implement, Test and Release. The Secure SDLC includes security checks at all these steps. This includes Threat Modeling in the Requirements and Design phases, Static Application Security Testing (SAST) at the Implement and Test phases, and Dynamic Application Security Testing (DAST) at the Test and Release phases.
Threat Modeling is the process by which threats to the application are discovered and documented so they can be mitigated during the implementation phase. At the beginning of this process testers/ analysts learn how the application is intended to work by reviewing the requirements and design of the application. Depending on the intentions of the application, and the type of data stored, transmitted or processed on the application, and by utilizing an attacker’s mentality they develop scenarios and use cases which show how an entity might attack the software being developed. These models are then reviewed and new requirements and design features are put in place to mitigate the threats to the application.
Brief Explanation of S-SDLC:
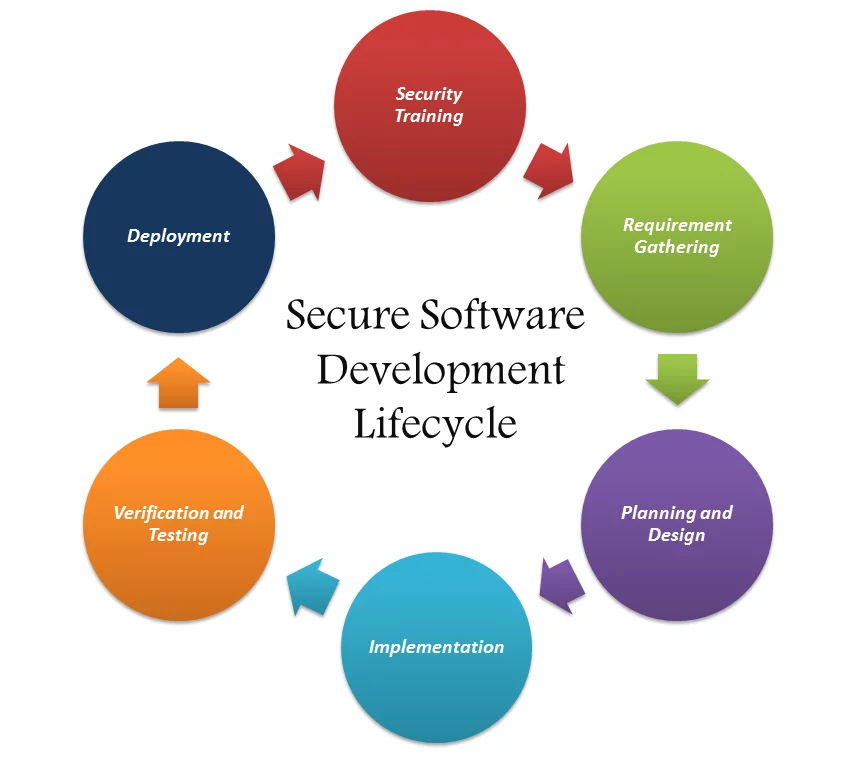
Application Security is often mapped into key phases during Secure Software Development Life Cycle. Each phase of the S-SDLC is mapped with security activities.
Figure: Secure Software Development Life Cycle(S-SDLC)
Following are the phases of secure software development life cycle:
1. Core Security Training Phase: Training to software development teams on application security, organizational and to make sure the team stays informed of the latest updates in security and privacy. Foundational concepts for building better software include secure design, threat modeling, secure coding, security testing, and best practices surrounding privacy.
Software development teams on application security, organizational policy and capabilities to make sure the team stays informed of the latest updates in security and privacy.
The Security Awareness Training for Software Developers includes the following modules:
- Secure Coding Best Practices based on the OWASP Top 10
- Defensive techniques, ideally presented as a framework (e.g. OWASP ESAPI)
- Web Service and Web 2.0 Threats
- Black-box Application Assessment Tools
- Best practices for secure code reviews
- Cryptography, Hashing and Obfuscation
- Input Validation Strategies
- Understanding Threats: Threat Modeling
2. Requirements Gathering Phase: These should be gathered by the same personnel, in fact. Since the idea of secure development is to start at the very beginning of the coding, it helps to have both the feature requirements and the security requirements side by side during planning.
- Security Requirements
- Risk Assessment
3. Planning and Design: Consider security and privacy in the initial design of new products and features and permits the integration of security in a way that minimizes disruptions to plans and schedules.
- Identify Design Requirements from security perspective
- Architecture & Design Reviews
- Threat Modeling
Consider security and privacy when designing new features of products and integrate security into applications with minimal disruption.
4. Implementation: Avoid coding issues that could lead to vulnerabilities and leverages state-of-the-art development tools to assist in building more secure code. Analyzing the source code prior to compile provides a scalable method of security code review and helps ensure that secure coding policies are being followed.
- Make certain SQL queries are parameterized correctly and that input is validated
- Ensure developers are performing proper validation to prevent Cross Site Scripting
- Coding Best Practices
- Perform Static Analysis
- Secure Data Storage
- Secure Access Control
Prevent coding errors from creating vulnerabilities as well as use sophisticated development tools to build more secure code.
5. Verification and Testing: Run-time verification of software applications to ensure that functionality works as designed. Apply appropriate verification to software applications and make sure they produce proper functionality as defined in the initial design.
- Vulnerability Assessment
- Fuzzing
Apply appropriate verification to software applications and make sure they produce proper functionality as defined in the initial design.
6. Deployment: Response plans and protocols to address new threats that emerges over time. Certifying software prior to a release helps ensure security and privacy requirements were met.
- Server Configuration Review
- Network Configuration Review
Make sure to have the right plans or protocols for response when new threats emerge over time.
Best Practices for SDL
- Define security training policy which addresses requirements based on job responsibilities
- Define Security Requirement Guidelines which for applications
- Define and implement Risk Assessment Practices
- Define Minimum level of security and privacy quality
- Define Secure architecture design guidelines
- Perform attack surface analysis
- Perform threat modeling in design phase
- Define secure coding guidelines
- Define Secure Coding Checklist
- Define secure code review checklists
- Define unsafe functions, cryptographic algorithms
- Perform application security testing
- Define secure deployment policy
- Define guidelines and procedures for secure deployment
- Define security benchmark such as CIS, DISA for application environment configuration
Benefits of Secure Software Development Life Cycle (SSDLC):
- Build More Secure Software
- Help Address Security Compliance Requirements
- Reduce Costs of Maintenance
- Awareness of potential engineering challenges caused by mandatory security controls
- Identification of shared security services and reuse of security strategies and tools
- Early identification and mitigation of security vulnerabilities and problem
- Documentation of important security decisions made during the development
References:
http://www.microsoft.com/security/sdl/process/training.aspx
http://www.microsoft.com/security/sdl/default.aspx
https://www.owasp.org/index.php/Secure_SDLC_Cheat_Sheet
AUTHOR:
Security Consultant, Varutra Consulting, Pvt. Ltd.