How to Simplify Security with Cybersecurity Mesh Architecture (CSMA)?
Due to the trend of digital acceleration and different workforce options (hybrid and work from anywhere), and the fact that so many employees are now operating outside the company, the traditional network infrastructure is now a thing of the past. This transformation has given the employees flexibility and increased the complexity of securing the extended attack surface. As per the Gartner Cybersecurity Mesh report, there has been a significant rise in the attack surface due to remote work. Virtual networks, employees, IoT devices, edge computing technologies, and other aspects of digital transformation require a flexible security strategy. The only solution for this problem is integrated, broad, and automated CSMA (Cybersecurity Mesh Architecture).
What is Cybersecurity Mesh?
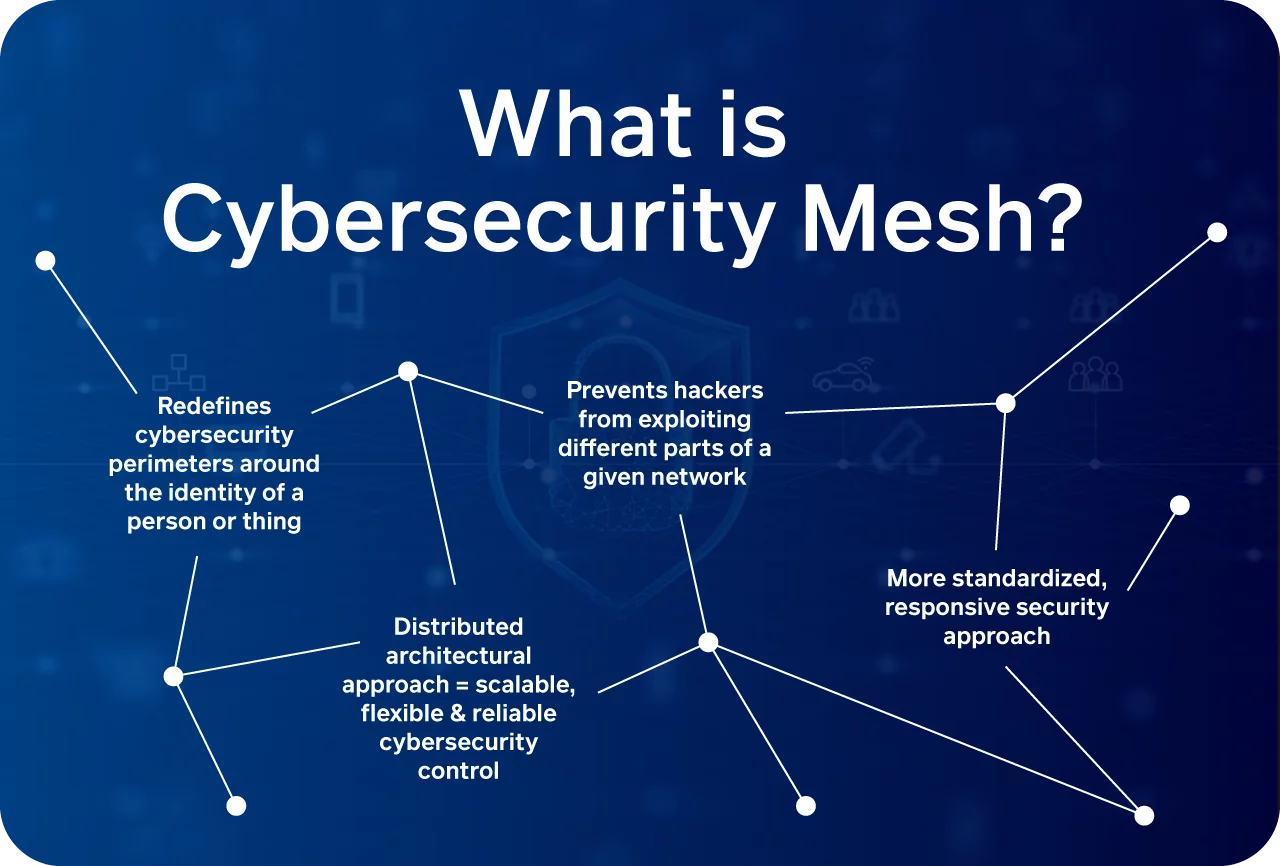
A simple definition for cybersecurity mesh is a scalable and composable approach toward extending security controls to its other distributed assets. Its flexibility makes it suitable for the modern practice of multi-cloud architecture, which is necessary for hybrid and works from anywhere work modules. Cybersecurity mesh architecture enables a resilient and flexible secure environment. It allows the tools that integrate with multiple supportive layers like security intelligence, policy management, and more.
(Source: Stefanini)
What is CSMA (Cybersecurity Mesh Architecture)?
Security silos are one of the most significant security challenges that an organization comes across. Unfortunately, companies seldom deploy various point security solutions to address particular security vulnerabilities or risks. As a result, security infrastructure becomes intricate and challenging to manage and monitor, leading to missed detections and delayed responses.
CSMA is designed to make scalable and composable security. It is done by modularizing security objectives and enabling them to integrate through multiple layers. CSMA’s flexible and collaborative approach helps the organization gain a better security posture with limited resources. This security approach is well-suited for hybrid, work from anywhere, and multi-cloud environments.
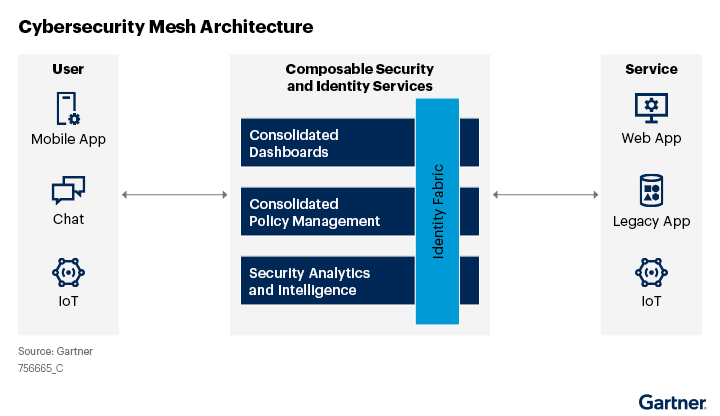
Understanding the Cybersecurity Mesh Architecture (CSMA) Foundational Layers
The CSMA’s foundational layers describe multiple security solutions’ core security goals and functionalities.
Security Analytics and Intelligence
The function of this layer focuses on compiling, aggregating, and analyzing the security data from different security applications and tools. Based on the collected data, solutions like SIEM (security information and event management) and SOAR (security orchestration automation and response) tools analyze the potential threats and prompt suitable threat responses.
Distributed Identity Fabric
The main focus of this layer is to provide the identity and access management services essential to a zero-trust security approach. The functionalities include directory services, decentralized identity management, entitlement management, identity proofing, and adaptive access.
Consolidated Policy and Posture Management
Managing and integrating constant security policies across multiple environments requires translating policies for various ecosystems. In this layer, the solution converts the approaches into the rules and configuration settings needed for a specific ecosystem or tool and can provide a dynamic runtime authorization service.
Consolidated Dashboards
An array of distinct and disconnected security solutions delays security operations by forcefully injecting context switches between different dashboards. The function of this layer is to provide the integrated visibility of the organization’s entire security infrastructure, investigation, efficient detection, and security incident responses.
Benefits of Cybersecurity Mesh Architecture (CSMA)
Here are the benefits of integrating CSMA into the organization:
- Smart Security Designs: It helps the organization design a segregated security infrastructure and deploy solutions based on the foundational layers.
- Constant Security: CSMA helps achieve security consistently by defining the organization’s infrastructure, whether it is expanding or evolving.
- Scalability and Flexibility: CSMA is designed in such a way that it extends its security solutions to the new infrastructure as well. It provides corporate security and evenly distributes it among the organization’s IT infrastructure.
- Improved Collaborations: Cybersecurity mesh architecture enhances the collaboration between multiple security solutions in the organization. It improves detection, response, and threat prevention effectiveness and speed.
- Simplified Management and Deployment: CSMA creates a basic architecture for deploying security solutions in the organization. It also helps make the procedure faster and helps in configuring the new keys. Also, the adaptability and flexibility of the CSMA allow it to evolve to meet the changes in the company and growing security needs.
- Improved Efficiency: CSMA integrates the enterprise’s security infrastructure and eliminates the requirement for additional security personnel to operate and switch context between multiple tools. It helps them deploy efficiently, frees up the extra time and resources, assists in configuration, and more.
Conclusion
With the rapid security changes in infrastructure, the current approach to identifying and providing proper security is insufficient. Therefore, CSMA is designed to provide a simple integrated security architecture and posture to secure the total assets irrespective of location. It is the only solution that works together positively to effectively improve the complete security posture by controlling how tools integrate. In addition, the cybersecurity mesh architecture’s distributed identity fabric provides trusted access to the organization’s workforce, business partners, and clients.
Reference:
Gartner
Fortinet
Checkpoint
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Private Limited




