Threat Advisory Report on WannaCry Ransomware (Critical Severity)
Here we will discuss Threat Advisory Report on WannaCry Ransomware (Critical Severity). 1. Introduction On Friday, May 12, countless organizations around the world began fending…
How To Develop Secure Software – Action Plan To Make Secure
The purpose of this article is to help to develop secure software. Easily avoided software defects are a primary cause of commonly exploited software vulnerabilities….
Mobile Vulnerability Database (MVD)
Mobile Vulnerability Database, or MVD, is a unique place to find out about vulnerabilities reported worldwide for Mobile Platforms. Introduction to Mobile Vulnerability Database: The…
Introduction to Secure Software Development Life Cycle
The most effective way to reduce application security risk is to implement a formal development process that includes security best practices to avoid application vulnerabilities….
External Penetration Testing – Case Study
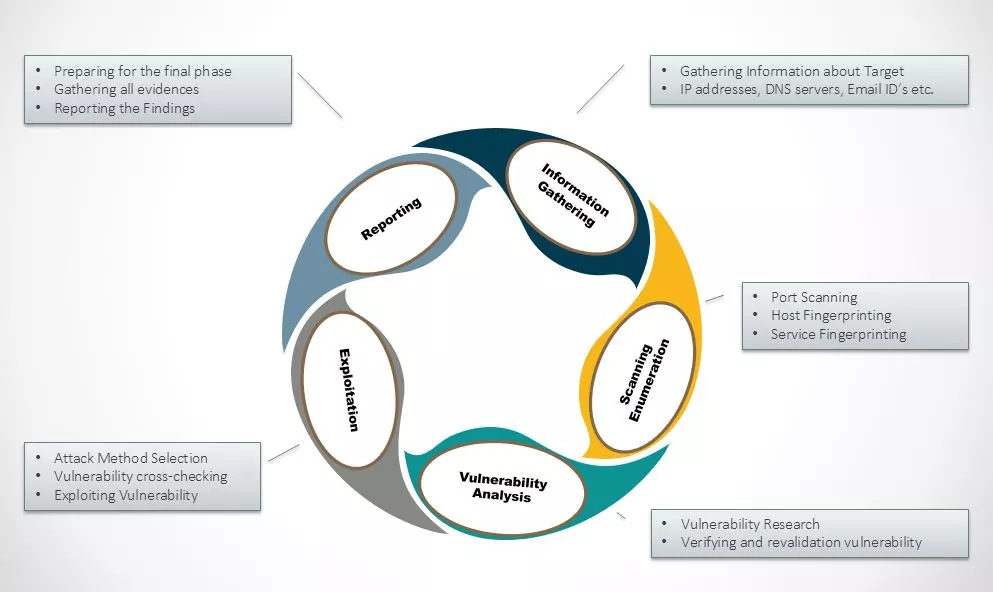
ABSTRACT External Penetration Testing consists of a reviewing and assessing the vulnerabilities that could be exploited by external users/Hacker without any credentials or without having…
Adobe Flash Player Zero Day Attacks Found In Hacking Team Data Leaked
Hacking Team is a Milan-based information technology company that sells offensive intrusion and surveillance capabilities to governments, law enforcement agencies and corporations.Its “Remote Control Systems”…
Shellshock-Security Patching Aftermath
On September 24th 2014, a publicly disclosed vulnerability was revealed in the UNIX/Linux which we have discussed in our blog https://www.varutra.com/blog/?p=1010. Although a patch has…
Shell Shock – The Bash Vulnerability
BASH (Baurne Again Shell) Bash is the shell, or command language interpreter, that will appear in the GNU operating system. Bash is an sh-compatible shell…
Android Malwares – An Overview
Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can…
Malware threatens Android, uses Remote Access Trojan
Android remains at number one Operating System worldwide so also getting targeted by Malware creators. In 2013 about 98 percent of all malware detected were…
Categories
- Android Security (19)
- Application security (1)
- Authentication & Authorization (23)
- Blockchain Security (1)
- Bug Bounty (2)
- BYOD (5)
- Case Study (29)
- Chatbot Security (1)
- Cloud Security (14)
- Containerization Security (1)
- Corporate Training (6)
- Cyber Attack (34)
- Cybersecurity Frameworks and Solutions (3)
- Data Breaches (35)
- Data Leakage (27)
- Data Privacy (29)
- Email Phishing (8)
- Encryption & Cryptography (14)
- Ethical Hacking (19)
- General (42)
- Governance Risk & Compliance (8)
- iOS Security (2)
- IOT Security (7)
- Java Security (2)
- Mobile Application Security (19)
- Mobile Device Management (10)
- Network Pentesting (9)
- News (48)
- Password Security (10)
- Past Events (8)
- Patch Management (3)
- Ransomware Attack (14)
- Reverse Engineering (3)
- Secure SDLC (5)
- Security Advisory (34)
- Security Best Practices (43)
- Security Hardening (38)
- Social Engineering Attack (10)
- Social Networking Security (5)
- Source Code Review (2)
- SPAM (2)
- Student Oriented Courses (2)
- Thick Client Penetration Testing (4)
- Unix/Linux Security (1)
- Upcoming Events (3)
- Viruses & Malware (16)
- VoIP Penetration Testing (4)
- Vulnerability Disclosure (21)
- Web Application Security (34)
- Windows Mobile Security (1)
- Zero Day Attack (8)