The Rise of Phishing Attacks during the COVID-19 Pandemic

Cyberattacks are increasing in number every day due to the widespread use of mobile devices and the Internet. As data is considered a valuable asset for organizations, it needs to be secured to avoid any business loss. Phishing attacks are prominently used to steal data of individuals and organizations and harm them.
What is Phishing?
Phishing is a kind of social engineering attack where the aim of the attacker is to steal user information such as login credentials, personal details, financial information, etc., by impersonating a trusted entity (organization or user). The attacker targets a user by sending them an email, SMS, or making a call that seems to be from a known entity asking for personal information. Personal information can be anything, including credit card details, bank details, and other private information.
Attackers use phishing to target both individuals as well as businesses. When targeting individuals, attackers use phishing to extract personal information to make unauthorized purchases, steal money, and perform identity theft. While targeting big corporate and government organizations, they use phishing to gain a foothold in the corporate networks as part of a bigger attack. The main aim of attacking organizations is to make them suffer financial losses, reputation loss, and loss of customer trust.
Phishing Attacks during the COVID-19 Pandemic
Attackers use phishing as their favorite tool to get sensitive information from organizations and individuals for their personal gains. Due to the COVID-19 pandemic, organizations around the world are allowing their employees to work from home in order to ensure business continuity. Working remotely has changed the way we work and made us rely more on emails, phone calls, and online communication platforms like Zoom, Skype, Google Meet, etc. This has increased the opportunities for attackers to trick users into their phishing trap. According to FBI, phishing attacks have increased 110% in 2020 when compared to 2019 and the percentage is anticipated to increase over time, as illustrated in the graph below.
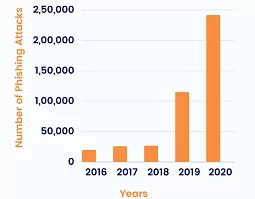
Phishing attacks over the past years
https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf)
Cyber fraudsters are exploiting the opportunity of teleworking and the extraordinary reliance on emails for official and personal communication. In this pandemic, attackers are targeting employees in the name of spreading awareness regarding COVID-19 to trick them into giving their personal information or clicking on malicious URLs or attachments, thereby downloading malware on their systems unknowingly.
How do these fraudsters make people download or click on malicious links inside phishing mails? Well, they trick users by impersonating government organizations, centers for public health, important private institutions, etc. They do so to win the trust of the target users to make them a victim of phishing. To make their emails genuine, attackers even use the branding and logos of well-known organizations.
As per the latest Phishing and Fraud Report of F5 labs, phishing incidents have increased 220% during the peak of the pandemic compared to the average incidents in a year. In the present scenario, it is estimated that this figure will increase as employees are still teleworking and not aware of the latest methods of phishing used by attackers. The main objectives of phishing attacks during the pandemic were found as credential harvesting, fraudulent donations in the name of charity, and malware delivery.
How do attackers perform Phishing Attacks?
Attackers send phishing emails containing malicious attachments or links to target users by pretending to be some trusted entity. Most users open the emails considering them genuine and from a trusted source. When a user clicks on the malicious links or attachments, they are either prompted to some webpage where they are asked for their personal information, or some malware gets downloaded on their systems. The downloaded malware will help the attackers to take control of the victim’s computer, access their personal and financial information present on the system, and log their keystrokes. Stealing of sensitive information of users helps attackers to perform identity theft. Similarly, cybercriminals use phone calls and messaging apps to lure people to provide their personal information. Using their personal information, the attackers can plan further attacks.
Types of Phishing and their Identification
Though phishing is of many types, some important and most common phishing attacks that were used by attackers during the pandemic are:
- Email Phishing
Email phishing is one of the most popular social engineering attacks that attackers use to target random organizations and individuals. Attackers keep the email content so natural that users who read it feel that it looks legitimate. They even use deceptive domain names that look similar to some highly trusted entity (companies, educational institutions, etc.) to gain the trust of their target users. These emails contain either malicious attachments or links. Attackers create email content in such a way that it lures the users to click on malicious links or attachments.
Malicious links inside the phishing emails redirect the user to some website that is created to steal the user’s personal information (login credentials and personally identifiable information, including bank details, credit/debit card details, etc.). When the user clicks on the malicious attachment, malware gets downloaded on their system that helps attackers to exfiltrate sensitive information, log keystrokes, encrypt information, etc.
How to identify Email Phishing?
Carefully follow the following points to identify email phishing attempts:
- Check the sender’s email address and contact information.
- Never click on shortened links as they are used to bypass Secure Email Gateways.
- Ignore emails containing little text with a large image because the image may hide malicious code.
- Check the brand logos carefully because attackers usually fake brand logos to fool users.
- Check and delete an email received from an unknown source if it contains any code.
Discover more about email phishing at our Security Advisory – Email Phishing blog.
- Spear Phishing
It is a kind of email phishing where attackers target specific individuals or organizations. It is a more targeted attack where the attackers know about the target users. Attackers gather information of target users via various freely available sources like social media, magazines, internet forums, and a company’s official website. Once they gather information, they target specific individuals working in the organization using real names, job roles, or the official phone number to make the target user think that the email is from some employee working in the same organization, thereby making the user perform the action mentioned in the phishing mail.
How to identify Spear Phishing?
Carefully follow the following points to identify spear-phishing attempts:
- Beware of abnormal requests from individuals working in other departments.
- Be cautious with shared document links (e.g., Google Suite, Dropbox, and Office 365) as these links can land you on a malicious website.
- Exercise caution while accessing documents that require your credentials to open because it can be an attempt to steal your credentials.
- Whaling/CEO Fraud
Like spear phishing, whaling is a type of corporate phishing where attackers use open-source intelligence to target users (employees). In this phishing attack, an attacker uses corporate sources (company’s website, official social media pages, etc.) of an organization to gain information about its senior leadership member or the CEO. After getting the information, the attacker sends emails to employees working inside the organization by impersonating the CEO via a similar email address. In whaling attacks, also known as CEO fraud, the attacker might ask for money or make the recipient download malicious documents for review.
How to identify Whaling?
Carefully follow the following points to identify whaling attempts:
- Be cautious if you receive any abnormal request from the senior leadership member for the first time, asking you to take some urgent action.
- Ensure the email is received on your official email address, not on your personal email address.
- Vishing
Vishing refers to voice phishing. It is a form of phishing where attackers call the target individuals on their phones and create an emergency-like situation to make them do the requested action against their own interest. Attackers usually perform voice phishing or vishing during busy or stressful times. For example, an attacker can fool an individual by pretending to be from the internal revenue service (IRS), asking for their social security number in the name of some audit during the tax season. It is more likely that the person would provide the requested information to the attacker in such a situation.
How to identify Vishing?
Check for the following points to identify vishing attempts:
- Check the caller number to find out if it exists in the caller blacklist or from an unusual location.
- Vishing calls are usually made during some specific season or event that is stressful.
- Be wary when the caller asks you for unusual information.
- Smishing
It is a type of phishing that involves sending malicious text messages that contain links that download malware on target devices. Attackers send a text message to their target user demanding some urgent action by clicking the link present in the message. Upon clicking the link, malware gets downloaded on the user’s device to perform malicious actions like data exfiltration.
How to identify Smishing?
Check for the following points to detect smishing attempts:
- If you receive any text message from an abnormal area code (initial code of the contact), be careful before taking any suggested action or responding to the message. Attackers normally use international codes to perform smishing.
- Any text message that asks for taking immediate action to change a delivery status, asks for personal information, asks to update social security details, etc.
How to Prevent Phishing Attacks?
Though preventing phishing altogether is not possible, organizations need to ensure that they take sufficient security measures to minimize the chances where phishing attempts become successful. They need to consider the following security measures to ensure they are safe from phishing attacks:
- Train your staff: Train your staff to keep corporate and personal information secure. Also, educate them on various types of phishing attacks that are commonly used and how to stay away from the phishing traps.
- Use email filters: Use email filters to identify spam emails and emails that contain malicious attachments or links.
- Limit access to the Internet: Mitigate the risk of malicious websites by limiting access to the Internet via access control lists (ACLs) on your network.
- Install website alerts in browsers: Ensure that your browser alerts you about potentially risky websites while browsing to avoid any potential harm.
- Use MFA: Implement Multifactor Authentication for your employees to keep their accounts and your network secure. Even if attackers are successful in stealing the credentials of your employees, they cannot perform any malicious action.
- Regularly install security patch updates: Phishing attacks typically exploit common vulnerabilities, so regularly install security patch updates to mitigate the risk.
- Take data backup regularly: To stay safe from the risk of ransomware (malware) due to phishing attacks, it is essential to take data backups periodically.
Conclusion
With the increasing number of phishing attacks, organizations must exercise more caution and be prepared for defending against phishing attack attempts on their networks via their employees working remotely. The points discussed in this article help organizations and individuals to be aware of modern types of phishing attacks and how to identify them. The most important weapon against phishing attacks is identifying or diagnosing them before they harm you. Reach out to us for our highly effective Phishing Diagnostic Services to secure your corporate networks from various types of phishing attacks.
References
https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf
https://securityscorecard.com/blog/types-of-phishing-attacks-and-how-to-identify-them
Author,
Mustafa Ahmed,
Marketing Department,
Varutra Consulting Pvt. Ltd.