The Ripple Effect of Supply Chain Attacks on Global Commerce
In today’s globalized world, supply chains are the backbone of commerce, connecting businesses across continents. But what happens when those supply chains are targeted by cyber criminals? The ripple effect of a supply chain attack can be felt far and wide, causing disruptions, financial losses, and even reputational damage. In this blog post, we’ll dive into the world of supply chain attacks and explore their impact on global commerce.
What is a supply chain attack?
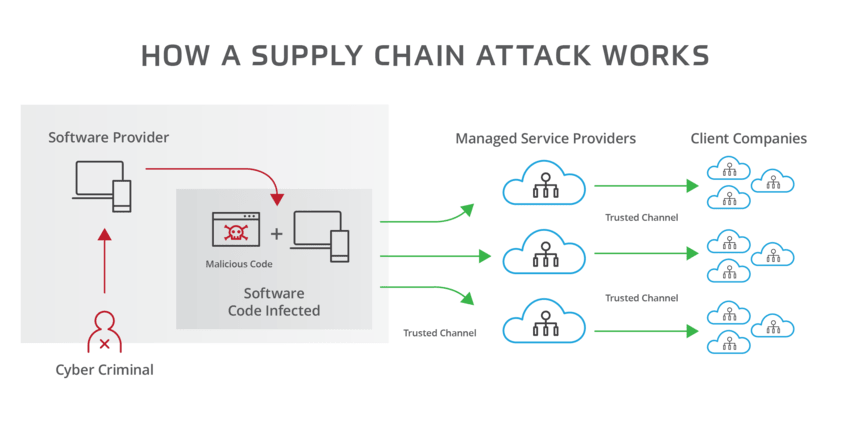
In simple terms, a supply chain attack is a cyber-attack that targets a company’s third-party vendors, suppliers, or partners to gain access to the company’s internal systems. The attack often involves infiltrating a trusted vendor’s network, compromising their software, and using it as a pathway into the target company’s network.
Supply chain attacks have become more prevalent and sophisticated in recent years, and they are challenging to detect and prevent. These attacks can target any industry, from manufacturing to healthcare, and any size of a company, from small businesses to global corporations.
How Supply Chain Attacks Work?
Supply chain attacks typically begin with the hackers identifying a vulnerable third-party supplier. This supplier could be a software vendor, a cloud provider, or a logistics partner. The attackers then exploit vulnerabilities in the supplier’s system to gain access to sensitive information or to introduce malware into the system. Once they have gained access, the hackers can move laterally through the supplier’s network, eventually reaching the target organization’s network.
https://www.pratum.com/blog/514-how-software-supply-chain-attacks-work
Examples of Supply Chain Attacks
The impact of supply chain attacks can be seen in several high-profile incidents in recent years. Here are just a few
examples:
a. SolarWinds Attack
One of the most significant supply chain attacks in recent years was the SolarWinds hack, which was discovered in December 2020. SolarWinds is a software company that provides IT management solutions to government agencies and Fortune 500 companies. The attackers infiltrated SolarWinds’ systems and introduced a backdoor into the company’s software update process. This backdoor allowed the hackers to gain access to the networks of SolarWinds’ customers, including multiple U.S. government agencies.
b. Kaseya Attack
Another recent supply chain attack was the attack on the IT services company, Kaseya, in July 2021. Kaseya provides IT management solutions to small and medium-sized businesses. The attackers exploited a vulnerability in Kaseya’s software and used it to deploy ransomware to the company’s customers. This attack affected over 1,500 businesses in more than 17 countries.
c. Target Data Breach
In 2013, the retail giant Target suffered a massive data breach that resulted in the exposure of 40 million customer credit and debit card numbers, as well as the personal information of 70 million customers. The breach was caused by a cybercriminal who gained access to Target’s network through a third-party vendor. This incident is just one example of how supply chain attacks can have a ripple effect on global commerce.
How do you detect a Supply Chain Attack in organizations ?
Detecting a Supply Chain Attack can be challenging, but here are some methods organizations can use to detect them:
• Monitor network activity for unusual or suspicious patterns of behavior, such as unexpected network traffic or connections to unknown IP addresses.
• Use intrusion detection and prevention systems (IDPS) to monitor for potential indicators of a Supply Chain Attack, such as malicious code or suspicious network activity.
• Conduct regular vulnerability assessments and penetration testing to identify any vulnerabilities in your organization’s systems and software that could be exploited in a Supply Chain Attack.
• Use endpoint protection software to detect and respond to potential threats on individual devices and endpoints.
• Keep an eye out for unusual changes in software and system configurations, such as unauthorized software installations or changes to firewall rules.
• Monitor your supply chain partners’ security posture and track their adherence to your organization’s security requirements.
• Utilize threat intelligence services to stay up-to-date on the latest Supply Chain Attack tactics and techniques.
• Conduct regular security audits of your supply chain partners and vendors to ensure they are meeting your organization’s security requirements.
• Implement logging and monitoring capabilities across all systems and devices to track all activity and detect any anomalies.
• Train employees to recognize potential indicators of a Supply Chain Attack, such as suspicious emails or software updates.
Types of Supply Chain Attacks
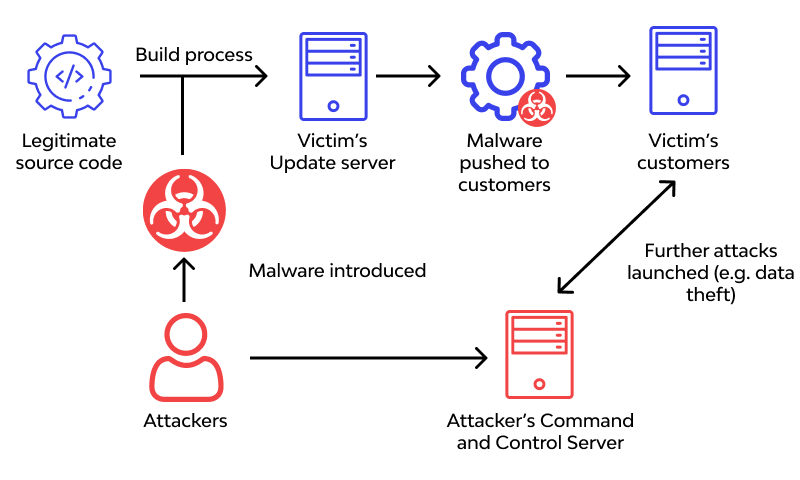
Malware injection
Malware injection is a type of cyber attack where malicious code or software, also known as malware, is surreptitiously inserted into a software application or hardware component that is distributed through the supply chain. This allows attackers to gain unauthorized access to the target’s network and cause harm.
 https://www.opendatascience.com/3-ways-to-protect-your-code-from-software-supply-chain-attacks
https://www.opendatascience.com/3-ways-to-protect-your-code-from-software-supply-chain-attacks
Third-party software :
Cyber attackers leverage vulnerabilities in third-party software to gain unauthorized access to a network and execute their attack.
Counterfeit hardware components :
The attackers use these components to gain access to the network and carry out their nefarious activities.
Man-in-the-middle (MITM) attacks :
Man-in-the-middle (MITM) attacks are also commonly used in supply chain attacks. In this method, attackers intercept and modify data transmitted between the target organization and suppliers, which enables them to inject malware and other malicious code into the network.
Physical tampering :
This can involve manipulating devices or equipment either during the manufacturing process or while in transit, granting the bad actors access to the network after the compromised device or equipment has been installed by the intended target.
Insider threats :
Insiders, such as employees of suppliers or shipping companies, may carry out attacks on the organization’s supply chain, resulting in damage to the target organization’s network and reputation.
Impact of Supply Chain Attacks on Global Commerce
Financial Losses
PSupply chain attacks can cause significant financial losses for companies. According to a survey by Ponemon Institute, the average cost of a data breach for a U.S. company is $8.19 million, and supply chain attacks can increase this cost by up to $1.1 million.
In addition, supply chain attacks can result in operational downtime, loss of revenue, and legal fees associated with resolving the breach.
Disruption of Operations
A supply chain attack can also cause significant disruption to a company’s operations. This can include:
• System downtime or unavailability
• There may be unexpected interruptions in the production or delivery process, resulting in delays.
• Inability to access critical data or systems
For example, the SolarWinds attack affected over 18,000 organizations, including government agencies and Fortune 500 companies, causing widespread disruption and chaos.
Reputational Damage
A supply chain attack can damage a company’s reputation, resulting in the loss of customer trust and loyalty. A breach can lead to negative media coverage, which can spread quickly on social media and affect a company’s public perception.
For example, in 2017, the credit reporting agency Equifax suffered a supply chain attack that resulted in the theft of personal data of 147 million consumers. The breach caused widespread outrage, and Equifax’s reputation was severely damaged.
National Security Risks
Supply chain attacks can also pose a risk to national security. Attackers can use compromised supply chains to gain access to critical infrastructure, such as energy or transportation systems, and cause significant disruption.
For instance, in 2020, the U.S. government issued an executive order banning the use of technology from Chinese companies Huawei and ZTE in government contracts, citing national security concerns related to potential supply chain attacks.
Indirect Effects on the Economy
Supply chain attacks can have indirect effects on the economy, beyond the immediate impact on individual companies. These attacks can disrupt the global supply chain, leading to shortages of goods and services and higher prices for consumers.
For example, in 2021, a supply chain attack on the Colonial Pipeline, a major U.S. fuel pipeline, caused a shutdown that lasted several days, resulting in fuel shortages and price increases in multiple states.
Regulatory and Legal Consequences
In addition to the financial and operational impacts, a supply chain attack can also have legal and regulatory consequences. Companies may be subject to fines and penalties for failing to adequately protect their customers’ data, and may also face lawsuits from customers or other affected parties. This can lead to further financial losses and reputational damage.
Loss of Customer Trust
Supply chain attacks can also damage a company’s reputation and result in a loss of customer trust. It is the responsibility of companies to ensure that their customers’ personal and financial information is kept confidential and secure. If a company fails to do so, customers may take their business elsewhere. In the case of Target, the data breach resulted in a 46% drop in profits and a loss of customer trust.
Disruption of Supply Chains
Supply chain attacks can also disrupt the supply chains of companies, resulting in delays in the delivery of goods and services. This disruption can have a domino effect, causing delays in other industries that rely on the affected company’s products or services. For example, the 2017 WannaCry ransomware attack disrupted the production of Renault and Nissan cars, as the attack affected the companies’ supply chain operations.
Steps to Mitigate Supply Chain Attacks
Given the significant impact of supply chain attacks, it is essential for companies to take steps to mitigate their risks.
There are several effective best practices that organizations can employ to mitigate supply chain attacks. These include :
Vendor Risk Management
• Companies should implement a vendor risk management program that includes due diligence and ongoing monitoring of third-party vendors. This program should include:
• Conducting background checks on potential vendors.
• Reviewing vendor security policies and procedures.
• Conducting regular security assessments of vendor systems.
• Monitoring vendor activity for any signs of suspicious behavior.
Cybersecurity Awareness Training
Employee cybersecurity awareness training can help prevent supply chain attacks. Organisations should educate employees on how to identify and report suspicious emails, phishing attempts, and other cyber threats.
Cybersecurity Frameworks
Businesses should adopt industry-standard cybersecurity frameworks, such as NIST or ISO 27001, to establish a baseline for their security controls. These frameworks can help organizations identify vulnerabilities and implement best practices to mitigate risks.
An incident response plan is critical in the event of a supply chain attack. This plan should include procedures for detecting and responding to attacks, as well as strategies for containing and mitigating the damage caused by the breach.
Continuous Monitoring
Continuous monitoring is crucial in detecting and preventing supply chain attacks. Firms should implement tools that can monitor their networks and systems for any signs of suspicious activity.
Conduct Risk Assessments
Companies should conduct regular risk assessments to identify vulnerabilities in their supply chain. This includes identifying third-party vendors and assessing their security protocols.
Implement Security Protocols
Companies should implement security protocols, such as multi-factor authentication and encryption, to protect their networks and the networks of their third-party vendors.
Regular Security Audits
Companies should conduct regular security audits to ensure that their security protocols are up-to-date and effective.
Cyber Insurance
Cyber insurance can provide financial protection in the event of a supply chain attack. It can cover the costs associated with data breach response, legal fees, and financial losses resulting from the attack.
Conclusion
In conclusion, supply chain attacks can have a significant ripple effect on global commerce. Companies must take steps to protect their networks and the networks of their third-party vendors to prevent these types of attacks. By conducting risk assessments, implementing security protocols, monitoring network activity, and conducting regular security audits, companies can reduce the risk of a supply chain attack and protect their customers and their business.
Research, References & Resources
https://www.helpnetsecurity.com/2021/12/01/supply-chain-attacks-protection
https://www.sciencedirect.com/science/article/pii/S1755581721000134
https://www.keepersecurity.com/threats/supply-chain-attack.html
https://www.upguard.com/blog/supply-chain-attack
https://www.techtarget.com/searchsecurity/definition/supply-chain-attack
https://crashtest-security.com/supply-chain-attack
https://www.upguard.com/blog/supply-chain-attack
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-a-supply-chain-attack
https://www.csoonline.com/article/3191947/supply-chain-attacks-show-why-you-should-be-wary-of-third-party-providers.html
https://www.businessnewsdaily.com/supply-chain/smb-cyberattacks
https://www.cisa.gov/sites/default/files/publications/defending_against_software_supply_chain_attacks_508_1.pdf
https://www.dni.gov/files/NCSC/documents/supplychain/Software_Supply_Chain_Attacks.pdf
https://www.crowdstrike.com/cybersecurity-101/cyberattacks/supply-chain-attacks
https://www.mitre.org/sites/default/files/publications/supply-chain-attack-framework-14-0228.pdf