Planning Your Cybersecurity Budget For 2022

Cyber threats and risks are a topic of global concern now. Everyone is looking for the best solutions to protect themselves against these arising cybersecurity problems. Organizations need to build the right strategies to overcome this cybersecurity challenge; otherwise, nothing can save them from this upcoming catastrophe. However, countless organizations are still hesitant to manage their cybersecurity budget effectively and efficiently to address their security needs successfully.
It was reported that 66% of cyberattacks occurred in the last year alone, and the frequency of these attacks has increased rapidly. For example, it is estimated that every 11 seconds, a business or a person is a victim of a ransomware attack. Previously it was 40 seconds. This estimate forces us to think about our cybersecurity situation and how to proceed forward while protecting ourselves from them.
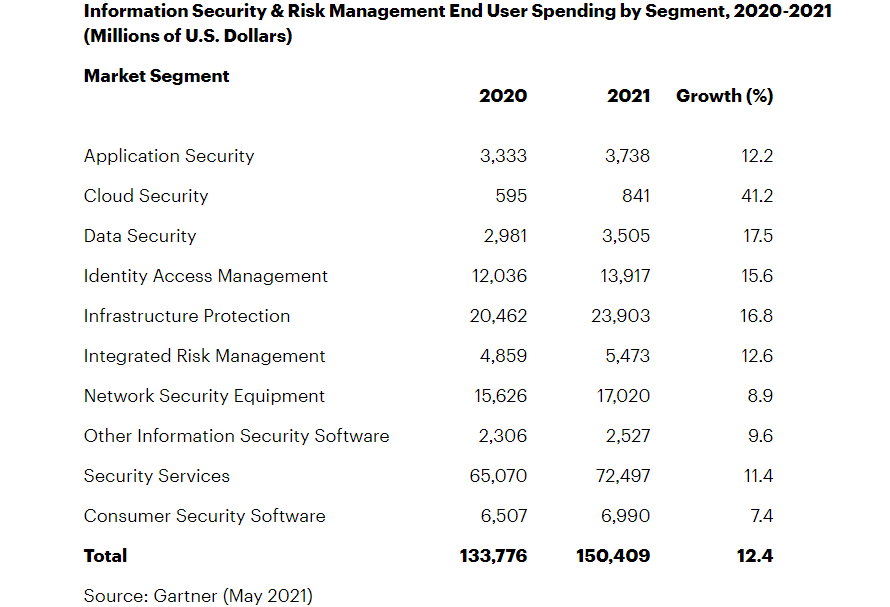
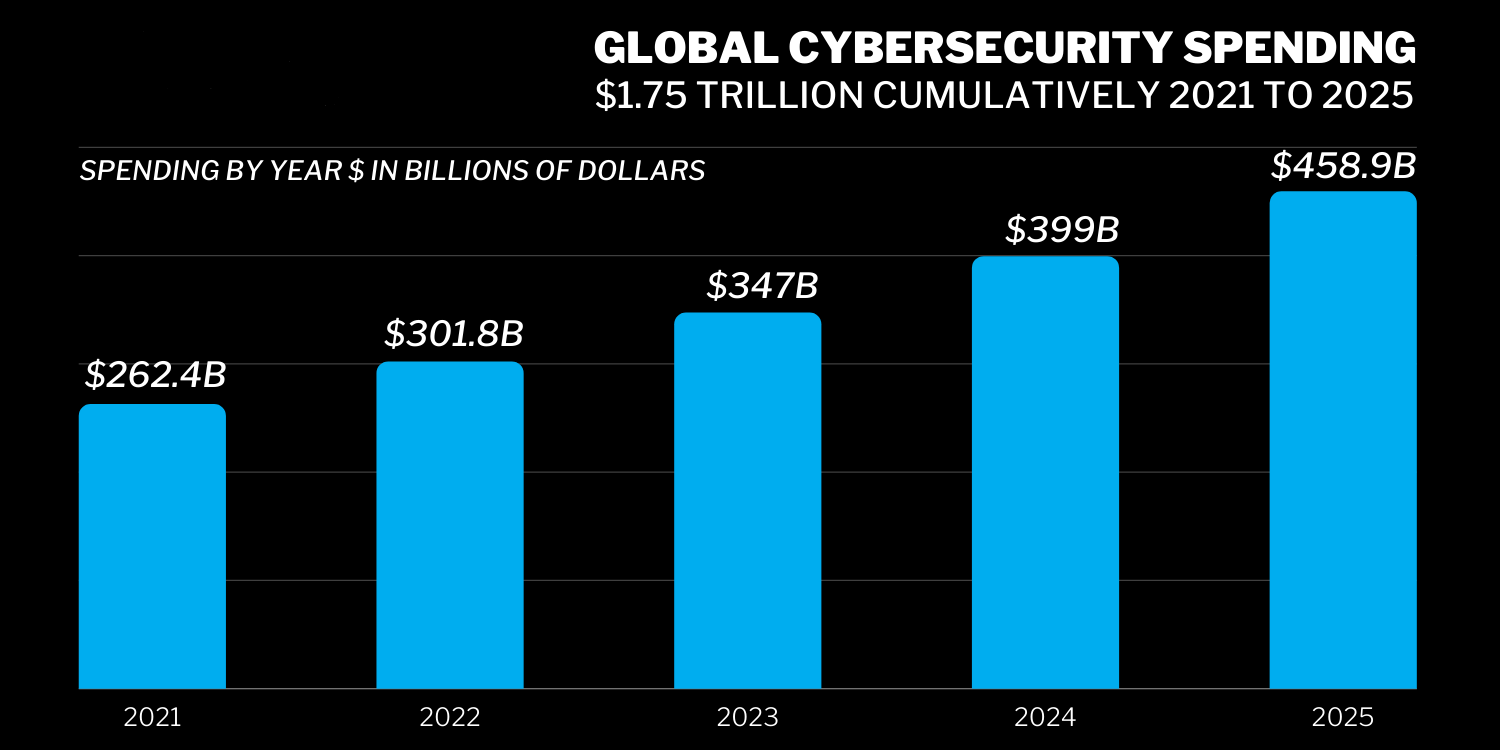
Cybersecurity risks and attacks are continuously evolving and changing. Their frequency has also increased in recent years. It makes it hard for anyone to plan a cybersecurity budget as things are not relatively stable from year to year. In 2021, cybersecurity professionals predicted a 12% rise in worldwide cybersecurity expenditure, roughly around $150 billion. These experts have mixed predictions for 2022 that it can either rise or remain steady, but by 2025, it can increase to approximately $1.75 trillion.
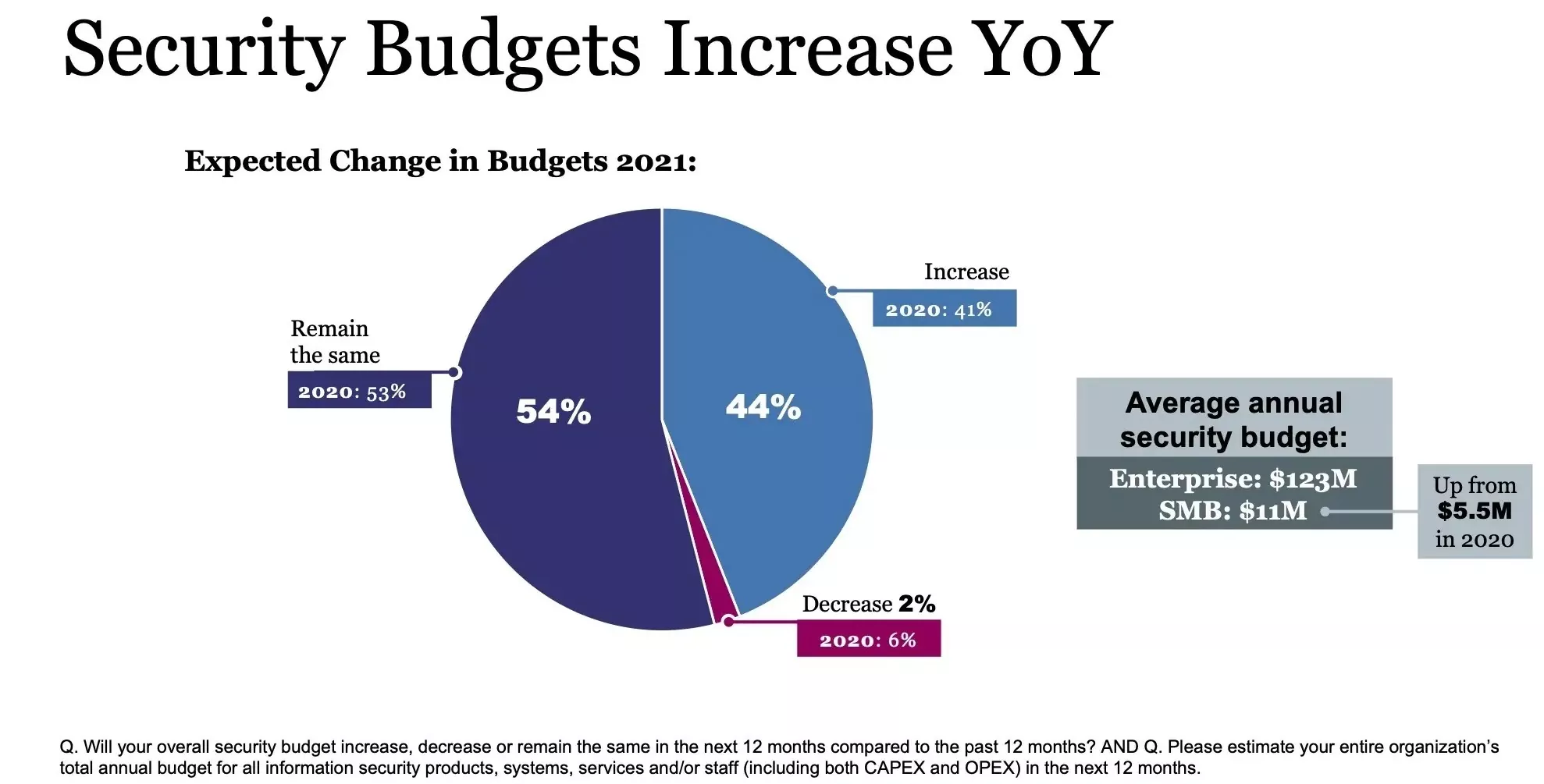
These numbers are essential while planning a 2022 budget for your cybersecurity. You have carefully looked at these numbers and carefully planned how to spend your money to protect your organization’s sensitive information. Planning a budget will help you in maximizing and segregate your expenditure.
How to Plan Your Cybersecurity Budget for 2022?
The following points will help you better prepare the cybersecurity budget for 2022.
Seamless Deployment of MFA
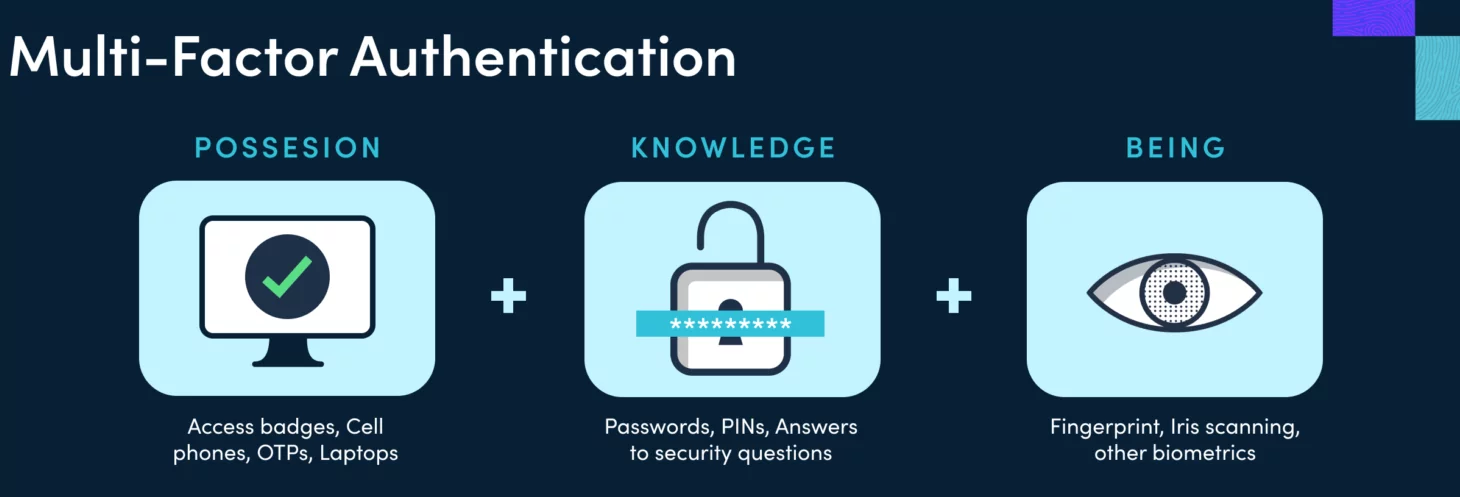
Multifactor Authentication should be considered a priority as it will help you verify the users. There is more than one way of authentication factors, and these are considered to be one of the best security methods as they provide better security for your employees and clients. It is also effective against data breaches. Different authentication elements include:
- Knowledge Factor (Information that only the user is aware of)
- Possession Factor (Item or device that only the user possesses)
- Inherent Factor (Something unique that only the user has, like a permanent or characteristic attribute)
Risk Assessment for Ransomware and Its Mitigation
A ransomware attack is a common and frequent cyber-attack faced by any organization or an individual. The best way to counter and mitigate ransomware attacks is by carrying out risk assessments. It helps identify the vulnerable area and take immediate steps to protect it. In addition, taking assistance of other preventive measures like antivirus software and creating a backup will also come in handy.
Proper Configuration and Cloud Inventory
Nowadays, organizations focus on cloud computing for storage as it is convenient for businesses and people globally. Moreover, it saves time and money, so its demand also increases daily. Therefore, various organizations provide cloud computing assistance like AWS (Amazon Web Services), Salesforce, Microsoft Azure, etc. However, if they are not correctly configured, it can pose a risk for the organization. Furthermore, there can be other security issues like unauthorized access to the cloud, vulnerabilities in security setup, etc. These can be very problematic to the organization and vulnerable to cyber-attacks. In such a case, an organization can seek the assistance of various cloud security services that will help them in mitigating such security risks.
Data Breach Preparation and Supply-Chain Risks
Supply chains are considered the backbone of any organization. It helps in the organization’s growth by adding value to the clients and customers. However, they can be vulnerable to various cybersecurity risks if managed poorly. Therefore, you need to properly carry out your supply chain activities and deal with your partners carefully. In addition, you need to ensure that you have a solid cybersecurity plan that will monitor and detect any malicious activity carried against you to prevent data breaches.
Threat Hunting and Monitoring Activities
It is the age of big data and APTs (Advanced Persistent Threats). Cybercriminals are getting advanced day by day, and it is difficult for an average organization to manage its IT security seamlessly. Threat hunting is considered one of the best cybersecurity means to protect your organization. So, it is necessary to invest in a threat service provider so that they can protect your private and sensitive data from any security breach.
Proper Training and Guidance to the Employees
An organization should also invest in educating and training their employees for proper conduct to prevent them from becoming victims of cyber-attack. They should be updated against the recent threats and risks and response and prevention techniques. It will help them work efficiently and improve your organization’s security posture. We also offer corporate training for the organizations to prepare themselves better to combat any cybersecurity attack.
Designing the Incident Response Plan
With the continuous rise in cybersecurity threats and risks, organizations need to be fully prepared by designing a dynamic incident response plan. It will be your guide in case you encounter a dire cybersecurity threat. You will know how to act and what to do in such a situation. This action will help you provide essential guidance to protect your data until the outside help arrives.
Penetration Testing and Vulnerability Assessment
An organization must always upgrade its software and keep its systems updated with the latest security patches and updates. But sometimes people forget to do it on time due to multiple reasons. Therefore, it is recommended that they opt for penetration testing and vulnerability assessment for situations. They will assist the organization by identifying any potential vulnerability that a hacker can exploit and help them in mitigating it.
Conclusion
These are some top areas where an organization can focus on planning its cybersecurity budget to solidify its security in 2022. They need to invest in the right strategy and technology to stay ahead of these cybersecurity criminals and hackers. They can also seek the assistance of various cybersecurity organizations for security assistance. Varutra offers multiple security services to help the organization cater to its cybersecurity needs.
Reference:
https://www.dataprise.com/resources/blog/2022-cybersecurity-spending
https://cybersecurityventures.com/cybersecurity-spending-2021-2025
Author,
Sanjana Yadav,
Marketing Department,
Varutra Consulting Pvt. Ltd.




