Zero Knowledge Proof

Introduction
Looking for something exciting and a secure way to protect your secrets? Zero Knowledge Proof Protocol has the potential to increase privacy and security in the applications.
Definitions
Zero Knowledge Proof Protocol is an encryption technique used to prove that you know something without disclosing any information about it. For example, suppose you have a box with some goods in it but you can actually tell what is inside the box by using some secret key or a message.
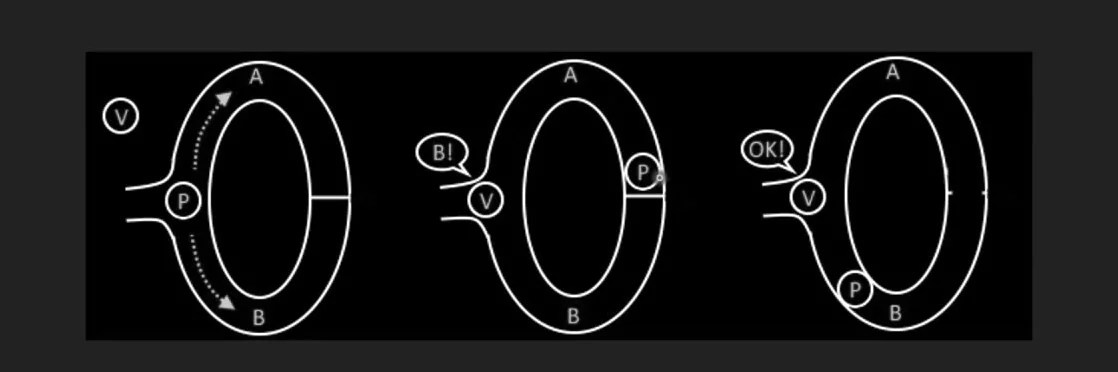
Fig: 1.0 Basic Example
In the above-given diagram i.e. Fig (1.0) two people are involved; Verifier(V) and Prover(P). So, in this image, Verifier asks prover to go around the circle and unlock the key which is in the middle of the circle. A prover will only be able to unlock the key if he knows the secret, so the prover can go around from any point ‘A’ or ‘B’. This process will continue until the verifier does not get satisfied that the legitimate user is making the request.
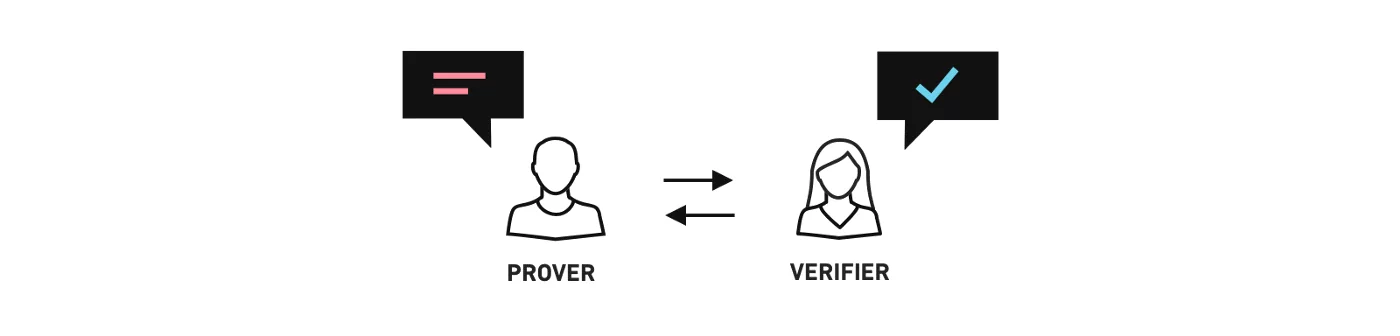
Fig: 1.1 Client & Server Authentication
There are three requirements that must meet the acknowledgment:
- Completeness: If the trusted party is legitimate, ZKP will always return ‘TRUE’
- Soundness: If an attacker is trying to impersonate, it is not possible to trick ZKP
- Privacy: An attacker cannot try to trick the verifier
Think about how authentication method works, it works in either of the following ways:
- Public-key based authentication – it is based on asymmetric cryptography requires parties to exchange public keys (a chain of trust)
- Zero-knowledge proof – this doesn’t require a key exchange, doesn’t leak password. Allows to derive temporary keys for secret key transport encryption
How secret leakage can be prevented:
- Protecting authentication database: Encrypt the secret storage and restrict the database access
- Indirect secret storage: To make it more difficult for an attacker, verifier should escape storing secret itself but store one-time reproducible secret (i.e. salted hash values) a unique value for each and every prover.
Why Zero Knowledge Proof?
Imagine that the verifier itself is an attacker or the verifier is replaced by an attacker, the prover is a common user and does not know about anything, the prover will obviously give what the verifier wants which can lead to fraudulent authentication.
Now here is the advantage of ZKP, which enables two parties to check if they share the same secret without exposing it.
Working of Zero Knowledge Proof Protocol:
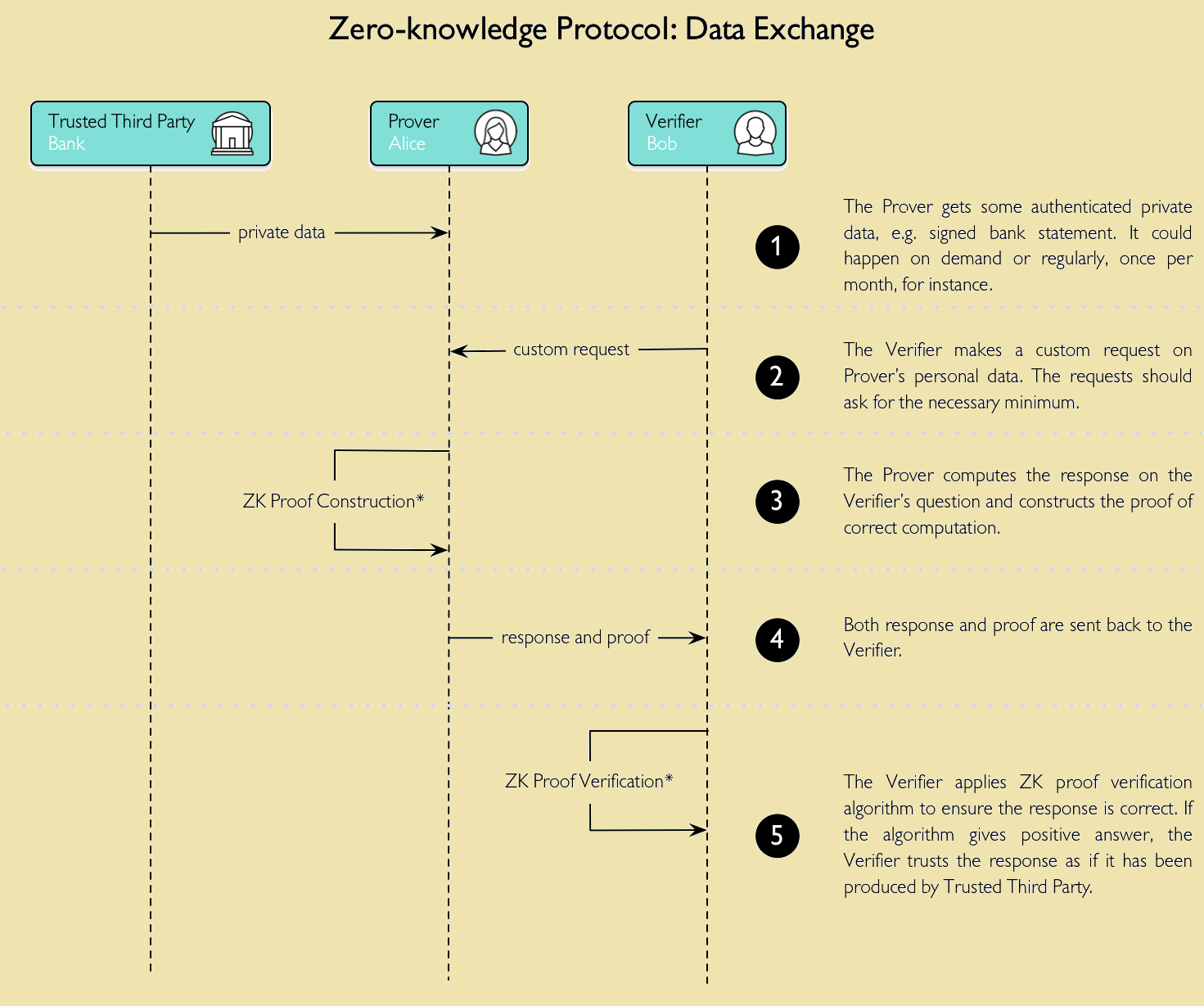
Interactive Zero-Knowledge Proof
In this, the verifier asks frequent questions about the knowledge which the prover possess and it takes place as shown in the below diagram.
Fig: 1.2 Interactive Zero-Knowledge Proof
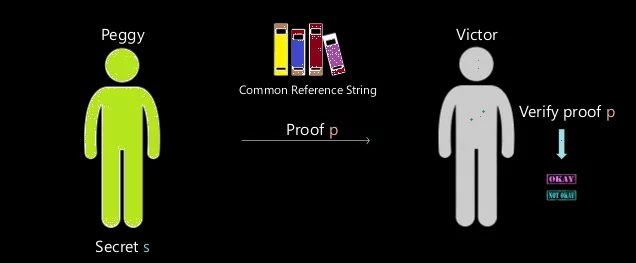
Non-interactive Zero-Knowledge Proof
As the name implies, this does not require an interactive process, as it avoids the possibility of the collision but may require additional machines and programs.
Fig: 1.3 Non-interactive Zero-Knowledge Proof
Conclusion
At last, we can conclude that we can implement Zero-Knowledge Protocol over other authentication methods as it is more secure and provides authentication on the server as well as on the client side. Also, if ZKP is implemented for authentication, the passwords will not be exchanged which means that they cannot be stolen and thereby provides a secure medium of communication.
Author,
Neelam Verma
Attack & PenTest Team
Varutra Consulting