Understanding Deep and Dark Web and Exploring Its Threats

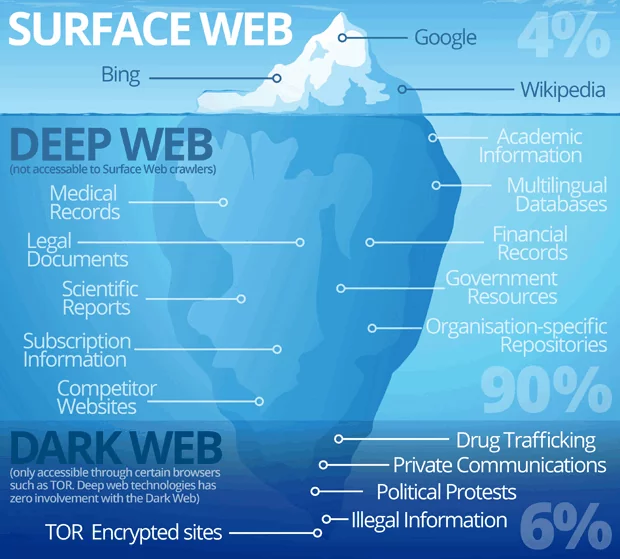
The internet comprises millions of web pages, servers, and databases operating 24/7. But the web we use is often addressed as the “visible” internet called the surface internet or the open web. The sites that can be found using the search engines like Bing, Google, Baidu, etc., are part of the surface web. If the internet is like an iceberg, then the surface web is referred to as the iceberg’s tip. The rest of the iceberg is the non-visible web and comprises both the deep and dark web.
Source: The SSL Store
What are the surface web, deep web, and dark web?
Surface Web
The surface web or open web is the visible internet; from the analytical point of view, it makes up less than 5% of the entire internet. Most websites are typically browsed using traditional browsers like Internet Explorer, Firefox, Google Chrome, and Opera. These websites are usually registered with the operators like “.org,” “.com,” “.net,” and more and are indexed. In addition, there is a procedure called “crawling” through which search engines like google index the website. According to the 2022 Siteefy report, there are currently 14 billion websites operating globally.
Deep Web
The deep web is below the surface web and comprises more than 90% of the websites. This hidden web is so massive that it is impossible to determine exactly how many websites are active at any time. For instance, if we consider big search engines fishing boats, they can only catch hold of websites if they are incredibly close to the surface. Everything else, i.e., private databases to criminal matters, is inaccessible. A particular portion of the deep web may be considered illegal though most of the data there may be considered safe and legal. The websites on the deep web are mostly password protected and cannot be browsed using search engines as they are not indexed.
The type of data that is present on the deep web:
- Databases: It is a composition of private and public file collections that are not connected to other areas of the web but can only be searched by looking out for the database itself.
- Intranets: It comprises several internal networks for government, hospitals, organizations, and the educational sector that use internal communication to communicate and control their organizations.
While diving further into the deep web, that is a little away from the light and dangerous. Some users like to dive further into the deep web as it allows them to bypass the local constraint and access services that are generally unavailable in their regional areas. If they dive further, users will encounter dangerous activities and information. Tor websites are usually present this far in the deep web and can even be deemed as the dark web. The anonymous browser can only access it.
Dark Web
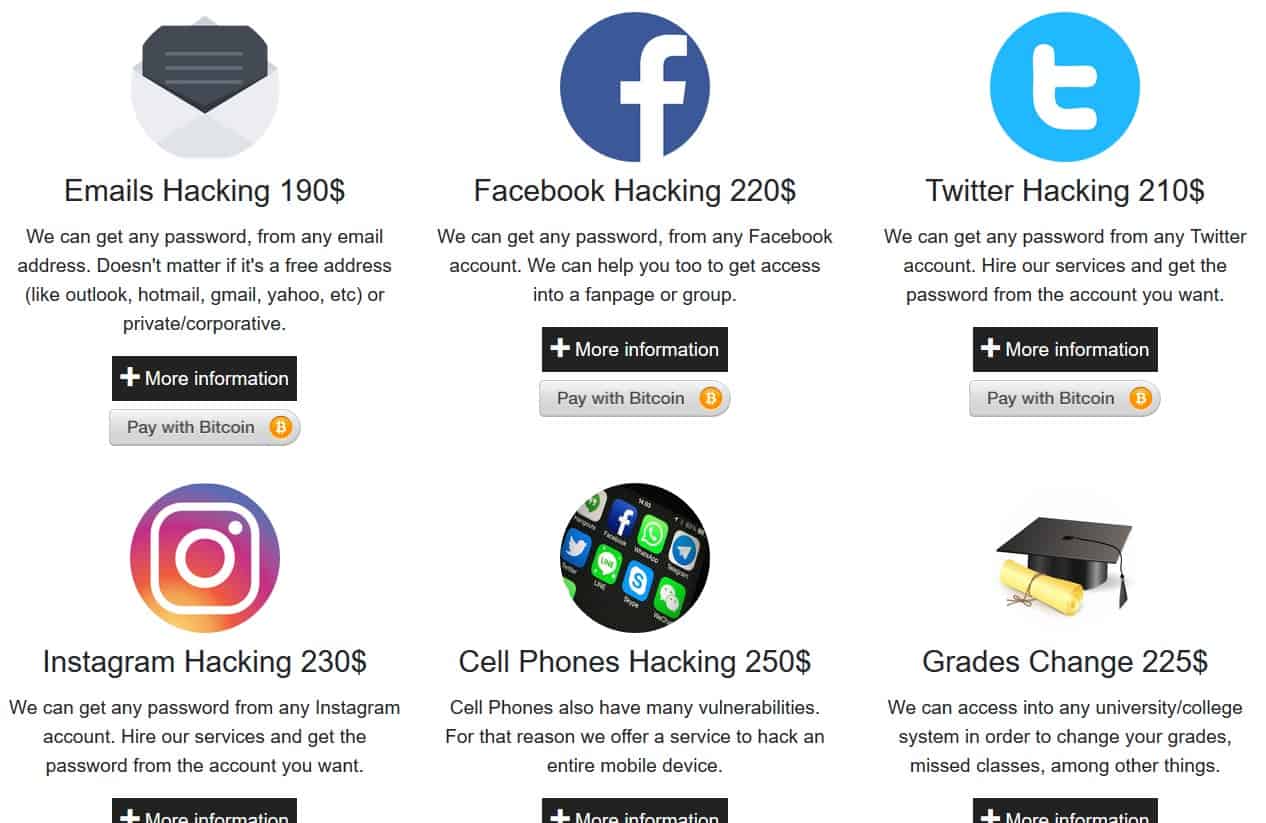
The dark web is the rear of the iceberg if the internet is considered an iceberg. It is a place where websites can only be browsed using specialized browsers due to their explicit content. It is done to keep the browsing activity anonymous and private. It is helpful in legal and illegal activity or evading regional censorship. However, it is a highly concealed part and often considered an unknown haven. The dark web is often linked to criminal or unlawful activity, extending to trading sites where users can buy illicit goods and services. It can be pretty much gruesome, and some people even call this place to be a place where humanity’s darkest sides emerge. The Silk Road hub is the central marketplace for illicit items to be bought and sold.
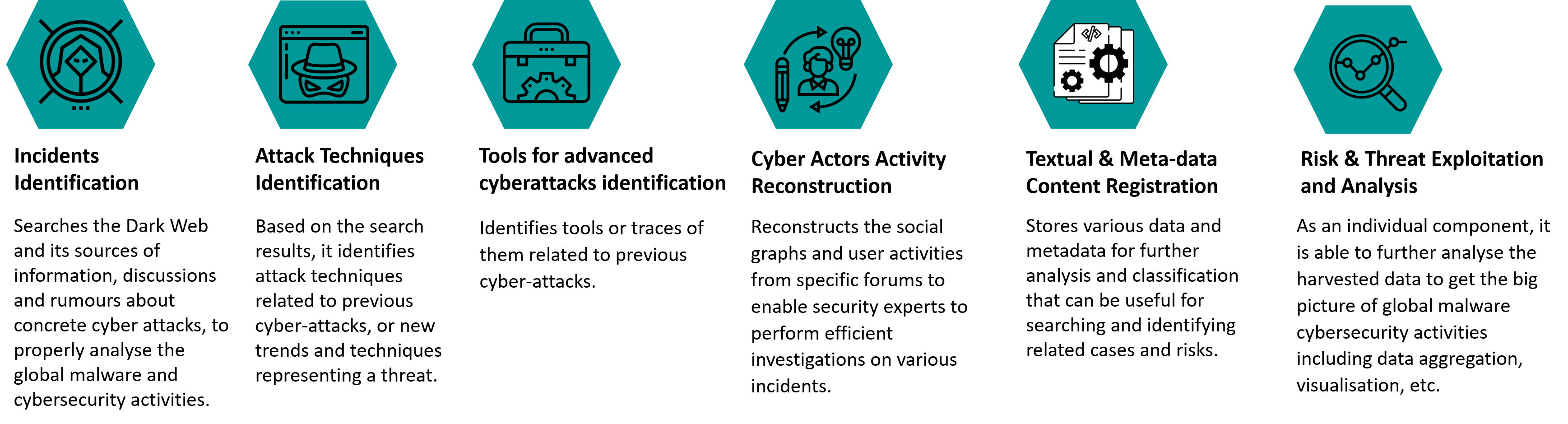
Threats on Deep and Dark Web
Here are some threats that users can come across during browsing:
Malicious Software or Malware
Malware is fully active across the dark web and is often distributed to specific portals as a tool to conduct a cyberattack. But its presence can also be found lingering on the dark web to infect unsuspecting users. They can be exposed to different types of malwares like:
- Ransomware
- Botnet malware
- Phishing malware
- Keyloggers
Users are more prone to be singled out and the target of cyber-attacks if they are browsing the dark web. These threats due to online browsing can even exploit your computer and network connections. Any online activity of the user can serve the purpose of breadcrumbs and carry it to the threat actor if they decide to dig further into the user’s identity.
Source: Cyber Sane
Monitored by the Government
The content on the dark web is often deemed illegal and is not safe for browsing. Previously, the government took over several Tor-based websites, and users may become the government’s target by visiting those websites. In addition, there was an illegal drug market on the dark web known as the Silk Road, which was hijacked previously for police surveillance. Government personnel uses custom software applications to infiltrate and observe the activities to discover and identify the users and bystanders. As a result, users’ risk being monitored by government officials if they browse such websites as they come under scrutiny. In some countries, not adhering to government restrictions and exploring new ideologies is a punishable crime.
Scams
Reports have suggested various tempting offers for illegal services like paid assassinations, trafficking, illicit weapons, drugs, and more to scam the willing users and make money from them. In addition, some scammers are taking advantage of the dark web’s reputation to scam people for a large sum of money or even steal their identity and personal information.
Threats to Businesses
Threat actors can communicate quickly on the dark web without fear of interception. They can also share new technologies and practices to jeopardize business and their network. Here are two examples of threats that organizations may have come across:
- Gift Card Fraud: It is a prevalent scam among threat actors, and the gift card market is a prime example of how dark web data can severely affect businesses. The gift card information can be sold on the dark web, which impacts the brand value and undermines the gift card’s value. For example, in 2017, Amazon was targeted by threat actors operating from the dark web. They gained access to the third-party seller accounts before distributing data on the dark web. The seller accounts lost more than $100,000 of revenue as the hackers modified the seller’s accounts to direct the money to the hacker’s-controlled bank account.
- Credit Card Fraud: It is also one of the common frauds on the dark web as the threat actors can easily exchange sensitive card details before law enforcement can intervene. However, it creates risks for businesses due to fraudulent card use.
Organized Attacks Targeting Businesses
Various criminal groups use HaaS (Hacking as a Service) to freely distribute multiple malicious software and tools to other hackers to target businesses. Hackers could steal sensitive data and demand ransom in exchange for the information or cripple the organization so they cannot carry out any operations.
Source: Comparitech
How Can Varutra Protect Against Dark Web Threats?
There are chances that the user’s personal information is exposed on the dark web while browsing it. In such a scenario, users can seek assistance from cybersecurity organizations that will help in protecting the data. Varutra offers Deep & Dark Web Analysis to identify the organization’s sensitive data and other corporate data that may be exposed over the deep and dark web. We follow the extensive Open-Source Intelligence (OSINT) to collect the data scattered over the Deep and Dark web. This methodology helps access the leaked data and helps mitigate probable outcomes of a breach.
Want us to cyber-protect you against various dark web threats? We are an email away: connect@nullinfosharesystems.com.
Reference:
Kaspersky
Crowdstrike
Heimdal Security
Tulane University
Stratix Systems
Siteefy
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Private Limited




