5 Concerning Cyberattacks to Watch Out for in 2022

Introduction
Technologies are evolving continuously, and we are primarily dependent on them. They make our day-to-day life easier, but they are also more prone to cybersecurity threats. These cyberattacks are not only compromising confidential information but also lead to severe, devastating effects on any organization. COVID 19 pandemic has rapidly accelerated the digital transformation of organizations due to remote working, which has also increased new & sophisticated cyber threats. It is likely said that 2022 will see many sophisticated cyberattacks. Organizations encounter several security gaps due to complexity and lack of visibility, making them vulnerable to cybersecurity risks.
5 Concerning Cyberattacks to Watch Out for in 2022
Here are some essential data about 2021 cybersecurity statistics to help keep 2022 secure from any cybersecurity threat.
- While executing zero-trust implementations, security gaps are experienced by nearly 50% of organizations.
- Increase in ransomware attacks between July 2020 and July 2021.
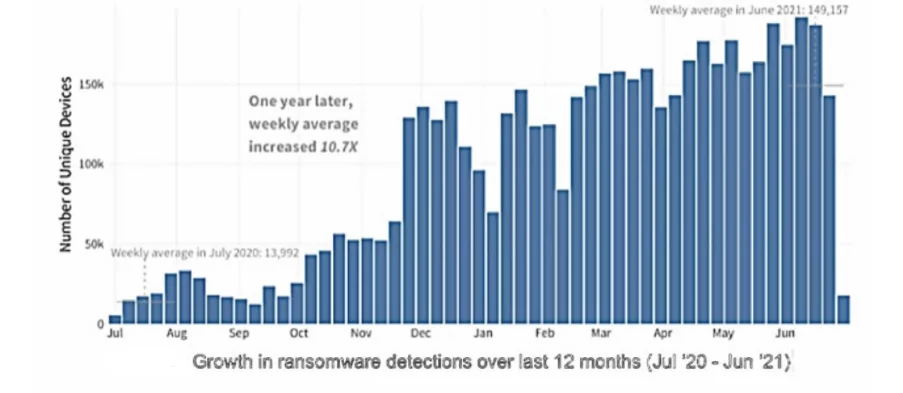
Figure 1: Ransomware threat (cyberattack) detections from July 2020 to July 2021 (Source)
- Organizations have experienced a notable percentage of operational attacks (OT) that have affected productivity and endangered the employee’s security.
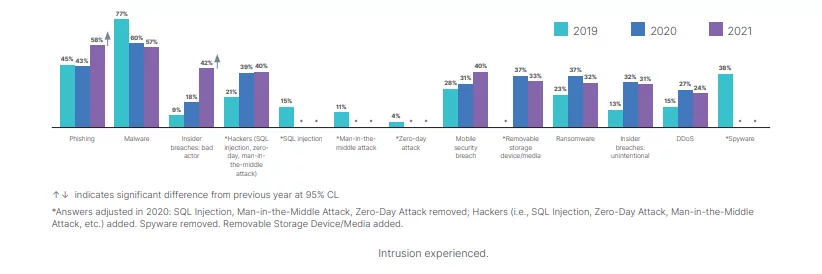
Figure 2: Intrusion experienced from 2019 to 2021 (Source)
Organizations take several measures to counter such attacks, but they still can’t guarantee 100% security. Therefore, it is better to be prepared against emerging cyber threats to minimize cybersecurity risks. While no one can predict the future, here are 5 upcoming threats that are a topic of concern in 2022.
Linux Attacks
Linux is primarily used in back-end systems for profuse networks. It is considered a container-based solution for mission-critical software and IoT applications. Therefore, it is becoming a hacker’s favorite target. Several organizations are mainly prepared for preventing Windows attacks, but they are not accustomed to tackling attacks on Linux. They are basically oblivious to securing Linux-based applications from any defensive and malware threats compared to Windows. This scenario can be a lot more worsen if the Linux system has sensitive information like certificates, Secure Socket Shell (SSH) credentials, application usernames, and passwords.
The modern attacks are very effective and efficient in targeting Linux systems. For instance, the Beacon feature in Cobalt strike, known as Vermilion Strike, can successfully target Linux applications by simple remote access without getting detected. Likewise, a recent Log4J vulnerability is one of the prime examples of a recent cyber-attack where Linux binaries capitalize on the opportunity.
Satellite Network Attacks
People are not connected through the internet, which means that there is a substantial rise in the usage of the satellite network. It means there is a strong possibility of new threats targeting satellite networks. In this scenario, the large enterprises mainly rely on satellite networks will be hackers’ targets. In addition, companies that support low-latency activities like online gaming or providing services to remote locations will be the potential target of such malicious attackers.
Threat to Crypto Wallets
Hackers are now targeting these crypto wallets with the rise in bitcoins and other cryptocurrencies. They are constantly working on developing new and sophisticated malware. Attackers target crypto wallets containing sensitive information like bitcoin address, bitcoin private key, crypto wallet address, and other private information. By targeting this information, they can empty the wallet.
Attackers often begin by creating a phishing campaign with a basic strategy of attaching a malicious file. This malicious file is designed to infect the victim’s system and steal the crypto wallet’s sensitive information like credentials from their system. There are other means to steal the credentials, such as using a fake Amazon gift card generator to replace the victim’s wallet with the attacker or remote access trojan (RAT). This attack uses social engineering to target the cryptocurrency and has the competence to accomplish keylogging, uploading & downloading files, executing commands, and taking screenshots.
Targeting OT Systems
Nowadays, ransomware attacks are prevalent and are targeting critical infrastructure. These incidents are often described as “killware.” These attacks target hospitals, water treatment plants, pipelines, and other critical infrastructure. They don’t directly target human lives, but these malware attacks disrupt the infrastructures’ smooth functioning and indirectly impact the people.
Cyber-criminals are also evolving and getting confident in carrying out attacks. They are now moving from personal attacks to more prominent and public attacks that have more impact, like supply chain and large-scale attacks with several human victims. Due to the near-universal convergence of IT and OT networks, attackers find it easier to access OT systems by compromising the home networks and applications. There is also a significant risk of ICS and SCADA systems. Now attackers don’t need exceptional technical knowledge to exploit the vulnerabilities as they can purchase the attack kits on the dark web.
Cyberattacks on the Edge
The COVID-19 Pandemic has compelled people to work from home. It means that the corporate network is threatened due to the residential network. It means that there is a rise in network edges as threats (type: living off the land) can remain hidden due to the large vicinity. In this technique, cyber-criminals can use the previously designed malware using the existing applications and stay hidden in the system. They can then carry out the attacks and data exfiltration like a regular activity without getting detected. Living off the land attacks can be combined with edge access trojans (EATs) and create a new attack that will live off the edge along with the land. This malware can avoid getting detected and use local resources to monitor the activities and data edge to steal, hijack or demand ransom for information, critical systems, and applications.
Conclusion
Cybersecurity threats are rapidly rising due to digitalization. It means one has to look out for its countermeasures and be aware of various terms of cybersecurity and its repercussion. By getting conscious of cybersecurity issues, one can reduce its risks and after-effects. To prepare for 2022, the organization needs to harden the security measures for Linux and Windows operating systems. Also, while integrating new technology, the organizations need to ensure their security, whether the network is secure. For example, check whether the satellite-based connectivity is safe before establishing the connection. It is also essential to keep in mind that we are combating new and prevailing threats.
Reference
https://pecb.com/article/top-5-types-of-security-threats-to-look-out-for-in-2022
https://www.crn.in/columns/5-cybersecurity-threats-to-watch-out-for-in-2022/
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




